In epic hack, Signal developer turns the tables on forensics firm Cellebrite
Widely used forensic software can be exploited to infect investigators' computers.
Virtually no limits
“There are virtually no limits on the code that can be executed,” Marlinspike wrote.
He continued:
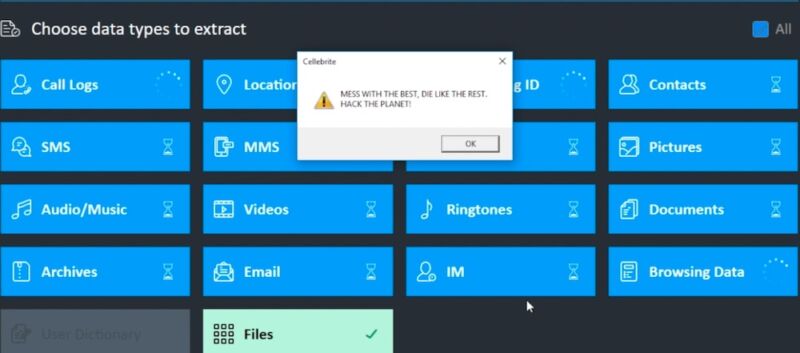
For example, by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures. This could even be done at random, and would seriously call the data integrity of Cellebrite’s reports into question.
. . . Marlinspike included a video that shows UFED as it parses a file he formatted to execute arbitrary code on the Windows device. The payload uses the MessageBox Windows API to display a benign message, but Marlinspike said that “it’s possible to execute any code, and a real exploit payload would likely seek to undetectably alter previous reports, compromise the integrity of future reports (perhaps at random!), or exfiltrate data from the Cellebrite machine.”
. . .Marlinspike said he obtained the Cellebrite gear in a “truly unbelievable coincidence” as he was walking and “saw a small package fall off a truck ahead of me.” The incident does seem truly unbelievable. Marlinspike declined to provide additional details about precisely how he came into possession of the Cellebrite tools. . .
The vulnerabilities could provide fodder for defense attorneys to challenge the integrity of forensic reports generated using the Cellebrite software. Cellebrite representatives didn’t respond to an email asking if they were aware of the vulnerabilities or had plans to fix them. . ."


No comments:
Post a Comment