Barracuda says its services and products are used by over 200,000 organizations worldwide, including high-profile ones such as Samsung, Delta Airlines, Kraft Heinz, and Mitsubishi.
CISA: New Submarine malware found on hacked Barracuda ESG appliances
- July 28, 2023
- 05:27 PM
- 0

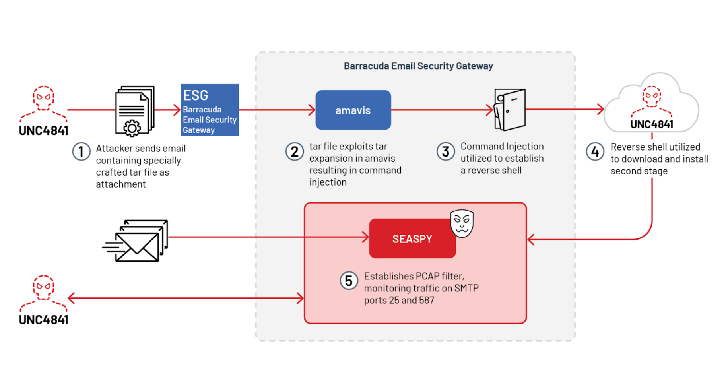
CISA says new malware known as Submarine was used to backdoor Barracuda ESG (Email Security Gateway) appliances on federal agencies' networks by exploiting a now-patched zero-day bug.
A suspected pro-China hacker group (UNC4841) deployed the backdoor in a series of data-theft attacks detected in May but active since at least October 2022.
Last month, Barracuda took an unconventional approach and offered replacement devices to all affected customers at no charge.
- This decision came after issuing a warning that all compromised ESG (Email Security Gateway) appliances needed immediate replacement instead of merely re-imaging them with new firmware.
Unknown backdoor found on hacked ESG appliances
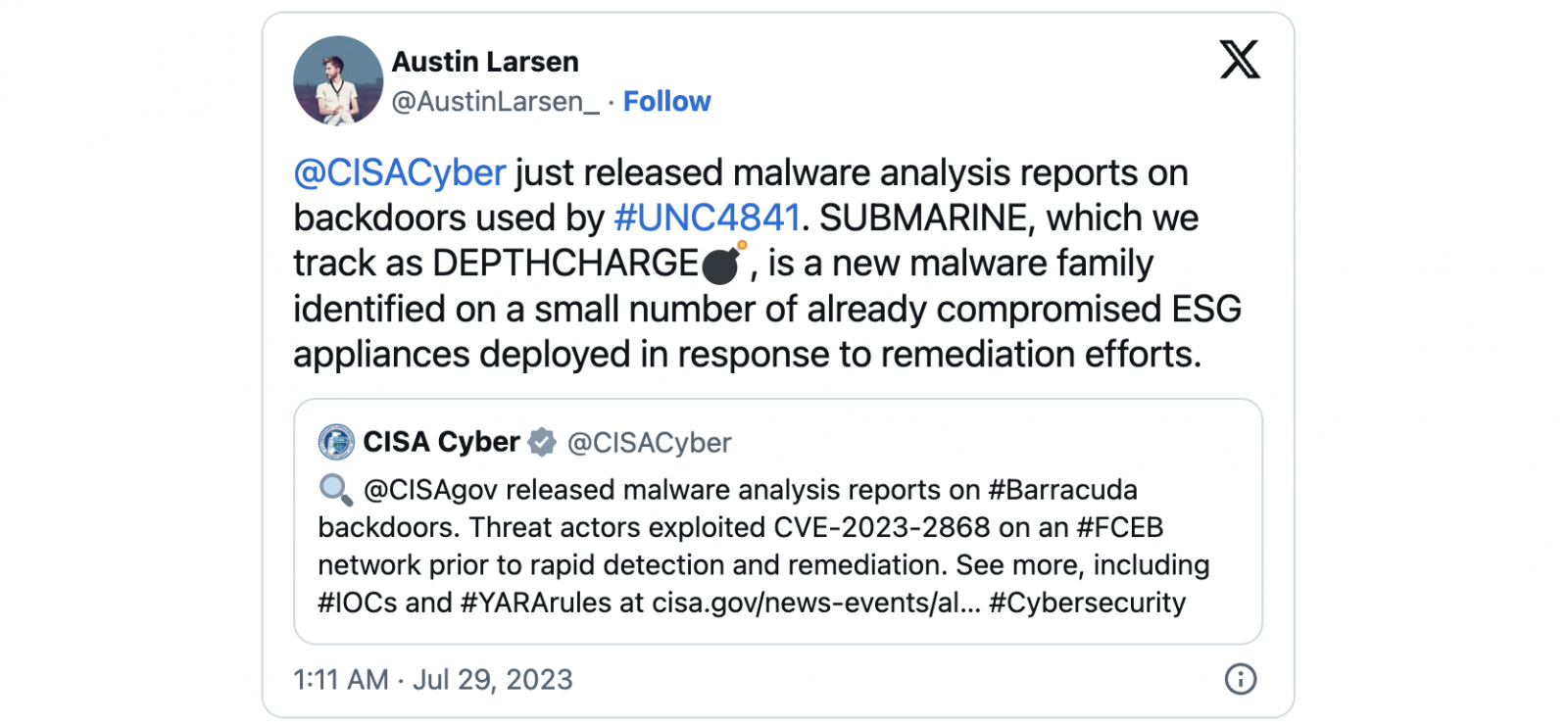
On Friday, CISA revealed that another new malware strain known as Submarine—and also tracked by Mandiant as DepthCharge—was found on the compromised appliances, a multi-component backdoor used for detection evasion, persistence, and data harvesting.
- "In addition to SUBMARINE, CISA obtained associated Multipurpose Internet Mail Extensions (MIME) attachment files from the victim. These files contained the contents of the compromised SQL database, which included sensitive information."
"This additional malware was utilized by the threat actor in response to Barracuda’s remediation actions in an attempt to create persistent access on customer ESG appliances. This malware appeared on a very small number of already compromised ESG appliances," Barracuda added.
"Barracuda’s recommendation is unchanged. Customers should discontinue use of the compromised ESG appliance and contact Barracuda support (support@barracuda.com) to obtain a new ESG virtual or hardware appliance."
The advice aligns with today's warning from CISA, which says that the "malware poses a severe threat for lateral movement."
Those who encounter suspicious activities linked to the Submarine malware and the Barracuda ESG attacks are urged to contact CISA's 24/7 Operations Center at Report@cisa.gov.
Barracuda says its services and products are used by over 200,000 organizations worldwide, including high-profile ones such as Samsung, Delta Airlines, Kraft Heinz, and Mitsubishi.




No comments:
Post a Comment