Hmm..."Ironically, most of the DDoSes relied on DDoS protection, such as those from content delivery network Cloudflare, to keep from being taken down in DDoSes themselves. In some cases, defendants relied on Cloudflare’s free tier, with others using a more advanced tier that required payment...The charges and seizures are part of “Operation PowerOFF,” an ongoing campaign by international law enforcement agencies to dismantle criminal DDoS-for-hire services...(Seizure notice on the sites taken over by authorities (Image: Hackread.com)
"The seizure is a part of a coordinated operation dubbed Operation PowerOFF conducted in collaboration with the UK, Europol, and the Netherlands.
On Wednesday, December 14th, the US Department of Justice (DoJ) announced seizing 48 domains and charging six suspects for being involved in Stresser, aka Booter services.
These services offered malicious actors a platform to carry out DDoS attacks (distributed denial of service attacks).
DDoS attacks – A Growing Concern
DDoS attacks are a growing concern among businesses and organizations around the world. These malicious cyber attacks involve flooding an organization’s network with large amounts of traffic, making it difficult or impossible for legitimate users to access the services they need.
While DDoS attacks can be difficult to prevent, there are several steps organizations can take to protect themselves against such threats. The first step is to ensure that all software and applications used by the organization are updated regularly with the latest security patches.
Organizations should also consider investing in firewalls and other security solutions that can detect and block DDoS attacks before they have a chance to affect operations. Additionally, having security protocols in place for authenticating user accounts is important in order to ensure that malicious actors cannot gain unauthorized access
Seized Domains Details
According to the DoJ, the Federal Bureau of Investigation (FBI) seized 48 domains offering to conduct DDoS for hire services on behalf of other cybercriminals in exchange for payment in cryptocurrency.
The seized websites reportedly claimed to offer the service of testing the resilience of web infrastructure but actually offered DDoS for hire services. The platforms had targeted victims worldwide, including in the USA. Their key targets were government agencies, educational institutions, and gaming platforms.
- Bootersx
- IPStressercom
- SecurityTeamio
- Astrostresscom
- RoyalStressercom
- TrueSecurityServicesio
According to the DoJ’s press release, millions of users were targeted via these platforms. Just on one platform (IPStressercom), over a million registered users carried out at least 30 million DDoS attacks between 2014-2022.
. . ." READ MORE
- Teen hires attacker to DDoS his school district
- Authorities seize 15 popular DDoS-for-hire websites
- World’s largest DDoS-for-hire service & seize its domain
- Dutch Police Seizes 15 DDoS-for-hire services in one week
- No prison for the crook duo behind vDOS DDoS for hire service
Prosecutors charge 6 people for allegedly waging massive DDoS attacks
48 Internet domains associated with the services have also been seized.
"Federal prosecutors on Wednesday charged six people for allegedly operating websites that launched millions of powerful distributed denial-of-service attacks on a wide array of victims on behalf of millions of paying customers.
The sites promoted themselves as booter or stressor services designed to test the bandwidth and performance of customers’ networks. Prosecutors said in court papers that the services were used to direct massive amounts of junk traffic at third-party websites and Internet connections customers wanted to take down or seriously constrain. Victims included educational institutions, government agencies, gaming platforms, and millions of individuals. Besides charging six defendants, prosecutors also seized 48 Internet domains associated with the services.
“These booter services allow anyone to launch cyberattacks that harm individual victims and compromise everyone’s ability to access the Internet,” Martin Estrada, US attorney for the Central District of California, said in a statement. “This week’s sweeping law enforcement activity is a major step in our ongoing efforts to eradicate criminal conduct that threatens the Internet’s infrastructure and our ability to function in a digital world.”
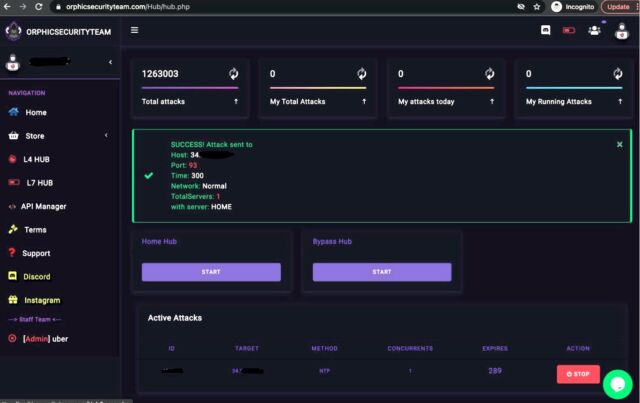
The services offered user interfaces that were essentially the same except for cosmetic differences. The screenshot below shows the web panel offered by orphicsecurityteam.com as of February 28. It allowed users to enter an IP address of a target, the network port, and the specific type of attack they wanted. The panel allowed users to pick various methods to amplify their attacks. Amplification involved bouncing a relatively small amount of specially crafted data at a third-party server in a way that caused the server to pummel the intended victim with payloads that were as much as 10,000 times bigger.
According to an affidavit filed on Wednesday, some of the services had staggering numbers of registered customers and attacks launched. For instance, logs indicate that a service called ipstressor.com had 2 million registered users, with 1 million of them conducting DDoSes. The service conducted or attempted to conduct 30 million DDoSes between 2014 and 2022. Securityteam.io allegedly conducted or attempted to conduct 1.3 million attacks and had 50,000 registered users. Prosecutors said astrostress.com conducted or attempted to conduct 700,000 DDoSes and had 30,000 registered users.
The domains seized were:
- anonboot.com
- api-sky.xyz
- astrostress.com
- booter.vip
- brrsecurity.org
- cyberstress.us
- dragonstresser.com
- dreams-stresser.io
- freestresser.so
- instant-stresser.com
- ipstress.vip
- ipstresser.wtf
- orphicsecurityteam.com
- ovhstresser.com
- quantum-stresser.net
- redstresser.cc
- royalstresser.com
- silentstress.net
- stresser.app
- stresser.best
- stresser.gg
- stresser.is
- stresser.net/stresser.org
- stresser.so
- stresser.top
- truesecurityservices.io
- vdos-s.co
- zerostresser.com
- ipstresser.xyz
- kraysec.com
- securityteam.io
- ipstresser.us
- stresser.shop
- exotic-booter.com
- mcstorm.io
- nightmarestresser.com
- shock-stresser.com stresserai.com
- sunstresser.com
The six individuals charged were:
- Jeremiah Sam Evans Miller, aka “John The Dev,” 23, of San Antonio, Texas, is charged with conspiracy to violate and violating the computer fraud and abuse act related to the alleged operation of a booter service named RoyalStresser.com (formerly known as Supremesecurityteam.com).
- Angel Manuel Colon Jr., aka “Anonghost720” and “Anonghost1337,” 37, of Belleview, Florida, is charged with conspiracy to violate and violating the computer fraud and abuse act related to the alleged operation of a booter service named SecurityTeam.io.
- Shamar Shattock, 19, of Margate, Florida, is charged with conspiracy for allegedly running a booter service known as Astrostress.com.
- Cory Anthony Palmer, 22, of Lauderhill, Florida, is charged with conspiracy for allegedly running a booter service known as Booter.sx.
- John M. Dobbs, 32 of Honolulu, Hawaii, is charged with aiding and abetting violations of the computer fraud and abuse act related to the alleged operation of a booter service named Ipstressor.com, also known as IPS, between 2009 and November 2022.
- Joshua Laing, 32, of Liverpool, New York, is charged with aiding and abetting violations of the computer fraud and abuse act related to the alleged operation of a booter service named TrueSecurityServices.io between 2014 and November 2022.
All six have yet to enter a plea and are expected to make their first court appearance early next year. . ." READ MORE

.jpg)

.jpg)


No comments:
Post a Comment