Tuesday, November 30, 2021
CONTENT MODERATION: : Evolving Norms In The Governance Of Online Communities
Techdirt Podcast Episode 307: Evolving Norms In The Governance Of Online Communities
from the panel-discussion dept
In last week's episode, we had a conversation with the creators and curators of the Knight Foundation's virtual symposium on Lessons From The First Internet Ages. This week, we've got the audio from the panel discussion at the symposium that Mike participated in along with Stanford's Daphne Keller and Harvard Law's Evelyn Douek, all about the ways that the governance of online communities has evolved and changed as the internet has matured.
Follow the Techdirt Podcast on Soundcloud, subscribe via Apple Podcasts, or grab the RSS feed. You can also keep up with all the latest episodes right here on Techdirt.
Filed Under: daphne keller, evelyn douek, governance, internet, podcast

We see a Techdirt Insider membership in your future...
MAYBE YOU DON'T WANT TO READ OR TO HEAR THIS. . .Air-Borne HazMats
Moderna CEO says vaccines likely no match for Omicron: Live News
The assessment from the head of the vaccine maker comes as Hong Kong and others announce travel curbs.
![<div class=__reading__mode__extracted__imagecaption>Countries around the world have reimposed travel restrictions in response to the new Omicron variant [File: Thomas Peter/Reuters]](https://www.aljazeera.com/wp-content/uploads/2021/11/2021-07-09T123417Z_376355004_RC2YGO98VNKX_RTRMADP_3_HEALTH-CORONAVIRUS-CHINA.jpg?resize=770%2C513)
BLEEP BLEEP BLEEP...Starting off this week Ultimately, our goal is to turn your #$@!* computer that never does what you want into one that you praise as a well-tamed tool.
Bleeping Computer® is an information security and technology news publication created in 2004 by Lawrence Abrams. Millions of visitors come to BleepingComputer.com every month to learn about the latest security threats, technology news, ways to stay protected online, and how to use their computers more efficiently.
For our work in analyzing ransomware, issuing news alerts about the latest security threats, and offering free ransomware decryptors, BleepingComputer is the first news and support site to be added as a partner of the No More Ransom Project. This project was started in 2016 as an alliance between Europol's European Cybercrime Centre, the National High Tech Crime Unit of the Netherlands police, and McAfee to battle ransomware.
In addition to news, we provide a wide array of free technical support services, downloads, and self-education tools that allow users to resolve issues on their computer. Whether you are a novice user here to learn basic concepts about computers or an advanced user infected with ransomware, BleepingComputer can offer solutions to your problem for free.
Ultimately, our goal is to turn your #$@!* computer that never does what you want into one that you praise as a well-tamed tool.
Mission Statement
Our mission: To provide accurate and relevant information about the latest cybsecurity threats and technology advances so you can protect and take control of your network, devices, and data.
Ways to contribute
As part of our mission to help you take control of your data and devices, we always welcome news tips and research that you think our readers would find interesting.
To share a news tip with BleepingComputer, you can our News Tip form to share the information confidentially.
=========================================================================
Since launching in 2004, BleepingComputer has operated under strict guidelines to earn our readers' trust and maintain it, as we provide unbiased reporting about technology and cybersecurity issues.
While disinformation and misinformation campaigns run rampant and copycat publishers abound, BleepingComputer takes pride in our investigative and original reporting regarding a wide variety of topics, including cybersecurity, operating systems, computers, software products, and privacy issues.
To maintain our strict editorial independence and original reporting, BleepingComputer operates under the following guidelines:
- While BleepingComputer generates its revenue from advertising, our partners do not have any influence on our writing.
- BleepingComputer does not sell links on our site or accept compensation to write articles about companies or their products. Any sponsored posts at BleepingComputer will be clearly marked so readers understand that this is paid content or content that we may earn a commission.
- BleepingComputer does not accept payment to conduct reviews or provide a favorable opinion.
- BleepingComputer is commonly provided embargoed research or "tips" but we refuse to accept them with preconditions regarding what is stated in the article.
- BleepingComputer protects the identity of our sources to the fullest extent of the law.
For more detailed information regarding these guidelines, you can read the following sections below.
Sources of information
BleepingComputer relies on different sources of information that we use to craft our articles. These sources include end-users, employees, threat actors, corporate reports, research, press releases, and other publisher's stories.
We also conduct interviews over the phone, messaging apps, emails, and through video conferencing. During phone and video interviews, we may record the conversation to report on the information provided properly. All discussions are considered to be "on the record" unless we are told otherwise, in which case, we will honor that request.
Due to the nature of our reporting on cybersecurity and cyberattacks, we also commonly use sources who wish to remain anonymous for fear of reprisals from employers or threat actors. When working with sources who wish to remain anonymous, BleepingComputer will always protect their identity to the fullest extent of the law.
Regardless of how we attain our information, BleepingComputer will always independently confirm the accuracy of such information through our own tests, in conversations with the related companies, or through other individuals who have demonstrated that they have first-hand knowledge about the topic.
Editorial corrections and updates
Despite making the best efforts to report on a particular topic or news event accurately, we may sometimes get something wrong.
If a mistake is reported to BleepingComputer or we discover it on our own, we will promptly update our content with a correction and provide a statement explaining why we made the change.
While covering a story, there are times that the report may be developing and new information becomes available at a later date. When that occurs, we will update our content and note why BleepingComputer added additional content.
Conference and press event coverage
At times, BleepingComputer writers are invited to conferences to cover new information presented by companies and researchers.
While we may attend these events, BleepingComputer does not promise to cover the topics or product information presented at said events.
Advertising and Sponsored Content
BleepingComputer uses advertising to cover the costs of operating the website and producing our content.
Advertisers will never influence what and how we write about a particular topic or about products and services that we may cover in our content.
BleepingComputer may at times utilize a native advertisement called advertorials, which is an advertisements in the form of editorial content. All advertorial content will clearly be marked as sponsored content or deals and will always contain a disclaimer at the bottom so that readers can identify that there is a commercial incentive for the publishing of the content.
Some of our content may contain marketing links, or affiliate links, that generate commissions from purchases made through those links. Our affiliate partnerships don't influence our editorial content and will only be recommended if they provide a tangible benefit to the visitor. Visitors can find more information on how BleepingComputer uses affiliate links in our 'Affiliate Disclosures' below.
Product Reviews
When writing reviews on this site, BleepingComputer uses the following guidelines:
- When reviewing products, the editors and team members will always provide honest opinions, findings, beliefs, or experiences on the products being reviewed.
- BleepingComputer never accepts compensation to write a review.
- When writing reviews, we sometimes purchase the product ourselves or are given the product by the company. If we are given the product, it will be stated in the review.
- After a review is finished, we will return the item if requested. Otherwise, the reviewed item will be given away as a promotion on BleepingComputer.com.
- Advertisers on our site may also be a company who's product we are reviewing. Their advertising, though, will have no bearing on how we review their product
Affiliate Disclosures
The Federal Trade Commission requires that we disclose any relationship between a product manufacturer or advertiser when we write about a product, service, or recommend a product. BleepingComputer agrees with this policy as it allows you, the reader, to understand the relationships between a site and the various companies and products they promote.
We have outlined our product review standards and the various ways we use affiliate links or earn commissions:
Affiliate Links
BleepingComputer may use links that generate a commission for the site if you use them to purchase a product. In the forums, we use SkimLinks to automatically transform posted links into affiliate links. If you do not wish to view inserted links, you can opt out of this process by going to this URL: http://optout.skimlinks.com/?tested=1.
We may also utilize affiliate links for various products within our Virus Removal Guides, Download section, and Tutorials, and News articles.
Virus Removal Guides
In our Virus Removal section, we offer guides on how to remove various computer infections. These guides may use programs and utilities that generate commissions for the site when you purchase them. We will never, though, promote a product for the sole purpose of generating a commission.
We will only suggest a product that can actually help you remove the computer infection for free, and we will only receive a commission if you decide to purchase it after. If it is required that you purchase a product before you can remove an infection, and we receive a commission for it, we will specifically state this in the guide. The products that we routinely use in our guides and that we receive affiliate commissions from are MalwareBytes, Emsisoft, Zemana, and HitmanPro.
Download Section
All of the programs in our Download section are fully functional and free to use. If you use the product and decide to purchase it, we may earn a commission for the sale, depending on the software.
Tutorial Section
Some tutorials may discuss or require specific hardware or software that contain Amazon affiliate links that will generate a commission for the site if you purchase them.
StackCommerce and the BleepingComputer.com Deals Store
BleepingComputer.com has partnered with StackCommerce to offer our readers deals on a variety of products. If a user chooses to purchase a product through this store, BleepingComputer.com will earn a commission on the sale.
If you have any questions or concerns regarding these policies, please free to contact us here: https://www.bleepingcomputer.com/contact/
=========================================================================
-
This Cyber Monday deal helps prepare for a career in Cyber Security
This training guides you from an introductory security level to the highest certifications in the IT industry. With code CMSAVE70, you can get the 5-course collection today for just $9 during our Cyber Monday sale.
- BleepingComputer Deals
- November 29, 2021
- 02:56 PM
 0
0
-
Dark web market Cannazon shuts down after massive DDoS attack
Cannazon, one of the largest dark web marketplaces for buying marijuana products, shut down last week after suffering a debilitating distributed denial of service attack.
- Bill Toulas
- November 29, 2021
- 01:26 PM
 0
0
-
This portable 4K touchscreen monitor is just $232 for Cyber Monday
Enter the Desklab Portable Touchscreen Monitor — a lightweight 4K display that works with pretty much any device. It's normally priced at $700, but you can get it today for just $231.99 with code CMSAVE20 this Cyber Monday.
- BleepingComputer Deals
- November 29, 2021
- 12:36 PM
 0
0
-
Stealthy WIRTE hackers target governments in the Middle East
A stealthy hacking group named WIRTE has been linked to a government-targeting campaign conducting attacks since at least 2019 using malicious Excel 4.0 macros.
- Bill Toulas
- November 29, 2021
- 11:30 AM
 0
0
Zoom finally adds automatic updates to Windows, macOS clients
Zoom has announced today the launch of an automatic update feature designed to streamline the update process for desktop clients.
- Sergiu Gatlan
- November 29, 2021
- 10:45 AM
 0
0
Telegram channel admins who sold fake vaccine cards arrested
The Italian financial crime agency (Guardia di Finanza - GdF) has announced the arrest of several individuals suspected of managing Telegram channels to promote fake vaccine certificates, aka 'Green Passes.'
- Bill Toulas
- November 29, 2021
- 10:11 AM
 1
1
Panasonic discloses data breach after network hack
Japanese multinational conglomerate Panasonic disclosed a security breach after unknown threat actors gained access to servers on its network this month.
- Sergiu Gatlan
- November 29, 2021
- 09:40 AM
 0
0
The Word CONCERNED...We Do A Lot of That!
Why Omicron quickly became a variant of concern
The WHO lets Omicron skip over variant of interest, go straight to concern.
THAT'S A LOT OF MUTATIONS!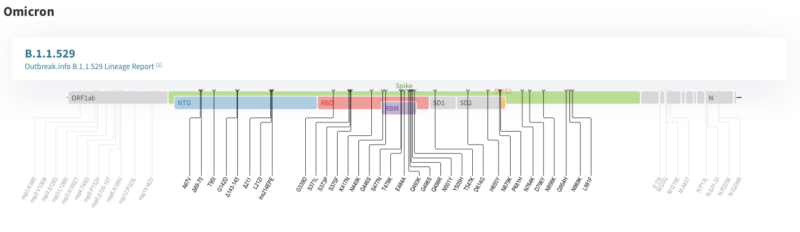
". . .Many changes
While the Delta variant's version of spike has nine changes compared to the virus that started the pandemic, Omicron has 30 differences. While many of these haven't been identified previously, a number of these have been seen in other strains, where they have a variety of effects. These include increasing infectiousness of the virus, as a number of the changes increase the affinity between the spike protein and the protein on human cells that it targets when starting a new infection.
Other changes in the spike occur in areas of the protein that are frequently targeted by antibodies that neutralize the virus. Changes here can mean that an immune response generated to vaccines or earlier versions of the virus are less able to target Omicron.
While these mutations are suggestive, understanding how they and the previously undescribed mutations in Omicron alter its behavior will depend on getting real-world data on its spread. Right now, however, we just don't have much of that.
We are lucky in the sense that it's relatively easy to detect Omicron. According to the WHO, some of the large collection of mutations in the gene that encodes the spike protein interfere with the gene's recognition by common versions of PCR tests. Those tests continue to recognize the presence of the virus by also targeting other areas of the genome. So a PCR test that comes back spike-negative but virus-positive is suggestive of the presence of Omicron, which can then be confirmed by genome sequencing.
These tests have shown Omicron is spreading rapidly within a number of countries in Southern Africa, although the total cases in Botswana and South Africa remain relatively low at the moment, so the significance of this spread is unclear. . .
READ MORE: https://arstechnica.com/science/2021/11/why-omicron-quickly-became-a-variant-of-concern/
Yikes! INTIMIDATION NOW GOES WITH THE TERRITORY FOR JOURNALISTS (Mike Masnick report in TechDirt)
When The FBI Shows Up At Your Door About Your Reporting, That's Intimidation
from the yikes dept
 Having the government show up at your door to ask some questions about your reporting can be extremely unnerving. Zack Whittaker, the top notch cybersecurity reporter for TechCrunch got to experience the fun of that when the FBI showed up at his door over a year after he had published a story about a hacker dumping thousands of Mexican embassy documents from Guatemala after the Mexican embassy left the data exposed online.
Having the government show up at your door to ask some questions about your reporting can be extremely unnerving. Zack Whittaker, the top notch cybersecurity reporter for TechCrunch got to experience the fun of that when the FBI showed up at his door over a year after he had published a story about a hacker dumping thousands of Mexican embassy documents from Guatemala after the Mexican embassy left the data exposed online.
As with many situations involving reporting on hacks and leaks, rather than focus on those actually responsible (often those who left the information exposed), law enforcement and the powers that be... often target the journalists. We saw that recently in Missouri where the governor called reporters hackers (and "fake news") for ethically disclosing that the state's elementary school agency had left teacher and administrator social security numbers exposed -- something the Department of Elementary and Secondary Education apologized for weeks later (though it didn't apologize to the journalists).
For Whittaker, the experience was reasonably concerning:
I contacted Mexico’s consulate in New York for comment, as is standard practice when reporting a story. A spokesperson said the Mexican government took the matter “very seriously.” We published our story, and that seemed to be the end of it.
The FBI knock at my door a year later suggested it wasn’t. I declined to speak with the agents and closed the door.
After we published our story the Mexican government requested the help of the U.S. Department of Justice through diplomatic channels to investigate the hack and presumably try to identify the hacker. Because I had contact with the hacker, that must have made me a subject of interest to the Mexican authorities, hence the visit a year on.
A month after the house call, the Mexican government provided the FBI with a list of written questions it wanted us to answer, many of which were already answered in the story. Our response to the DOJ declined to provide anything more than what we had already published.
However, as Zack notes, even if he knew he hadn't done anything wrong, all of this is incredibly unnerving. Legal threats (unfortunately, and often ridiculously) now come with the territory of being a journalist, but the intimidation factor is very real -- and that can be super damaging for better informing the public. Indeed, it's often why the powerful -- be they governments or just wealthy people and companies -- make use of such intimidation tactics all the time:
We’ve rebuffed spurious legal demands before, but having federal agents on your doorstep simply for doing your job is certainly a new one for me. There has been no suggestion of wrongdoing, though it’s unsettling not knowing what view Mexico would take if I ever stepped foot on its soil.
But it’s the legal threats and demands that don’t make it to print that can have the most damage. Legal demands inherently have a silencing effect. Sometimes they succeed. Journalism can be risky and the newsrooms don’t always win. Left unchecked, legal threats can have a chilling effect that stifles both security research and journalism by making it legally toxic to work. That means the world is less informed and sometimes less secure.
Filed Under: fbi, intimidation, journalism, mexico, reporting, zack whittaker
Companies: techcrunch
Monday, November 29, 2021
New Unarmed Aerial System
Schiebel Impresses at SAR Trials in Extreme Environmental Conditions in the Arctic
Schiebel, together with Andøya Space Defence, successfully demonstrated the capabilities of the CAMCOPTER® S-100 on board the coastguard vessel KV Nordkapp in Norwegian waters.
The purpose of the trials was to demonstrate the embarked Search and Rescue (SAR) and maritime surveillance capabilities of the CAMCOPTER® S-100 in the environmental conditions of the Arctic in latitudes above 75 degrees north.
The week-long trial was made possible through “Arctic 2030”, a Norwegian Ministry of Foreign Affairs programme, which aims to sustain Norwegian interests in the far north. The aim was to demonstrate that Unmanned Air Systems (UAS) ideally supplement manned helicopters, greatly enhancing SAR efforts in this remote part of the world.
The CAMCOPTER® S-100 proved that it can operate in adverse weather conditions, where manned helicopters can be at higher risk.

Global Military UAV Market Forecast to 2022
Global Trends, Market Share, Industry profiles, Growth, Opportunities by Geography and by type (UCAV, MUAV/MAV, TUAS, MALE, HALE, VTOL)
Published: December 2016 - Pages: 116 pages
Download free sample pagesThe UAS was equipped with a Trakka TC-300 EO/IR sensor, an Overwatch Imaging PT-8N Oceanwatch, a Radionor antenna as additional data link for video feed transmission as well as an Automatic Identification System (AIS) receiver.
Hans Georg Schiebel, Chairman of the Schiebel Group, said: “The CAMCOPTER® S-100 is perfect for maritime operations, including in the Arctic or Antarctic. It has proven several times that it can operate in temperatures down to -40 degrees Celsius and under harsh weather conditions. We’re proud to have been able to successfully demonstrate these remarkable capabilities to the Norwegian Coastguard and Navy.”
Source: Schiebel
Date: Nov 26, 2021
View original News release
DeFi: INFORMATION PLEASE. . .

According to a report published by crypto risk management firm Elliptic, fraud and theft of decentralized finance (DeFi) investments has surpassed $10.5 billion so far this year -- that's a 600% increase over all of 2020. DeFi is an automated method of banking and financing that runs on blockchain-based computer programming. It provides faster, cheaper cryptocurrency transactions anywhere in the world without a finance rep, credit check, or loan officer in the middle. As of this writing, more than $106 billion in funds are currently being invested in various DeFi offerings -- that's up from $12.4 billion invested just a year ago.
Key DeFi weaknesses
The Elliptic report found that the main vulnerabilities of DeFi were programming design errors that produced software bugs that hackers exploited as well as outright theft from "trusted" founders and developers who turned out to be crypto-cons. "Decentralised apps are designed to be trustless in that they eliminate any third-party control of users' funds," said Elliptic chief scientist Tom Robinson in an official statement. "But you must still trust that the creators of the protocol have not made a coding or design mistake that could lead to a loss of funds."
DeFi is not unique in risk exposure
It's worth noting that as DeFi and crypto in general are only now beginning to come into their own, those technologies shouldn't be singled out as more susceptible to fraud. Earlier this month, the San Francisco Federal Reserve branch posted a blog on its website that cited a report from Javelin Research which stated that total combined fraud losses climbed to $56 billion in 2020, with identity fraud accounting for $43 billion. Again, DeFi is not unique in its risk, it's just the latest high-profile target.
"We are still at the experimental stage and DeFi users face significant risks. As the technology matures and becomes better-regulated, losses will fall and DeFi will become a practical alternative to the banks, asset managers, and exchanges that we currently rely upon," stated Robinson.
DeFi defensive steps to take
By definition, decentralized finance puts the responsibility to manage and protect your money on you. Here are some common-sense steps you can take when reviewing DeFi options:
- Only consider projects that have a proven and published roadmap of progressive upgrades and developments spanning several years.
- Look for DeFi projects that regularly run "bug bounties" where they pay outside programmers and "good guy" hackers to pressure test their computer code to harden it against real threats.
- Only trust projects with founders who have been in the crypto space for years with a good reputation on different ventures.
- Only invest in what you know. If you don't understand liquidity pools, market makers, yield farming, or other elements of DeFi, stay away until you educate yourself.
Despite the specific DeFi difficulties outlined in the Elliptic research, all investments are susceptible to potential risk, loss, and theft. Whether investing in DeFi, derivatives, or diamonds, your best defense is a balance between being smart and being careful. If you don't take a smart and careful approach with your investments, your investments are unlikely to be yours for very long
YEAR-END MYSTERY RE-FI DEAL: 6th Time Around for City Manager Chris Brady
| File #: | 21-1307 |
| Type: | Resolution | Status: | Agenda Ready |
| In control: | City Council |
| On agenda: | 12/8/2021 |
| Title: | Authorizing the City Manager to enter into a Sixth Amendment to the Development Agreement, a First Amendment to the Amended and Restated Ground and Air Lease, and a First Amendment to the Amended and Restated License Agreement for the development commonly known as The GRID, a project on City-owned property, generally located at the southwest corner of Main Street and Pomeroy at 233 East Main Street and 34 South Pomeroy and granting an option to purchase the associated land and air rights. (District 4) |
22 October 2017
Mesa Council Study Session Mon 16 Oct 2017
Item 6A started in 1883 and Mark Freeman wants some history and he gets it from Director of Downtown Transformation Jeff McVey who stumbles quickly through an update on what was a 2.75-acre parcel that's now 3 1/2 acres -
 NEEDS A ZONING CHANGE to include some townhomes along a short stretch of Pomeroy Street that was just a drive-in to a parking lot for BenU and a 3-story parking garage behind Mesa Supreme Court
NEEDS A ZONING CHANGE to include some townhomes along a short stretch of Pomeroy Street that was just a drive-in to a parking lot for BenU and a 3-story parking garage behind Mesa Supreme CourtWHAT IS IT? 2 new 7-story buildings - watch for some details
Mayor John Giles tunes in with some mumbo jumbo about "vertical/urban" ???
 Jeff McVay, Director of "Downtown Transformation" just announced this morning on KJZZ FM that the City of Mesa is offering $3,000,000 of "incentives" to entice a developer for one of the projects at 300 E Main/Pomeroy Street on what was city-owned property for two 7-story "micro-apartment" [350 sq Ft] and mixed-use commercial/office towers atop the 3-story public parking garage for Mesa Superior Court and 14 row/townhouses on Pomeroy Street by the 3W Management Group.
Jeff McVay, Director of "Downtown Transformation" just announced this morning on KJZZ FM that the City of Mesa is offering $3,000,000 of "incentives" to entice a developer for one of the projects at 300 E Main/Pomeroy Street on what was city-owned property for two 7-story "micro-apartment" [350 sq Ft] and mixed-use commercial/office towers atop the 3-story public parking garage for Mesa Superior Court and 14 row/townhouses on Pomeroy Street by the 3W Management Group.| 18-0840 | 4-c | Resolution | 
The Second Amendment revises the development compliance dates and the permit fee |

 The media blitz is on for a development atop the 3-story city-owned parking garage behind the Mesa Superior Court building on First Avenue. Just one day after the mayor's SOTC18 speech, he's thrilled [seems like John Giles is always "thrilled" and "excited" about something] to announce "the big deal" to a news crew from ABC 15 that happened to show up in the 3-acre parking lot at 300 East Main Street between the Wells Fargo building and classroom space for Benedictine University at 225 East Main.
The media blitz is on for a development atop the 3-story city-owned parking garage behind the Mesa Superior Court building on First Avenue. Just one day after the mayor's SOTC18 speech, he's thrilled [seems like John Giles is always "thrilled" and "excited" about something] to announce "the big deal" to a news crew from ABC 15 that happened to show up in the 3-acre parking lot at 300 East Main Street between the Wells Fargo building and classroom space for Benedictine University at 225 East Main.Take a look at the video
Co+Hoots will move into a 14,000-square-foot co-working space, and will provide mentorships and internships for business students, a media release explained.
"We believe in the City of Mesa's commitment to transforming its downtown into a vibrant urban core," CO+HOOTS founder Jenny Poon said.
Here's the link > ABC15 News
It's one of the fastest "big deals" your MesaZona has never seen! And big promises for jobs
 But that's what just what staff writer Jim Walsh said in the corporate-owned The Times Media Group's East Valley Tribune in one more Spoon-Fed Story
But that's what just what staff writer Jim Walsh said in the corporate-owned The Times Media Group's East Valley Tribune in one more Spoon-Fed Story "Ready-to-Roll"By Jim Walsh, Tribune Staff Writer
"Ready-to-Roll"By Jim Walsh, Tribune Staff Writer  Tony Wall has been working on THE GRID project for more than two years. Is the problem about municipal tax-incentives/finance from the City of Mesa that involve development on a city-owned property or lack of interest from private sources for the $60-million project he can't get from private investors willing and able to assume the risk? Even after two or more rounds of financing, Tony Wall still can't get the financing - and he's lost what was called "the anchor" for THE GRID proposal [CO+HOOTS]. What about those highly-touted and highly-promoted PUBLIC PRIVATE PARTNERSHIPS? . .
Tony Wall has been working on THE GRID project for more than two years. Is the problem about municipal tax-incentives/finance from the City of Mesa that involve development on a city-owned property or lack of interest from private sources for the $60-million project he can't get from private investors willing and able to assume the risk? Even after two or more rounds of financing, Tony Wall still can't get the financing - and he's lost what was called "the anchor" for THE GRID proposal [CO+HOOTS]. What about those highly-touted and highly-promoted PUBLIC PRIVATE PARTNERSHIPS? . . Where: Main and Pomeroy streets
What: 196 sky apartments, 75 micro-units and 15 three-level row homes, plus commercial development.
The GRID is planned as an apartment complex and commercial development on three acres of city-owned land that includes an underutilized parking garage next to Benedictine University.
A Co+Hoots co-working space was initially set to anchor The GRID but is now working to partner with Benedictine.
The GRID plans to build a six-story building on Main Street and four stories of apartments on top of the existing three-story parking garage.

Mesa would continue to own the garage, providing the developer 340 spaces for residents and commercial visitors.
 McVay said city officials talked with investors earlier this month and they’re optimistic the project will happen.
McVay said city officials talked with investors earlier this month and they’re optimistic the project will happen.He said he hopes financing for The GRID will wrap up by the end of 2019 and that construction could begin early next year
Construction begins on the Grid, $75M opportunity zone project in Downtown Mesa (Phoenix Business Journal)
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...