This Internet Explorer MSHTML remote code execution vulnerability, tracked as CVE-2021-40444, was disclosed by Microsoft on Tuesday but with few details as it has not been patched yet.
Windows MSHTML zero-day defenses bypassed as new info emerges
- September 9, 2021
- 04:37 PM
- 1

New details have emerged about the recent Windows CVE-2021-40444 zero-day vulnerability, how it is being exploited in attacks, and the threat actor's ultimate goal of taking over corporate networks.
This Internet Explorer MSHTML remote code execution vulnerability, tracked as CVE-2021-40444, was disclosed by Microsoft on Tuesday but with few details as it has not been patched yet.
The only information shared by Microsoft was that the vulnerability uses malicious ActiveX controls to exploit Office 365 and Office 2019 on Windows 10 to download and install malware on an affected computer.
Since then, researchers have found the malicious Word documents used in the attacks and have learned new information about how the vulnerability is exploited.
Why the CVE-2021-40444 zero-day is so critical
Since the release of this vulnerability, security researchers have taken to Twitter to warn how dangerous it is even though Microsoft Office's 'Protected View' feature will block the exploit.
When Office opens a document it checks if it is tagged with a "Mark of the Web" (MoTW), which means it originated from the Internet.
If this tag exists, Microsoft will open the document in read-only mode, effectively blocking the exploit unless a user clicks on the 'Enable Editing' buttons.
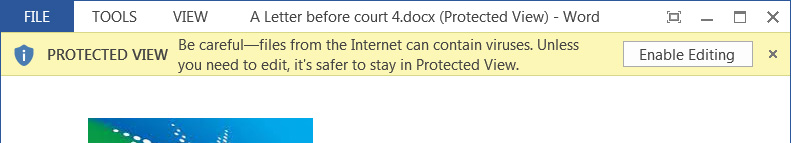
As the "Protected View" feature mitigates the exploit, we reached out to Will Dormann, a vulnerability analyst for CERT/CC, to learn why security researchers are so concerned about this vulnerability.
Dormann told BleepingComputer that even if the user is initially protected via Office's 'Protected View' feature, history has shown that many users ignore this warning and click on the 'Enable Editing' button anyway.
Dormann also warns that there are numerous ways for a document not to receive the MoTW flag, effectively negating this defense.
"If the document is in a container that is processed by something that is not MotW-aware, then the fact that the container was downloaded from the Internet will be moot. For example, if 7Zip opens an archive that came from the Internet, the extracted contents will have no indication that it came from the Internet. So no MotW, no Protected View."
"Similarly, if the document is in a container like an ISO file, a Windows user can simply double-click on the ISO to open it. But Windows doesn't treat the contents as having come from the Internet. So again, no MotW, no Protected View."
"This attack is more dangerous than macros because any organization that has chosen to disable or otherwise limit Macro execution will still be open to arbitrary code execution simply as the result of opening an Office document." - Will Dormann
To make matters even worse, Dormann discovered that you could use this vulnerability in RTF files, which do not benefit from Office's Protected View security feature.
Inspired by @buffaloverflow, I tested out the RTF attack vector. And it works quite nicely.
— Will Dormann (@wdormann) September 9, 2021
WHERE IS YOUR PROTECTED MODE NOW? pic.twitter.com/qf021VYO2R


No comments:
Post a Comment