This functionality was incorporated into a Python script called Snappy that was published on Trustwave's GitHub repository and made available for free.
Snappy: A tool to detect rogue WiFi access points on open networks
Bill Toulas
- July 2, 2023
- 10:17 AM

Cybersecurity researchers have released a new tool called 'Snappy' that can help detect fake or rogue WiFi access points that attempts to steal data from unsuspecting people.
Attackers can create fake access points in supermarkets, coffee shops, and malls that impersonate real ones already established at the location. This is done to trick users into connecting to the rogue access points and relay sensitive data through the attackers' devices.
As the threat actors control the router, they can capture and analyze the transferred data by performing man-in-the-middle attacks.
Trustwave's security researcher and wireless/RF tech enthusiast Tom Neaves explains that spoofing the MAC addresses and SSIDs of legitimate access points on open networks is trivial for determined attackers.
The devices of those who revisit the locations of open wireless networks they previously connected to will automatically attempt to reconnect to a saved access point, and their owners will be oblivious to the fact that they connecting to a malicious device.
Snappy to the rescue
Neaves developed a tool that addresses this common risk, helping people detect if the access point they're using is the same as the one they used the last time (and every time) or if it might be a fake or rogue device.
By analyzing Beacon Management Frames, he found certain static elements such as the vendor, BSSID, supported rates, channel, country, max transmit power, and others that vary between different 802.11 wireless access points but are consistent for a specific access point over time.
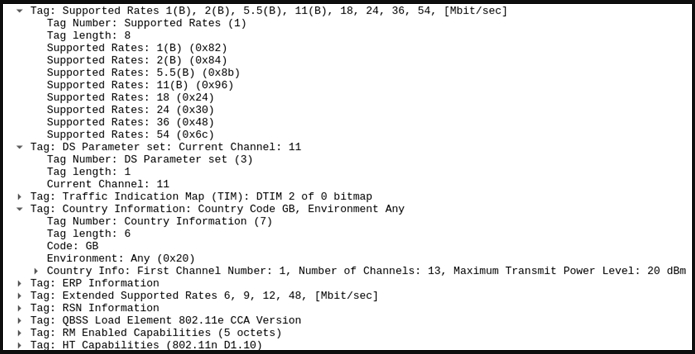 |
Matches mean that the access point is the same, hence trustworthy, while mismatches on the signature would mean that something has changed, and the access point might be rogue.
Apart from the mechanism to generate SHA256 hashes of wireless access points, Snappy can also detect access points created by Airbase-ng, a tool that attackers use to create fake access points to capture packets from connected users or even inject data into their network traffic.
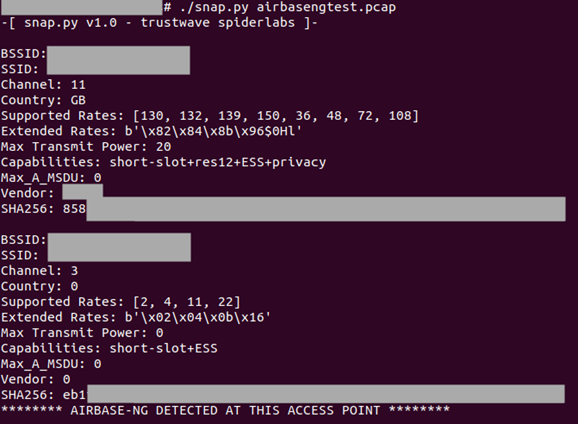
Android device owners may use Pydroid, QPython, or Termux to run Python scripts on their phones, while iOS users can choose between Pythonista, Carnets, and Juno.
Hopefully, Trustwave will consider publishing the tool in a more usable form for the wider audience soon.


No comments:
Post a Comment