No doubt one of those "cautionary tales" . The devices, known as Handheld Interagency Identity Detection Equipment (HIIDE), are designed to guarantee accurate identification of a person, even if their appearance has dramatically changed.
JUST HOW EASY Is it to eject/insert a memory card? (Illustration How to insert and eject a memory card)
CCC captures U.S. military biometrics database
The U.S. military used biometric devices en masse to capture people in Afghanistan. Some devices were left behind during the hasty withdrawal of NATO troops. CCC researchers found large amounts of biometric and other personal data when analyzing such devices. In the wrong hands, this data is life-threatening for people in Afghanistan and Iraq.
The biometric devices were used to identify individuals, e. g. at checkpoints when screening for wanted persons, or to control access by local collaborators. On used U.S. military equipment, we discovered, among other things, an unprotected biometrics database containing names, fingerprints, iris scans, and photographs of more than 2,600 Afghans and Iraqis.
Backstory: Biometric census of the Afghan population
The entire population of Afghanistan was biometrically catalogued -- supported by the German Bundeswehr. The motivation for this systematic collection of fingerprints, irises, faces and DNA was to enable the distinction between good and bad people. Programs such as the Automated Biometric Identification System (ABIS) were designed to identify known criminals, as well as local collaborators or Afghan security forces, at any time.
✓ Any biometric database is a ticking time bomb. When the Taliban captured the biometric devices, concerns were raised that the devices could be used to identify former local collaborators. Human Rights First thus published a guide to evading the misuse of biometric data.
✓ The risk was well known to all
There is no escape from biometric surveillance. We cannot simply change our biometric data. This danger was well known those in charge. Back in 2007, a member of the U.S. military warned of a similar biometric database in Iraq: "This database... becomes a hit list if it gets in the wrong hands."
✓✓ The data is unprotected
Allegedly, access to the biometrics database should not be possible without further technology. But even if that were the case, of course, the Taliban could still simply use the devices. Unfortunately, our research shows that all data on the mobile biometric devices is completely unprotected. We were able to read, copy and analyze them without any difficulty.
✓ ✓✓ Used devices in online auctions
Alarmed by news reports about biometric devices in the Taliban's hands, Matthias Marx, snoopy, starbug, md and other CCC members started to gather information about these devices. While doing so, they came across several offers at an online auction house. They were able to acquire a total of
- four devices of type SEEK II (Secure Electronic Enrollment Kit) and
- two devices of type HIIDE 5 (Handheld Interagency Identity Detection Equipment).
The devices were examined forensically.
From a technical perspective, the analyses were downright boring: All storage mediums were unencrypted. A well-documented standard password was the only thing needed to gain access. Also, the database was a standard database with standard data formats. It was fully exported with little effort.
✓✓✓✓ sensitive biometric data of 2,632 individuals
The extracted data was all the more impressive: The various devices shopped online contained names and biometric data of two U.S. military personnel, GPS coordinates of past deployment locations, and a massive biometrics database with names, fingerprints, iris scans and photos of 2,632 people. The device containing this database had last been used somewhere between Kabul and Kandahar in mid-2012.
✓✓ ✓✓✓ Lack of risk awareness among manufacturers, US and German military
The CCC then informed the SEEK device's manufacturer, Crossmatch Technologies (now: HID Global), and two known users of the devices, the US Department of Defense and the German Bundeswehr, about the vulnerability. The responsible parties were also informed that used devices with highly sensitive data can easily be ordered on the Internet. However, no one seems to care about the data leak:
We received an acknowledgement of receipt from the Bundeswehr, the Department of Defense kindly referred us to the manufacturer, and the manufacturer did nothing.
Two and a half months after our report, we were able to order another biometric device online.
✓✓✓✓✓✓ Life-threatening irresponsibility
"The irresponsible handling of this high-risk technology is unbelievable," said Matthias Marx, who led the CCC research group. The consequences are life-threatening for the many people in Afghanistan who were abandoned by the western forces. "It is inconceivable to us that the manufacturer and former military users do not care that used devices with sensitive data are being hawked online," Marx continued.
And yet all of this was predictable, because biometric databases cannot be effectively or permanently secured against illegitimate interests. What happened in Afghanistan is just a foretaste of the many biometric databases that will fall into the wrong hands in the future.
It is always a bad idea to centrally collect such data in bulk.
We have a few more questions
With regard to a Memorandum of Understanding, we are interested in the German Bundeswehr's role:
- Was the data collected under the ISAF mandate actually deleted?
- How did the Bundeswehr deal with the risk that the Afghan biometrics database could become a hit list?
- How are or were devices and access to biometric databases of the Bundeswehr secured against misuse?
- Were local collaborators informed about the risks of biometric capture?
- Was the Bundeswehr able to secure or destroy its own or externally provided biometric enrollment devices?
Links and further information
Researchers Shocked At Sensitive US Military Data Found On Memory Card Sold On Ebay
"In 2021, The Intercept reported that the Taliban had seized biometric devices left behind by the US military in Afghanistan, giving them identifiable information on those who worked with American forces.
A group of researchers in Germany called the Chaos Computer Club, led by Matthias Marx, wondered if it was really that easy to get highly classified military data. They purchased a few military surplus biometric scanners on eBay to discover that, yes, they had purchased the biometric data of thousands of individuals.
The devices, known as Handheld Interagency Identity Detection Equipment (HIIDE), are designed to guarantee accurate identification of a person, even if their appearance has dramatically changed. A HIIDE collects fingerprints, iris scans, and photographs for facial recognition, and it stores that data on a memory card. According to a report in the New York Times, the Chaos Computer Club, which has a history of digging into biometrics, discovered the memory card on one of its purchased HIIDE devices had not been erased. It contained the names, national origins, photographs, fingerprints and iris scans of 2,632 people.
Most of the records were from Kandahar, Afghanistan in the summer of 2012, but a second device had fingerprints and iris scans of US military personnel who were stationed in Jordan in 2013. Marx expressed surprise that the US military didn't even attempt to protect the data. The data was on a memory card, so it would have been trivially easy to dispose of the data before selling the biometric scanners. "They didn’t care about the risk, or they ignored the risk," said Marx.

The devices left in Afghanistan could contain similarly precise data, which would make it almost impossible for former US allies to hide from Taliban forces. This may amplify calls to grant asylum claims to get these people out of Afghanistan.
The Department of Defense demurred when asked for comment, saying it had not seen the data and therefore could not "confirm the authenticity of the alleged data or otherwise comment on it." It did, however, ask that any hardware with confidential information be returned to the military for analysis. The Chaos Computer Club says that given the sensitive nature of the data, it plans to delete everything it has found. These devices are capable of storing up to 22,000 full biometric profiles, so technically, it could have been a lot worse.' READ MORE
RELATED CONTENT
Corporate, Department of Defense
See also:
 Handheld Interagency Identity Detection Equipment
Handheld Interagency Identity Detection Equipment
- 76 pages
- © 2008 L-1 Identity Solutions Inc.
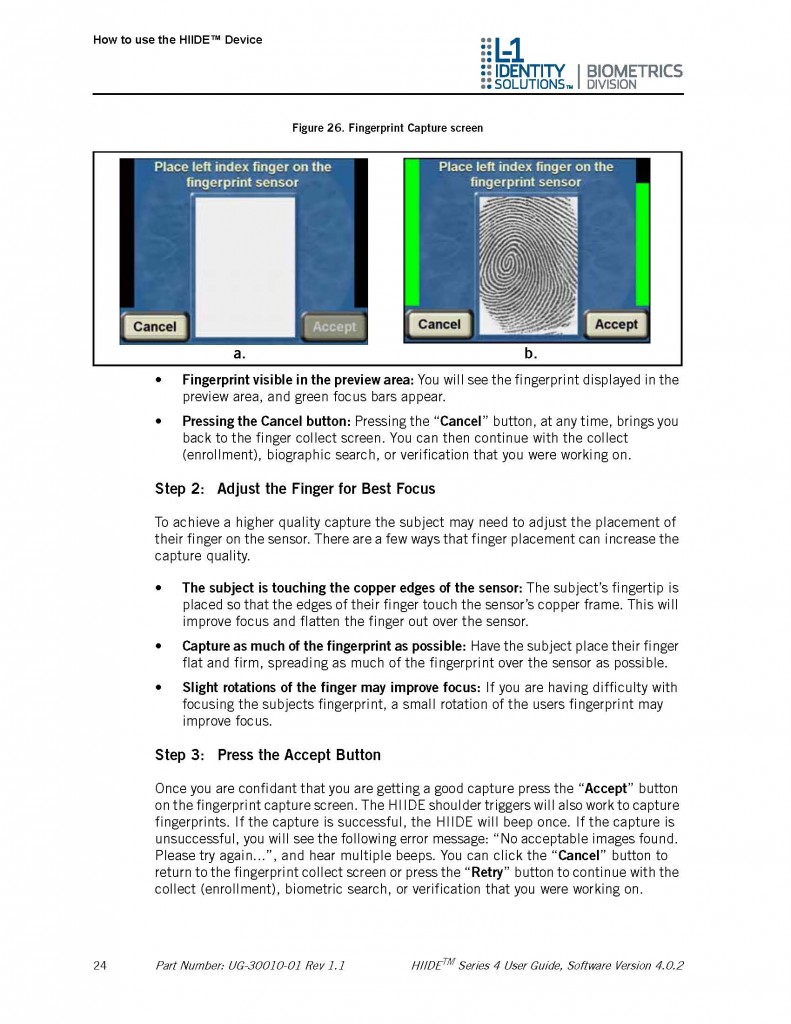
The HIIDE includes two separate cameras for imaging an individual’s irises and face, and a sensor pad for scanning fingerprints. These three sensors capture the minute details of a subject’s iris, fingerprint and face, as digital photographs, or “scans.” The HIIDE™ translates the photographic data into a binary code and links that code to biographic data about the individual, such as name and a personal identification number. The HIIDE then processes the code and biographic data and builds a portfolio for the individual that is stored in a database.
Once an individual has had a record created, or has been “enrolled,” that individual is part of the HIIDE database. One can “recognize,” or confirm that individual’s identity in the future by comparing a live scan of the subjects: iris, fingerprints and/or face to the biometrics contained in the database.
…
.png)
.jpg)
.png)


.jpg)
.jpg)





No comments:
Post a Comment