CosmicEnergy was discovered after a sample was uploaded to the VirusTotal malware analysis platform in December 2021
"Although we have not identified sufficient evidence to determine the origin or purpose of COSMICENERGY, we believe that the malware was possibly developed by either Rostelecom-Solar or an associated party to recreate real attack scenarios against energy grid assets," Mandiant said.
New Russian-linked CosmicEnergy malware targets industrial systems
- May 25, 2023
- 11:27 AM
- 0

"Mandiant security researchers have discovered a new malware called CosmicEnergy designed to disrupt industrial systems and linked to Russian cybersecurity outfit Rostelecom-Solar (formerly Solar Security).
The malware specifically targets IEC-104-compliant remote terminal units (RTUs) commonly used in electric transmission and distribution operations across Europe, the Middle East, and Asia.
CosmicEnergy was discovered after a sample was uploaded to the VirusTotal malware analysis platform in December 2021 by someone with a Russian IP address.
Analysis of the leaked malware sample has revealed several noteworthy aspects regarding CosmicEnergy and its functionality.
First, the malware shares similarities with previous OT malware like Industroyer and Industroyer.V2, both used in attacks targeting Ukrainian energy providers in December 2016 and April 2022.
Additionally, it's Python-based and uses open-source libraries for OT protocol implementation, just like other malware strains targeting industrial control systems, including IronGate, Triton, and Incontroller.
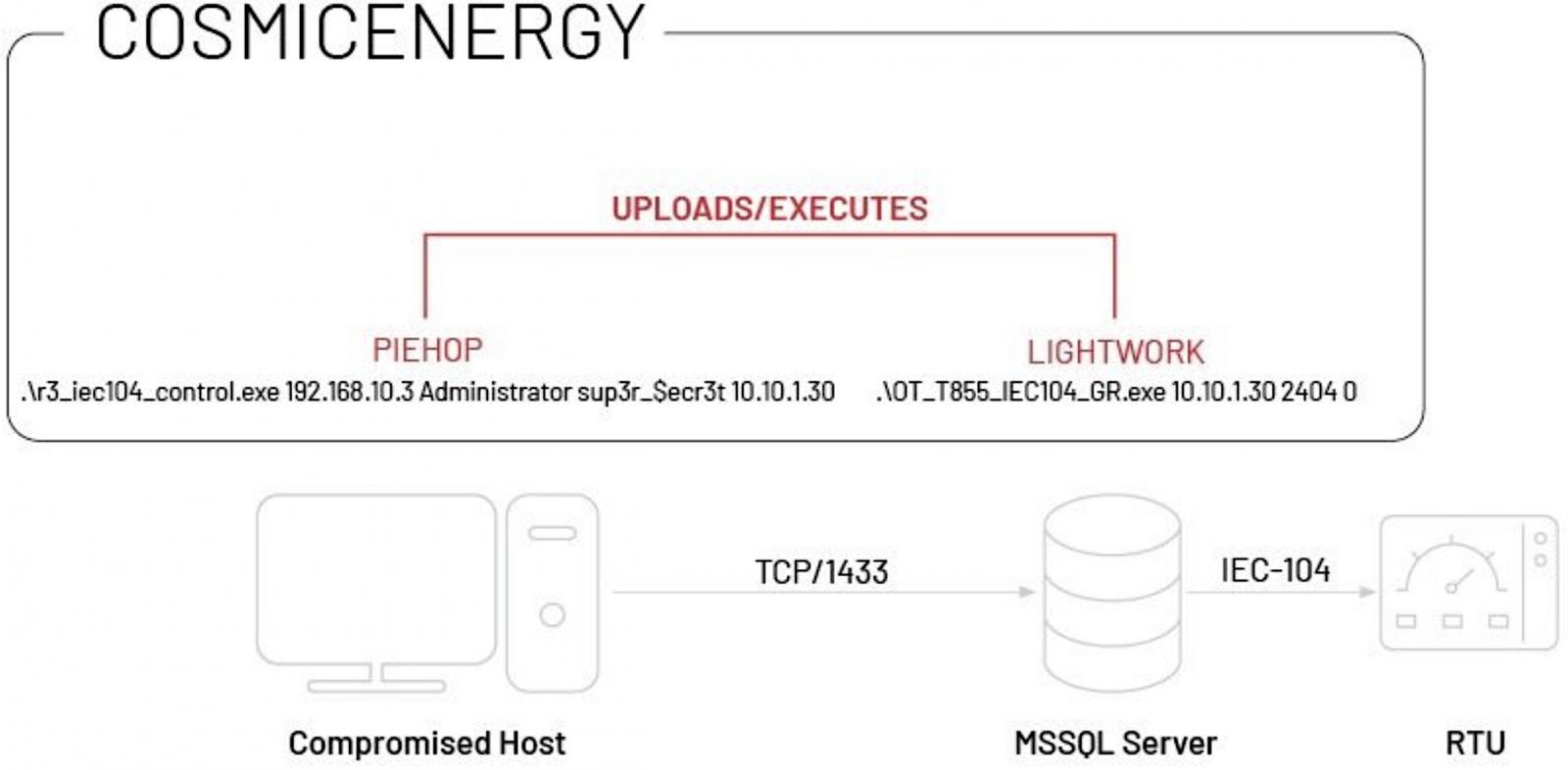
Just like Industroyer, CosmicEnergy likely gains access to the target's OT systems via compromised MSSQL servers using the Piehop disruption tool.
Once inside the victims' network, the attackers can control RTUs remotely by issuing IEC-104 "ON" or "OFF" commands via the Lightwork malicious tool.
- Mandiant believes this newly discovered malware may have been developed as a red teaming tool designed to simulate disruption exercises by Russian cybersecurity company Rostelecom-Solar.
- Based on public information showing that Rostelecom-Solar received funding from the Russian government for cybersecurity training and simulating electric power disruption, Mandiant suspects CosmicEnergy could also be used by Russian threat actors in disruptive cyberattacks targeting critical infrastructure like other red team tools.
"During our analysis of COSMICENERGY, we identified a comment in the code that indicated the sample uses a module associated with a project named 'Solar Polygon.' We searched for the unique string and identified a single match to a cyber range (aka polygon) developed by Rostelecom-Solar," Mandiant said.
"Although we have not identified sufficient evidence to determine the origin or purpose of COSMICENERGY, we believe that the malware was possibly developed by either Rostelecom-Solar or an associated party to recreate real attack scenarios against energy grid assets," Mandiant said.
"Given that threat actors use red team tools and public exploitation frameworks for targeted threat activity in the wild, we believe COSMICENERGY poses a plausible threat to affected electric grid assets."
As Microsoft reported in April 2022, after Russia invaded Ukraine, Russian hacking groups have deployed many malware families (some of them never before seen in the wild) in destructive attacks against Ukrainian targets, including critical infrastructure.
The list includes but is not limited to
- WhisperGate/WhisperKill,
- FoxBlade (aka HermeticWiper),
- SonicVote (aka HermeticRansom),
- CaddyWiper,
- DesertBlade,
- Industroyer2,
- Lasainraw (aka IsaacWiper), and
- FiberLake (aka DoubleZero).
The Sandworm Russian military hackers used the Industroyer2 malware to target the ICS network of a prominent Ukrainian energy provider but failed to take down its high-voltage electrical substations and disrupt energy delivery across the country."
SERGIU GATLAN
Sergiu Gatlan has covered cybersecurity, technology, and other news beats for more than a decade. Email or Twitter DMs for tips.-
The Week in Ransomware - May 26th 2023 - Cities Under Attack
Ransomware gangs continue to hammer local governments in attacks, taking down IT systems and disrupting cities' online services.
- MAY 26, 2023
- 04:45 PM
 2
2

Mozilla stops Firefox fullscreen VPN ads after user outrage

ChatGPT is down worldwide - OpenAI confirms issues
MORE
-
US govt contractor ABB confirms ransomware attack, data theft
Swiss tech multinational and U.S. government contractor ABB has confirmed that some of its systems were impacted by a ransomware attack, previously described by the company as "an IT security incident."
- MAY 26, 2023
- 12:33 PM
 0
0
-
Emby shuts down user media servers hacked in recent attack
Emby says it remotely shut down an undisclosed number of user-hosted media server instances that were recently hacked by exploiting a previously known vulnerability and an insecure admin account configuration.
- MAY 26, 2023
- 10:56 AM
 2
2
-
Mozilla stops Firefox fullscreen VPN ads after user outrage
Firefox users have been complaining about very intrusive full-screen advertisements promoting Mozilla VPN displayed in the web browser when navigating an unrelated page.
- MAY 26, 2023
- 10:52 AM
 8
8
-
BlackByte ransomware claims City of Augusta cyberattack
The city of Augusta in Georgia, U.S., has confirmed that the most recent IT system outage was caused by unauthorized access to its network.
- MAY 26, 2023
- 09:27 AM
 0
0







No comments:
Post a Comment