___________________________________________________________________________________
___________________________________________________________________________________
___________________________________________________________________________________
Qakbot botnet dismantled after infecting over 700,000 computers
- August 29, 2023
- 12:54 PM
- 1

Qakbot, one of the largest and longest-running botnets to date, was taken down following a multinational law enforcement operation spearheaded by the FBI and known as Operation 'Duck Hunt.'
- Over the past 18 months alone, losses have surpassed 58 million dollars.
- Throughout the years, Qakbot has consistently served as an initial infection vector for various ransomware gangs and their affiliates or operators, including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex, and, most recently, Black Basta.
"The victims ranged from financial institutions on the East Coast to a critical infrastructure government contractor in the Midwest to a medical device manufacturer on the West Coast," FBI Director Christopher Wray said.
"This botnet provided cybercriminals like these with a command-and-control infrastructure consisting of hundreds of thousands of computers used to carry out attacks against individuals and businesses all around the globe."
Taken down after taking control of Qakbot admin's PC
The FBI dismantled Qakbot after it infected over 700,000 computers (over 200,000 in the United States) after infiltrating parts of the botnet's infrastructure, including one of the computers used by a Qakbort admin.
- Those files included communications (e.g., chats discussed in detail below) between the Qakbot administrators and co-conspirators
- and a directory containing several files holding information about virtual currency wallets," according to court documents.
"A different file, found elsewhere on the same computer, named 'payments.txt,' contained a list of ransomware victims, details about the ransomware group, computer system details, dates, and an indication of the amount of BTC paid to the Qakbot administrators in connection with the ransomware attack."
- On Friday night, they redirected Qakbot traffic to servers controlled by the agency, which provided the FBI with the access needed to deploy an uninstaller to compromised devices across the globe, clearing the infection and preventing the deployment of additional malicious payloads.
- While victims received no notification when the uninstaller was executed to remove the malware from their systems, the FBI notified them using IP address and routing information collected from the victims' computers when deploying the removal tool.
- We also published a follow-up story with more details on how the FBI was able to nuke the Qakbot malware from Windows computers infected by the botnet.
"The scope of this law enforcement action was limited to information installed on the victim computers by the Qakbot actors," the Justice Department said in a press release today.
"It did not extend to remediating other malware already installed on the victim computers and did not involve access to or modification of the information of the owners and users of the infected computers."
The FBI also worked with CISA, Shadowserver, the Microsoft Digital Crimes Unit, the National Cyber Forensics and Training Alliance, and Have I Been Pwned to notify victims.
The operation was coordinated by the FBI's Los Angeles Field Office, the U.S. Attorney's Office for the Central District of California, and the Criminal Division's Computer Crime and Intellectual Property Section (CCIPS), in cooperation with Eurojust.
"Qakbot was the botnet of choice for some of the most infamous ransomware gangs, but we have now taken it out. This operation also has led to the seizure of almost 9 million dollars in cryptocurrency from the Qakbot cybercriminal organization, which will now be made available to victims," said U.S. Attorney Martin Estrada.
In May, cybersecurity and intelligence agencies from all Five Eyes member nations also took down the Snake peer-to-peer botnet operated by Russia's Federal Security Service (FSB) and linked to the notorious Turla hacking group.
___________________________________________________________________________________
How the FBI nuked Qakbot malware from infected Windows PCs
- August 29, 2023
- 04:45 PM
- 3

During this past weekend’s law enforcement operation, Operation Duck Hunt, the FBI redirected the botnet’s network communications to servers under its control, allowing agents to identify approximately 700,000 infected devices (200,000 located in the U.S.).
- After they took control of the botnet, the FBI devised a method to uninstall the malware from the victims’ computers, effectively dismantling the botnet’s infrastructure, from the victims’ PCs to the malware operators’ own computers.
What is Qakbot?
Qakbot, aka Qbot and Pinkslipbot, started as a banking trojan in 2008, used to steal banking credentials, website cookies, and credit cards to conduct financial fraud.
However, over time, the malware evolved into a malware delivery service utilized by other threat actors to gain initial access to networks for conducting ransomware attacks, data theft, and other malicious cyber activities.
Qakbot is distributed through phishing campaigns that utilize a variety of lures, including reply-chain email attacks, which is when threat actors use a stolen email thread and then reply to it with their own message and an attached malicious document.
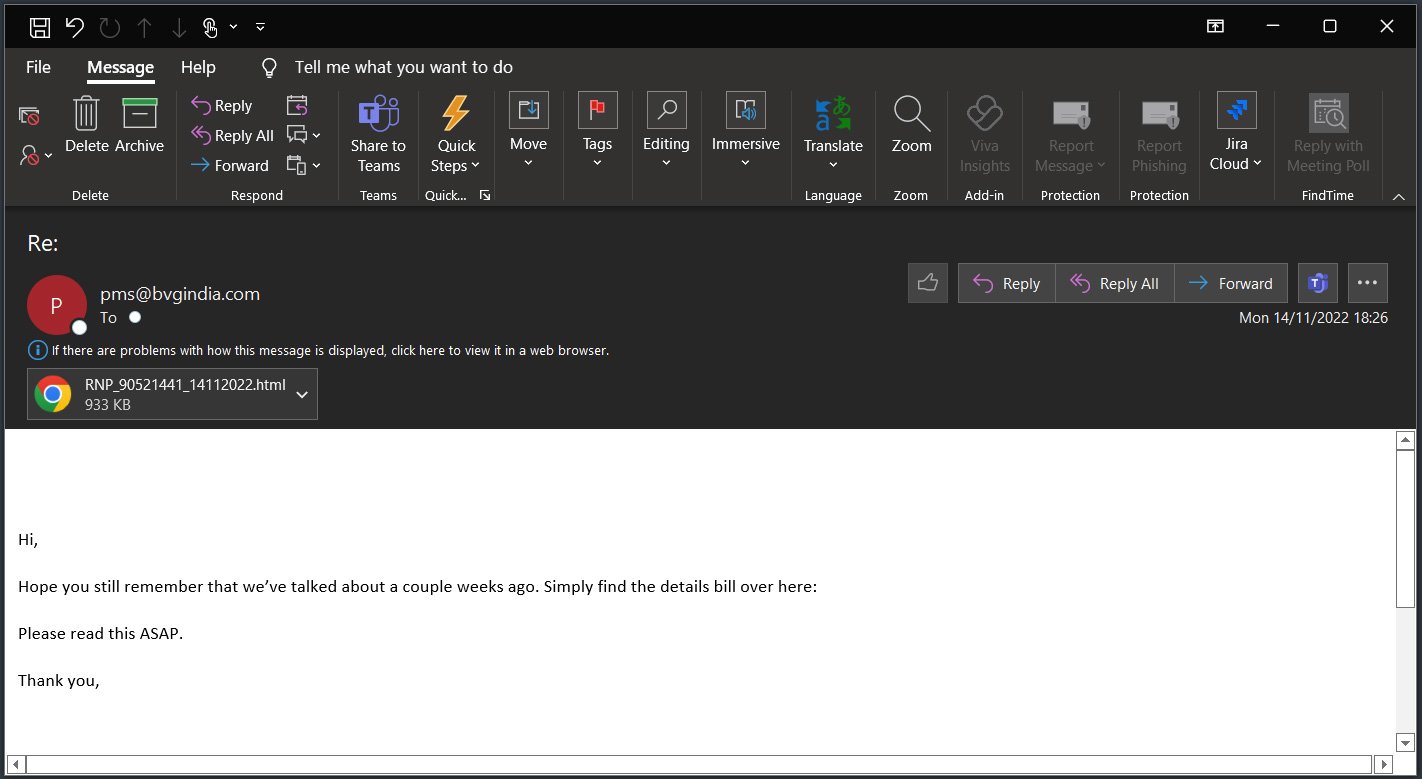
Source: BleepingComputer
These emails typically include malicious documents as attachments or links to download malicious files that install the Qakbot malware on a user’s device.
- These documents change between phishing campaigns and range from Word or Excel documents with malicious macros, OneNote files with embedded files, to ISO attachments with executables and Windows shortcuts.
- Some of them are also designed to exploit zero-day vulnerabilities in Windows.
Regardless of how the malware is distributed, once Qakbot is installed on a computer, it will be injected into the memory of a legitimate Windows processes, such as wermgr.exe or AtBroker.exe, to attempt to evade detection by security software.
For example, the image below depicts the Qbot malware injected into the memory of the legitimate wermgr.exe process.
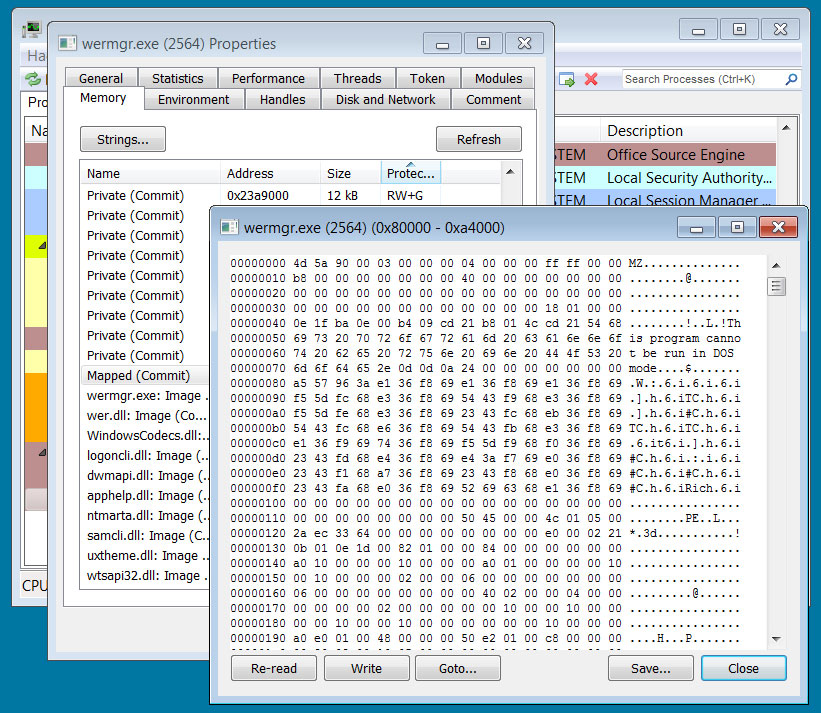
Source: BleepingComputer
- However, the Qakbot operators also partnered with other threat actors to facilitate cybercrime, such as providing ransomware gangs with initial access to corporate networks.
- In the past, Qakbot has partnered with multiple ransomware operations, including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex, and, most recently, Black Basta and BlackCat/ALPHV.
How the FBI uninstalled Qakbot
According to an application for seizure warrant released by the Department of Justice, the FBI was able to gain access to the Qakbot admin computers, which helped law enforcement map out the server infrastructure used in the botnet's operation.
Based on their investigation, the FBI determined that the Qakbot botnet utilized Tier-1, Tier-2, and Tier-3 command and control servers, which are used to issue commands to execute, install malware updates, and download additional partner payloads to devices.
Tier-1 servers are infected devices with a "supernode" module installed that act as part of the command and control infrastructure of the botnet, with some of the victims located in the USA. Tier-2 servers are also command and control servers, but the Qakbot operators operate them, usually from rented servers outside the USA.
The FBI says that both the Tier-1 and Tier-2 servers are used to relay encrypted communication with the Tier-3 servers.
These Tier-3 servers act as the central command and control servers for issuing new commands to execute, new malicious software modules to download, and malware to install from the botnet's partners, such as ransomware gangs.
Every 1 to 4 minutes, the Qakbot malware on infected devices would communicate with a built-in list of Tier-1 servers to establish encrypted communication with a Tier-3 server and receive commands to execute or new payloads to install
However, after the FBI infiltrated the Qakbot's infrastructure and administrator's devices, they accessed the encryption keys used to communicate with these servers.
Using these keys, the FBI used an infected device under their control to contact each Tier-1 server and have it replace the already installed Qakbot "supernode" module with one created by law enforcement.
This new FBI-controlled supernode module used different encryption keys not known to the Qakbot operators, effectively locking them out of their own command and control infrastructure as they no longer had any way to communicate with the Tier-1 servers.
The FBI then created a custom Windows DLL (or Qakbot module) [VirusTotal] that acted as a removal tool and was pushed to infected devices from the now-hijacked Tier-1 servers.
Based on an analysis of the FBI module by SecureWorks, this custom DLL file issued the
QPCMD_BOT_SHUTDOWN command to the Qakbot malware running on infected devices, which causes the malware process to stop running.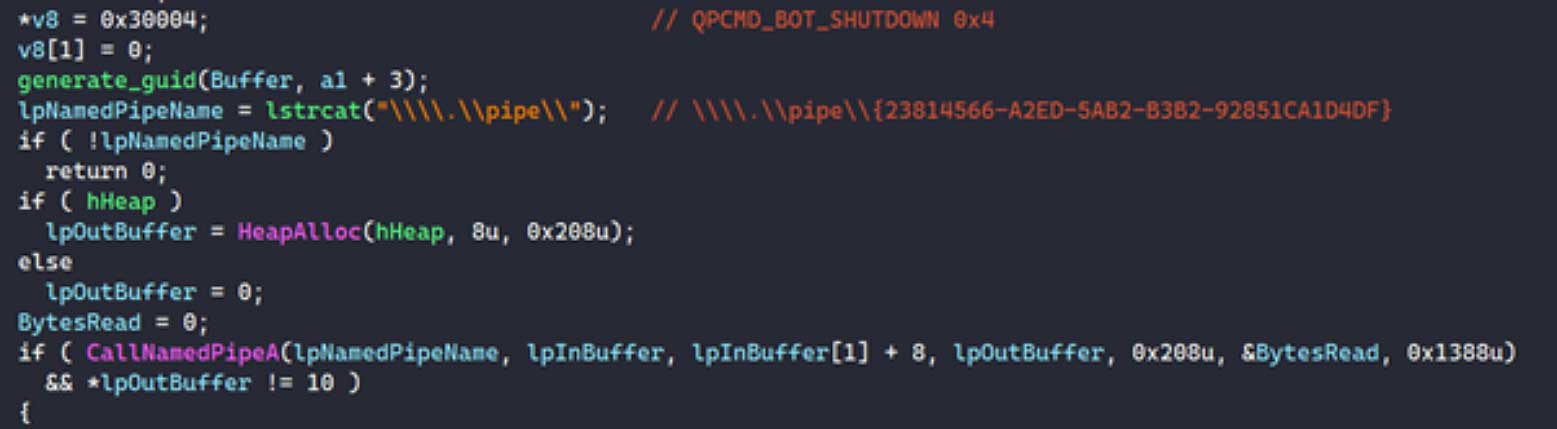
Source: SecureWorks
SecureWorks says they first saw this custom module pushed down to infected devices on August 25th at 7:27 PM ET.
"The shellcode unpacks a custom DLL (dynamic link library) executable that contains code that can cleanly terminate the running Qakbot process on the host."
The FBI says that this Qakbot removal tool was authorized by a judge with a very limited scope of only removing the malware from infected devices.
Furthermore, as the malware is injected into the memory of another process, the removal tool does not need to read or write anything to the hard drive to shut down the process.
"Qakbot establishes persistence on a host when it detects a user initiating a system shutdown. Using the named pipe to terminate the Qakbot process bypasses persistence," continues SecureWorks.
"As a result, Qakbot will not run if the host is restarted."
However, as pointed out in the comments below, QakBot may also create a scheduled task to launch the malware on startup, potentially loading the malware into memory again.
At this time, the FBI is unsure of the total number of devices that have been cleaned in this manner, but as the process started over the weekend, they expect that further devices will be cleaned as they connect back to the hijacked Qakbot infrastructure.
The FBI also shared a database containing credentials stolen by the Qakbot malware with Have I Been Pwned and the Dutch National Police.
As no notifications will be displayed on infected devices when the malware is removed, you can use these services to see if your credentials were stolen, indicating that you may have at one point been infected with the Qakbot malware.
This is not the first time the FBI used a court-approved seizure warrant to remove malware from infected devices.
The FBI previously received court approval to remove the Russian Snake data theft malware and the Emotet malware from infected devices, as well as web shells on Microsoft Exchange servers deployed in ProxyLogon attacks.
While this is definitely a win for law enforcement, it may not be the end of the Qakbot operation as no arrests were made.
Therefore, we will likely see the Qakbot operators begin to rebuild their infrastructure over the next few months through phishing campaigns or by purchasing installations through other botnets.
Update 8/30/23: Added information about persistence
___________________________________________________________________________________







No comments:
Post a Comment