Network hackers focus on selling high-value targets in the U.S.

A Crowdstrike report looking into access brokers' advertisements since 2019 has identified a preference in academic, government, and technology entities based in the United States.
- February 23, 2022
- 05:46 PM
 0
0
"A Crowdstrike report looking into access brokers' advertisements since 2019 has identified a preference in academic, government, and technology entities based in the United States.
Initial access brokers are a vital link in the cybercrime chain, as these threat actors are devoted to breaching corporate networks for future attacks.
These brokers then sell access to these networks to other cybercriminals who will do the "dirty" and more risky work of deploying malware, ransomware, move laterally, conduct espionage, etc.
Previously, we have seen threat actors selling access to networks for as little as $1,500, but as analyzed in the Crowdstrike report, the price depends on the compromised organization's location, size, and type.
Countries targeted
The most lucrative targets in terms of how much they can yield in dark web listings are the U.S. and the U.K. Listings from these two countries are selling for an average price of just below $4,000.
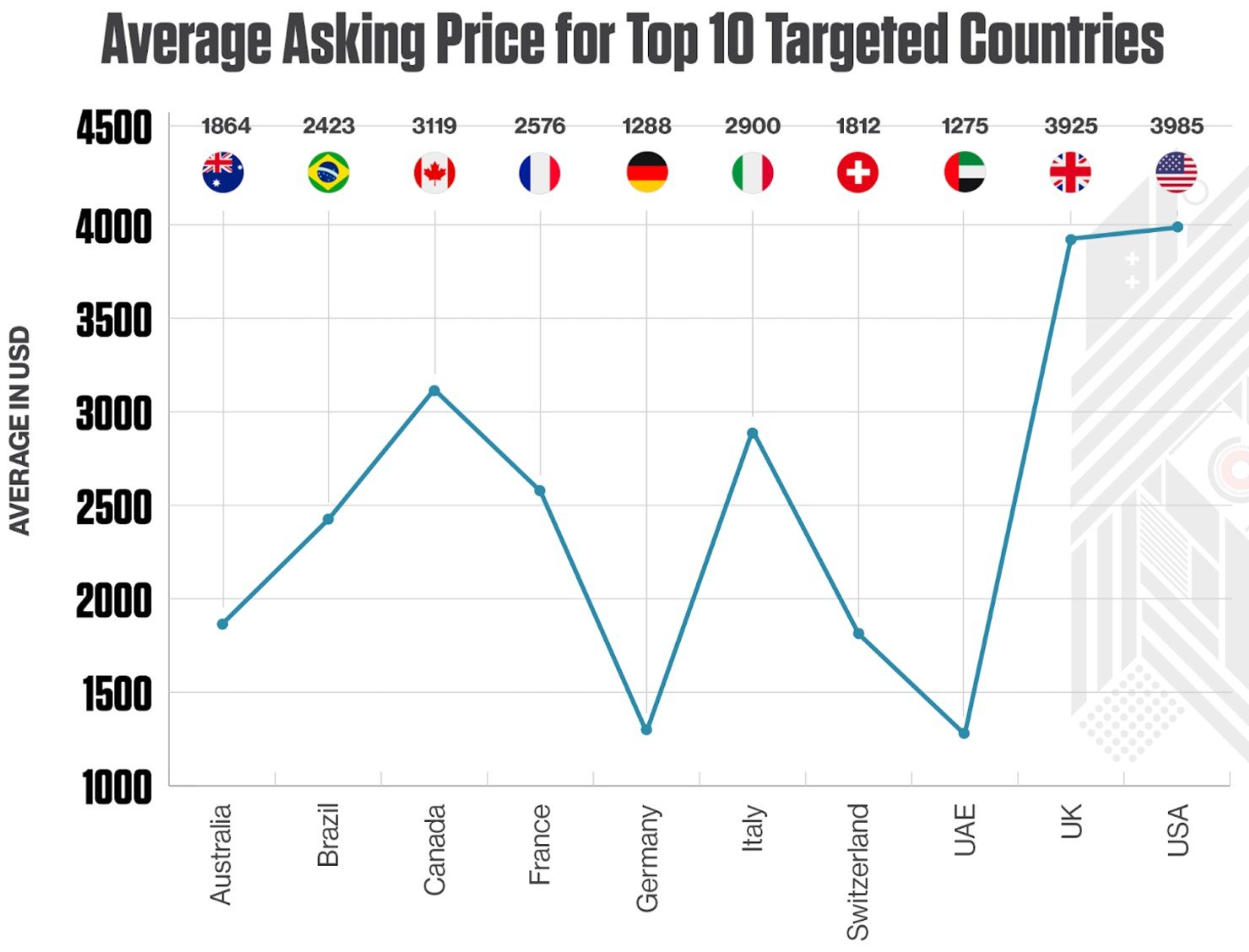
This is why the United States takes the lion's share of the target focus, accounting for over half (55%) of all initial access offerings on dark web forums and markets.
.jpg)
The U.K. is far behind with only 7%, while Brazil, Canada, and France have a significant share of the targeted pie (between 6% and 8%).
Another highly sought-after listing is access in Canadian organizations, which sells at an average of $3,119, while Italy is also fairing well with $2,900.
Sectors targeted
The sectors targeted by initial access brokers are also determining factors.
Depending on the entity, threat actors may use the access for financial extortion, data exfiltration, cyber-espionage, BEC acts, etc.
> According to Crowdstrike, the academic, government, and technology sectors are targeted the most, followed by financial, healthcare, and energy services.
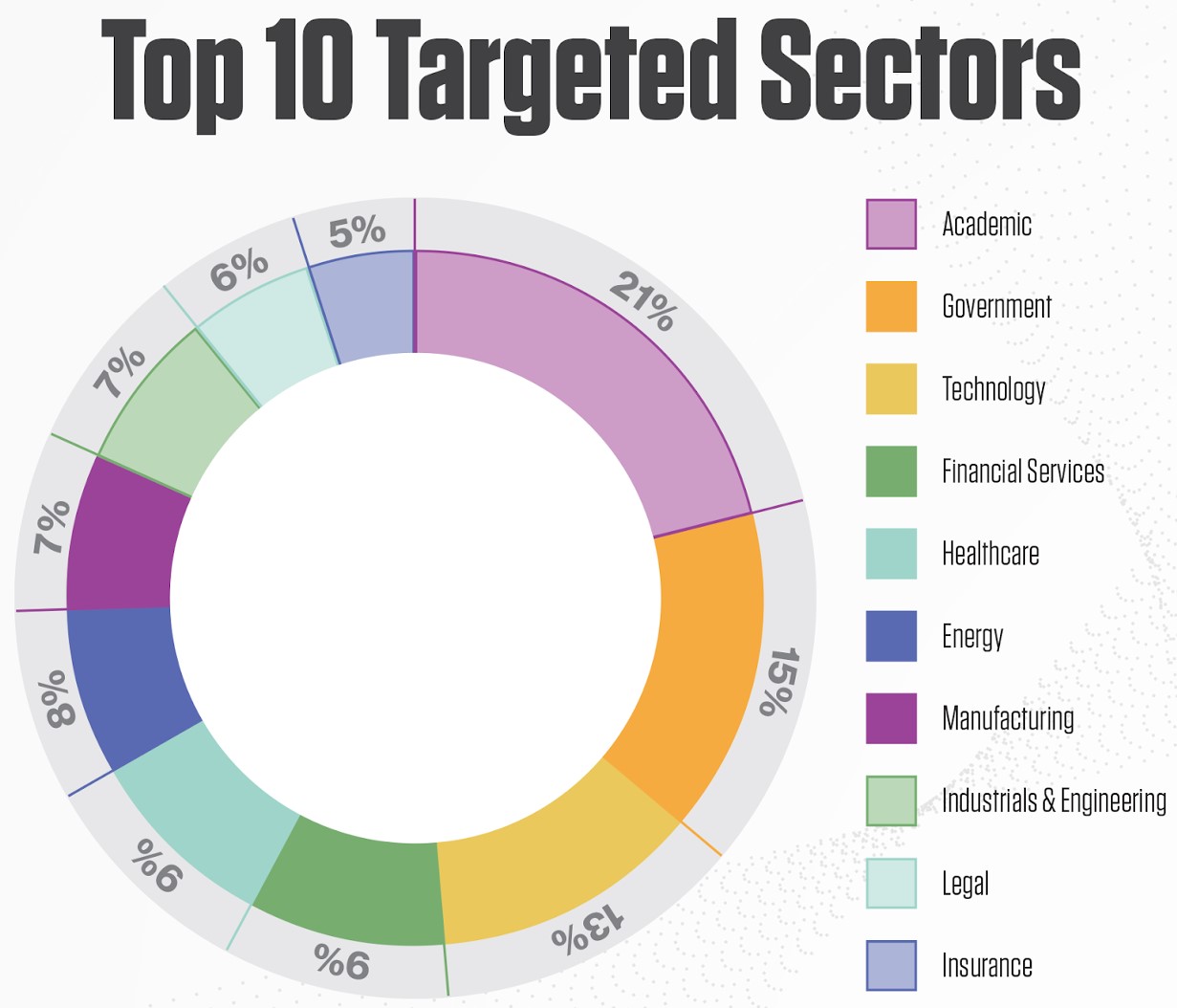
Considering that the dataset began in 2019, the outbreak of COVID-19, which led to a global research effort for the development of a vaccine, must have played a crucial role in the ranking of academic at the top.
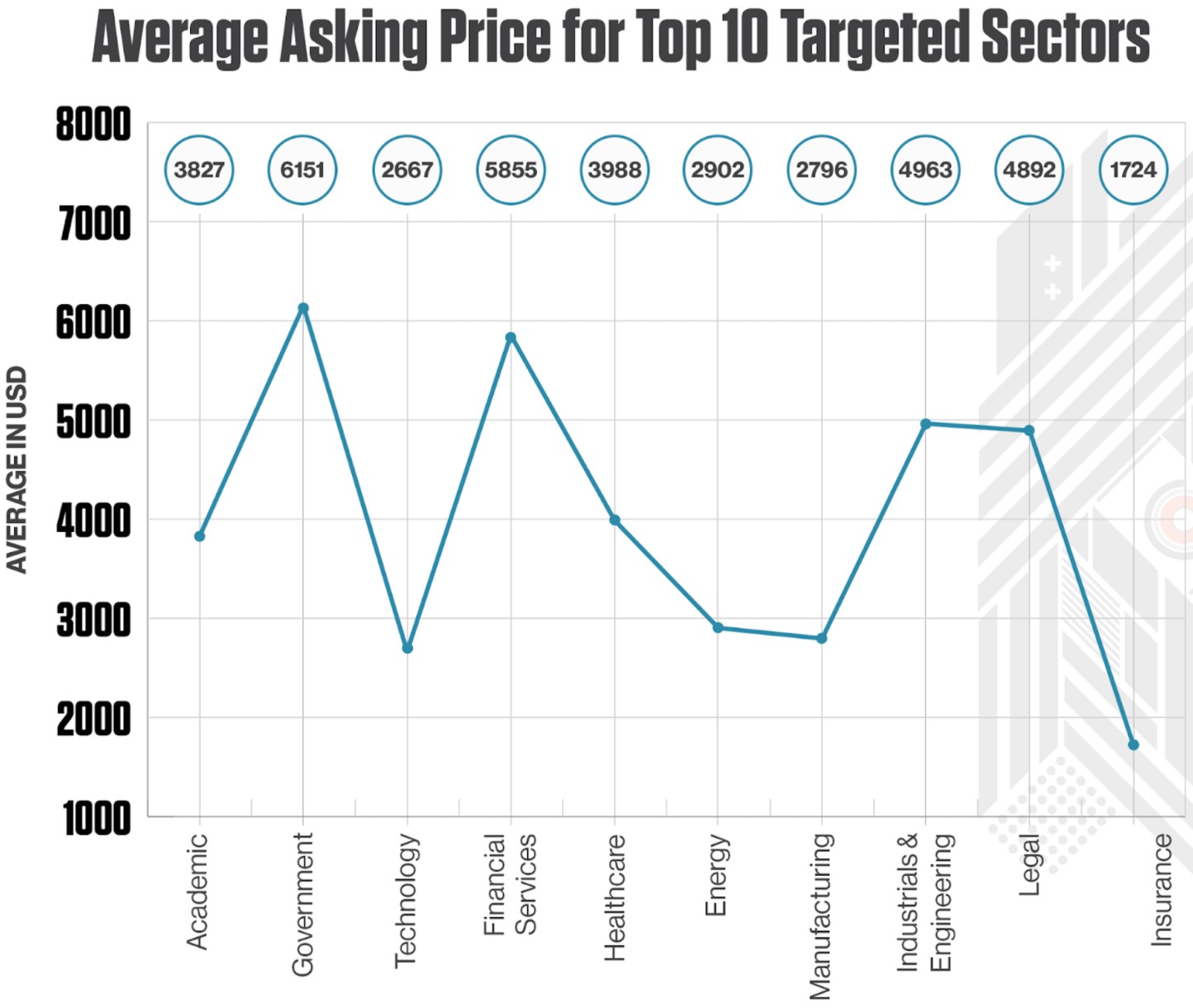
When looking at the average asking price for each sector, government listings are the most valuable at $6,151, followed by financial service providers at $5,855.
Outlook
The access broker economy is shifting, like all sectors of cybercrime, and while these threat actors employ all tricks in the book to keep the supply alive, easy and widely exploitable flaws like Log4Shell have pushed them aside.
Also, ransomware groups now use exclusive initial access contractors directed to attack specific targets rather than buying random firm access that may also be doubtful.
Crowdstrike has identified a short-lived fallout between Q4 2021 and Q1 2022 but now reports a resurgence in network access advertisements.
The demand is expected to remain high in 2022, but it'll all depend on the vulnerability landscape and the trends that underpin the operation of hands-on hackers like RaaS operators.
New data-wiping malware used in destructive attacks on Ukraine
- February 23, 2022
- 05:31 PM
- 0

Cybersecurity firms have found a new data wiper used in destructive attacks today against Ukrainian networks just as Russia moves troops into regions of Ukraine.
"A data wiper is malware that intentionally destroys data on a device to make the data unrecoverable and for the operating system to no longer work correctly.
This morning, Ukrainian government agencies and banks were hit with DDoS attacks that took websites offline.
Soon after, cybersecurity firms Symantec and ESET disclosed that they found a new destructive data wiper malware also used in cyberattacks today against Ukrainian organizations.
Symantec shared the hash of the new data-wiper on Twitter, which is currently being detected by only 16/70 security engines on VirusTotal. . ."

LockBit, Conti most active ransomware targeting industrial sector
Ransomware attacks extended into the industrial sector last year to such a degree that this type of incident became the number one threat in the industrial sector.
- February 23, 2022
- 05:48 AM
 0
0

Entropy ransomware linked to Evil Corp's Dridex malware
Analysis of the recently-emerged Entropy ransomware reveals code-level similarities with the general purpose Dridex malware that started as a banking trojan.
- February 23, 2022
- 08:34 AM
 0
0

FTC: Americans report losing over $5.8 billion to fraud in 2021
The US Federal Trade Commission (FTC) said today that Americans reported losses of more than $5.8 billion to fraud during last year, a massive total increase of over 70% compared to the losses reported in 2020.
- February 23, 2022
- 08:44 AM
 0
0

US, UK link new Cyclops Blink malware to Russian state hackers
New malware dubbed Cyclops Blink has been linked to the Russian-backed Sandworm hacking group in a joint security advisory published today by US and UK cybersecurity and law enforcement agencies.
- February 23, 2022
- 10:49 AM
 0
0

Ukrainian government and banks once again hit by DDoS attacks
The sites of several Ukrainian government agencies (including the Ministries of Foreign Affairs, Defense, and Internal Affairs, the Security Service, and the Cabinet of Ministers), and of the two largest state-owned banks are again targeted by Distributed Denial-of-Service (DDoS) attacks.
- February 23, 2022
- 12:25 PM
 0
0

Nigerian hacker pleads guilty to stealing payroll deposits
A Nigerian national named Charles Onus has pled guilty in the District Court of the Southern District of New York to hacking into a payroll company's user accounts and stealing payroll deposits.
- February 23, 2022
- 01:47 PM
 1
1

Ransomware extortion doesn't stop after paying the ransom
A global survey that looked into the experience of ransomware victims highlights the lack of trustworthiness of ransomware actors, as in most cases of paying the ransom, the extortion simply continues.
- February 23, 2022
- 02:43 PM
 1
1
NSA-linked Bvp47 Linux backdoor widely undetected for 10 years
A report released today dives deep into technical aspects of a Linux backdoor now tracked as Bvp47 that is linked to the Equation Group, the advanced persistent threat actor tied to the U.S. National Security Agency.
- February 23, 2022
- 07:21 PM
 1
1


No comments:
Post a Comment