16-30 November 2023 Cyber Attacks Timeline – HACKMAGEDDON
ALPHV/BlackCat Claims Technica Corporation Cyberattack
ALPHV/BlackCat Hackers Claim Attack on Technica, Documents at Risk of Exposure
Technica Corporation cyberattack could have far-reaching implications, given the nature of the leaked documents related to intelligence agencies.
The hacking group ALPHV/BlackCat has set its sights on Technica Corporation, claiming to have accessed classified and top-secret documents related to the FBI and various US intelligence agencies. The Technica Corporation cyberattack, characterized by the group’s previous bold maneuvers, raises concerns about the potential ramifications for national security.
Technica Corporation, a veteran-owned company founded in 1991, has been instrumental in providing information technology solutions to support the Federal Government’s mission to defend and protect the United States.
Technica Corporation Cyberattack: Uncertain Motives
The motive behind the cyberattack on Technica Corporation remains unclear, as ALPHV/BlackCat has not disclosed specific details regarding its objectives.

The Cyber Express Team attempted to verify the claim by reaching out to Technica Corporation officials. As of the writing of this report, no response has been received, leaving the authenticity of the cyberattack unconfirmed. However, if proven true, the Technica Corporation cyberattack could have far-reaching implications, given the nature of the leaked documents related to intelligence agencies.
A Pattern of Bold Moves: ALPHV/BlackCat’s Previous Targets
This Technica Corporation cyberattack follows ALPHV/BlackCat’s pattern of high-profile attacks. In January 2024, the hacking group targeted the healthcare website BrightStar Care, threatening to report the organization to the U.S. Department of Health and Human Services. The claim, similar to the current situation, remains unverified.
In December of the preceding year, BlackCat lodged a complaint with the SEC against MeridianLink, publicly reporting a cybersecurity incident and accusing the company of withholding information about a data breach. This move highlighted a new trend in cybercrime—directly involving regulatory bodies in addressing cybersecurity breaches.
A peculiar development occurred when the FBI seized control of ALPHV/BlackCat’s website, prompting a defiant response from the hackers. The group reestablished control and issued a menacing message to the FBI, asserting that the agency had limited access to decryption keys, leaving more than 3000 companies without access to their keys.
ALPHV/BlackCat’s deviation from its usual covert operations and ransom demands has raised questions about the group’s motivations and evolving strategies. Whether this audacious move is a sign of desperation, an attempt to exert more pressure for ransom, or an innovative tactic to manipulate regulations for illicit gains remains uncertain.
As cybersecurity threats continue to evolve, the Technica Corporation incident highlights the urgent need for enhanced cybersecurity measures and collaboration between government agencies and private enterprises to safeguard sensitive information and national security.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
NOTE: At this time, there are over 80 companies listed on Cactus' data leak site whose data has been leaked or the threat actors warn they will do so.
Energy giant Schneider Electric hit by Cactus ransomware attack
- January 29, 2024
- 03:10 PM
- 0

BleepingComputer has learned that the ransomware attack hit the company's Sustainability Business division earlier this month on January 17th.
- The attack disrupted some of Schneider Electric's Resource Advisor cloud platform, which continue to suffer outages today.
- While it is not known what type of data was stolen, the Sustainability Business division provides consulting services to enterprise organizations, advising on renewable energy solutions and helping them navigate complex climate regulatory requirements for companies worldwide.
Source: BleepingComputer
Customers of Schneider Electric's Sustainability Business division include Allegiant Travel Company, Clorox, DHL, DuPont, Hilton, Lexmark, PepsiCo, and Walmart.
The stolen data could contain sensitive information about customers' power utilization, industrial control and automation systems, and compliance with environmental and energy regulations.
It is not known if Schneider Electric will be paying a ransom demand, but if one is not paid, we will likely see the ransomware gang leaking the stolen data as they have done after previous attacks.
In a statement to BleepingComputer, Schneider Electric confirmed that its Sustainability Business division suffered a cyberattack and that data was accessed by the threat actors. However, the company says the attack was restricted to this one divisiion and did not impact other parts of the company.
"From a recovery standpoint, Sustainability Business is performing remediation steps to ensure that business platforms will be restored to a secure environment. Teams are currently testing the operational capabilities of impacted systems with the expectation that access will resume in the next two business days.
From a containment standpoint, as Sustainability Business is an autonomous entity operating its isolated network infrastructure, no other entity within the Schneider Electric group has been affected.
From an impact assessment standpoint, the on-going investigation shows that data have been accessed. As more information becomes available, the Sustainability Business division of Schneider Electric will continue the dialogue directly with its impacted customers and will continue to provide information and assistance as relevant.
From a forensic analysis standpoint, the detailed analysis of the incident continues with leading cybersecurity firms and the Schneider Electric Global Incident Response team continuing to take additional actions based on its outcomes, working with relevant authorities." - Schneider Electric.
Schneider Electric is a French multinational company that manufactures energy and automation products ranging from household electrical components found in big box stores to enterprise-level industrial control and building automation products.
Schneider Electric had $28.5 billion in revenue for the first nine months of 2023 and employs over 150,000 people worldwide. Schneider Electric is expected to release its 2023 full-year financial results next month.
Some of its well-known consumer brands include Homeline, Square D, and APC, the manufacturer of widely used uninterruptable power supply (UPS) devices.
Schneider Electric was previously targeted in the widespread MOVEit data theft attacks by the Clop ransomware gang that impacted over 2,700 companies.
If you have any information regarding this incident or any other undisclosed attacks, you can contact us confidentially via Signal at 646-961-3731 or at tips@bleepingcomputer.com.
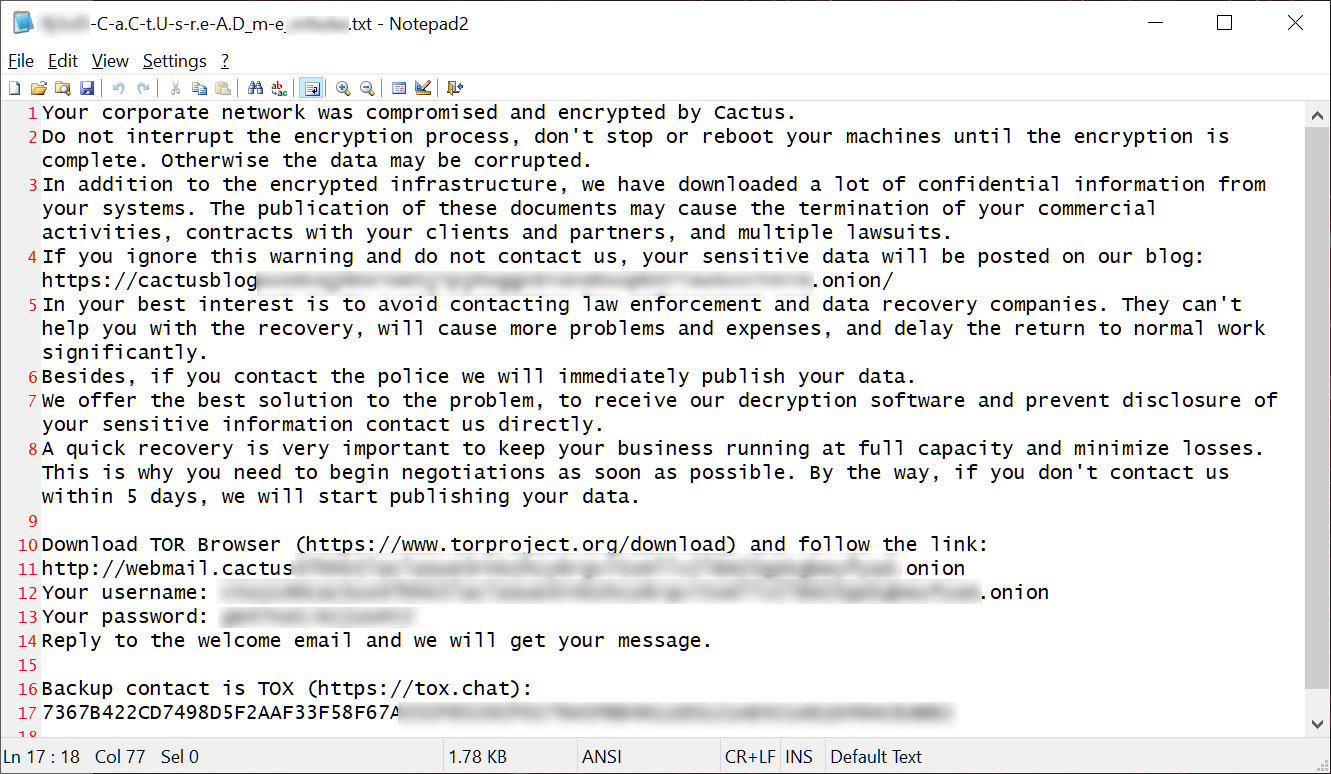
Who is Cactus ransomware
The Cactus ransomware operation launched in March 2023 and has since amassed numerous companies that they claim were breached in cyberattacks.
Like all ransomware operations, the threat actors will breach corporate networks through purchased credentials, partnerships with malware distributors, phishing attacks, or by exploiting vulnerabilities.
Once the threat actors gain access to a network, they quietly spread to other systems while stealing corporate data on servers.
After stealing the data and gaining administrative privileges on the network, the threat actors encrypt files and leave ransom notes behind.
Source: BleepingComputer
The threat actors will then conduct double-extortion attacks, which is when they demand a ransom to receive both a file decryptor and promise to destroy and not leak stolen data.
For those companies who do not pay a ransom, the threat actors will leak their stolen data on a data leak site.
At this time, there are over 80 companies listed on Cactus' data leak site whose data has been leaked or the threat actors warn they will do so.
-
US charges two more suspects with DraftKing account hacks
The U.S. Department of Justice arrested and charged two more suspects for their involvement in the hacking of almost 68,000 DraftKings accounts in a November 2022 credential stuffing attack.
- JANUARY 30, 2024
- 04:28 PM
 1
1
-
Ivanti warns of new Connect Secure zero-day exploited in attacks
Today, Ivanti warned of two more vulnerabilities impacting Connect Secure, Policy Secure, and ZTA gateways, one of them a zero-day bug already under active exploitation.
- JANUARY 31, 2024
- 08:41 AM
 0
0
-
Citibank sued over failure to defend customers against hacks, fraud
New York Attorney General Letitia James sued Citibank over its alleged failure to defend customers against hacks and scams and refusal to reimburse victims after allowing fraudsters to steal millions from their accounts.
- JANUARY 30, 2024
- 11:08 AM
 1
1
-
A mishandled GitHub token exposed Mercedes-Benz source code
A mishandled GitHub token gave unrestricted access to Mercedes-Benz's internal GitHub Enterprise Service, exposing source code to the public.
- JANUARY 30, 2024
- 01:42 PM
 0
0
-
Microsoft Teams phishing pushes DarkGate malware via group chats
New phishing attacks abuse Microsoft Teams group chat requests to push malicious attachments that install DarkGate malware payloads on victims' systems.
- JANUARY 30, 2024
- 12:47 PM
 0
0








![Whitepaper] Black Cat Ransomware](https://securityscorecard.com/wp-content/uploads/2024/01/AdobeStock_552370317-Security-Risk-Operations2.webp)

No comments:
Post a Comment