Intro: No stopping anytime soon: Here's one report and then another and another taken from Bleeping Computer https://www.bleepingcomputer.com/
OAS platform vulnerable to critical RCE and API access flaws

- May 26, 2022
- 03:11 PM
"Threat analysts have disclosed vulnerabilities affecting the Open Automation Software (OAS) platform, leading to device access, denial of service, and remote code execution.
The OAS platform is a widely used data connectivity solution that unites industrial devices (PLCs, OPCs, Modbus), SCADA systems, IoTs, network points, custom applications, custom APIs, and databases under a holistic system.
It is a versatile and flexible hardware and software connectivity solution that facilitates data transfers between proprietary devices and apps from multiple vendors and connects them to firm-specific products, custom software, etc.
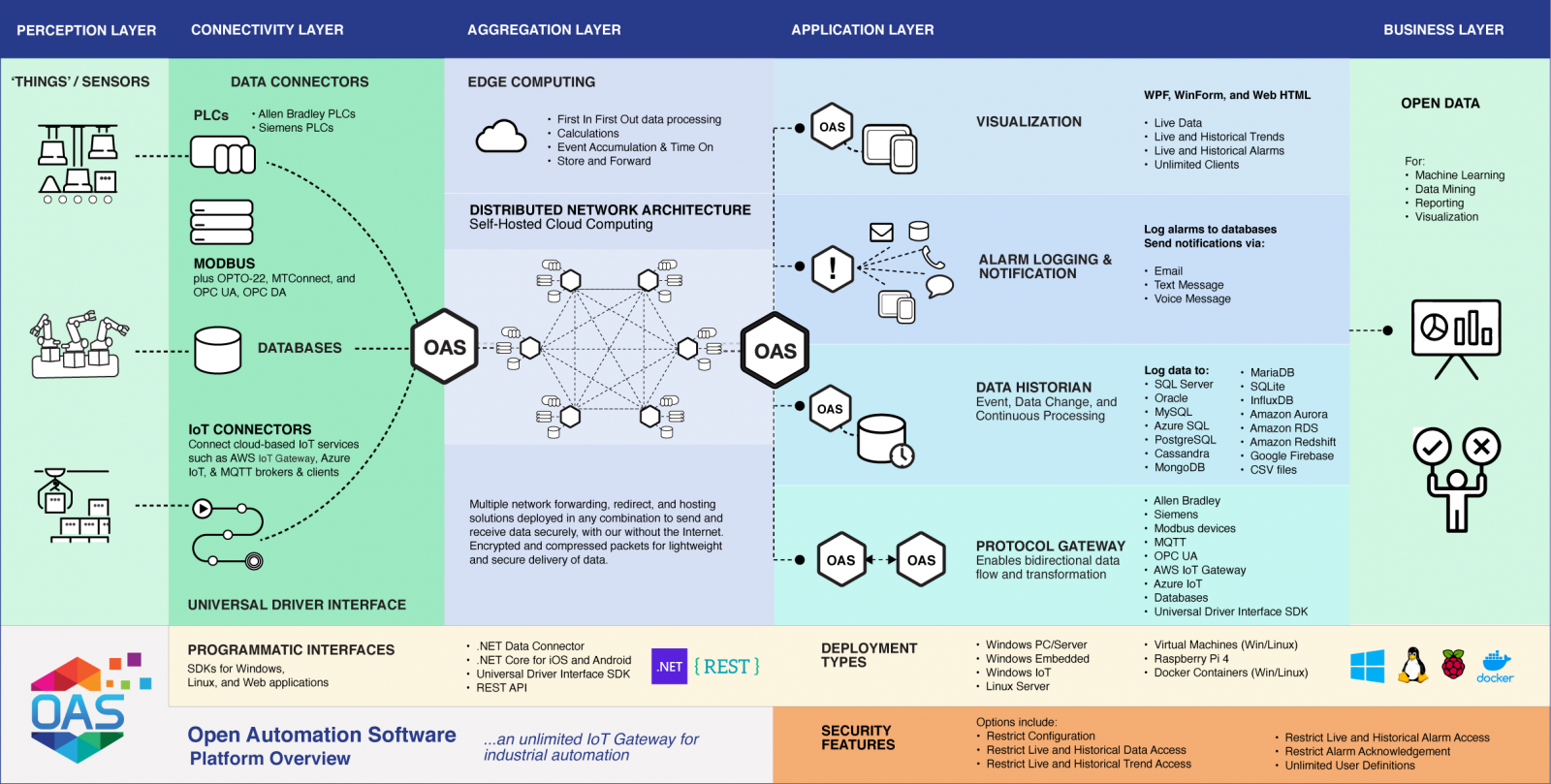
OAS is used by Michelin, Volvo, Intel, JBT AeroTech, the U.S. Navy, Dart Oil and Gas, General Dynamics, AES Wind Generation, and several other high-profile industrial entities.
As such, vulnerabilities in the platform can put crucial industrial sectors at risk of disruption and confidential information disclosure.
Critical flaws
According to a report by Cisco Talos, OAS platform version 16.00.0112 and below is vulnerable to a range of high and critical severity bugs that create the potential for damaging attacks.
Starting with the most critical of the bunch, CVE-2022-26833 has a CVSS severity rating of 9.4 out of 10 and concerns the unauthenticated access and use of the REST API functionality in OAS.
An attacker could trigger the exploitation of this flaw by sending a series of specially crafted HTTP requests to the vulnerable endpoints.
As Cisco explains, the REST API is designed to give programmatic access for configuration changes and data viewing to the “Default” user, which Talos researchers were able to authenticate by sending a request with a blank username and password.
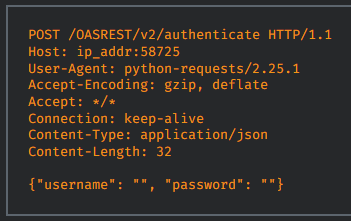
(Cisco)
The second critical flaw is CVE-2022-26082, rated at 9.1, which is a file write vulnerability in the OAS Engine SecureTransferFiles module.
According to Cisco, a specially-crafted series of network requests sent to the vulnerable endpoint may lead to arbitrary remote code execution.
“By sending a series of properly-formatted configuration messages to the OAS Platform, it is possible to upload an arbitrary file to any location permissible by the underlying user. By default, these messages can be sent to TCP/58727 and, if successful, will be processed by the user oasuser with normal user permissions.” - Cisco Talos
This enables a remote threat actor to upload new authorized_keys files to the oasuser’s .ssh directory, making it possible to access the system via ssh commands.
The other flaws discovered by Cisco Talos are all categorized as high-severity (CVSS: 7.5) and are the following:
- CVE-2022-27169: obtain directory listing via network requests
- CVE-2022-26077: information disclosure targeting account credentials
- CVE-2022-26026: denial of service and loss of data links
- CVE-2022-26303 and CVE-2022-26043: external configuration changes and creation of new users and security groups
Cisco provides mitigation advice for each of the above vulnerabilities, which involves disabling services and closing communication ports, so if upgrading to a newer version of OAS is impossible, there might be a solution with some functionality or convenience trade-offs.
Otherwise, upgrading to a more recent version of the OAS platform would be advisable. The security fixes for the two critical flaws described above landed in version 16.00.0.113, which was released as a security update on May 22, 2022.
Upgrade lags are to be expected in industrial environments that operate intricate and complicated data connectivity systems, but in this case, due to the severity of the disclosed flaws, it is crucial to take immediate action."

 0
0




No comments:
Post a Comment