AI algorithm detects MitM attacks on unmanned military vehicles
Bill Toulas
- October 14, 2023
- 11:14 AM
- 0

MitM attacks are a type of cyberattack where the data traffic between two parties, in this case, the robot and its legitimate controllers, is intercepted either to eavesdrop or to inject false data in the stream.
- Such malicious attacks aim to interrupt the operation of unmanned vehicles, modify the transmitted instructions, and, in some cases, even assume control, instructing the robots to take dangerous actions.
"The robot operating system (ROS) is extremely susceptible to data breaches and electronic hijacking because it is so highly networked," comments Professor Anthony Finn, who participated in the study.
"The advent of Industry 4, marked by the evolution in robotics, automation, and the Internet of Things, has demanded that robots work collaboratively, where sensors, actuators, and controllers need to communicate and exchange information with one another via cloud services."
"The downside of this is that it makes them highly vulnerable to cyberattacks."
The university researchers developed an algorithm using machine learning techniques to detect these attempts and shut them down in seconds.
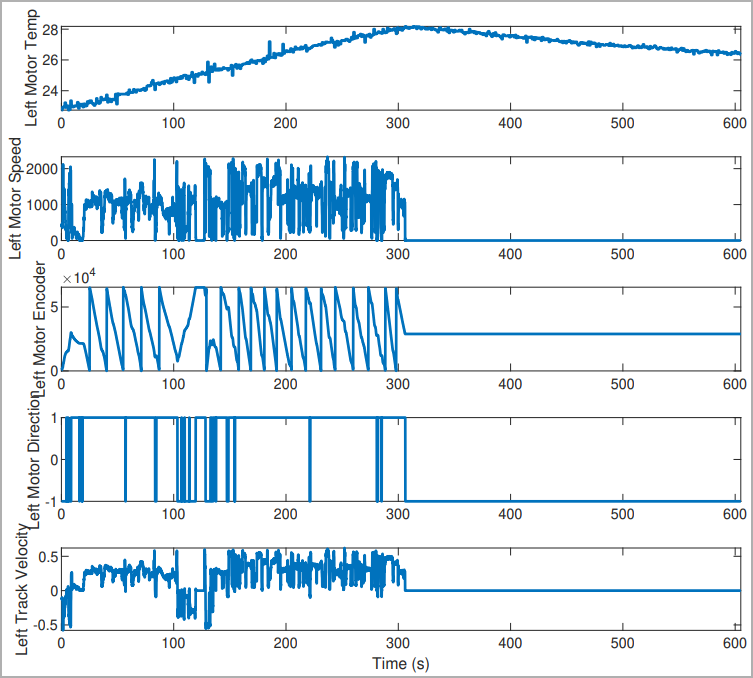

Discerning MitM attacks
Also, robotic systems can be compromised at various levels, from the core system to its sub-systems and their sub-components, causing an operational problem that could render the robot dysfunctional..
The university researchers developed a system that analyzed the robot's network traffic data to detect attempts to compromise it. This system uses node-based methods, scrutinizes packet data, and uses a flow-statistic-based system that reads metadata from the packet header.
The detailed technical paper released by the researchers delves into the specifics of the deep learning CNN (convolutional neural network) model that was developed for this purpose, comprising multiple layers and filters that raise the reliability of the cyberattack detection outcome.
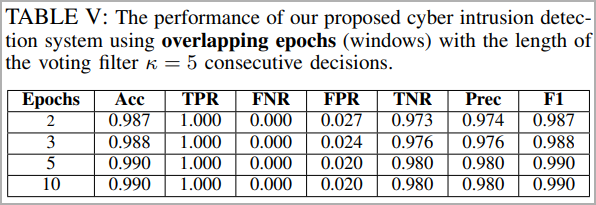
Real tests conducted on the replica bot with simulated cyber-attacks targeting various systems produced excellent results and high identification accuracy even after only 2-3 epochs of model training.
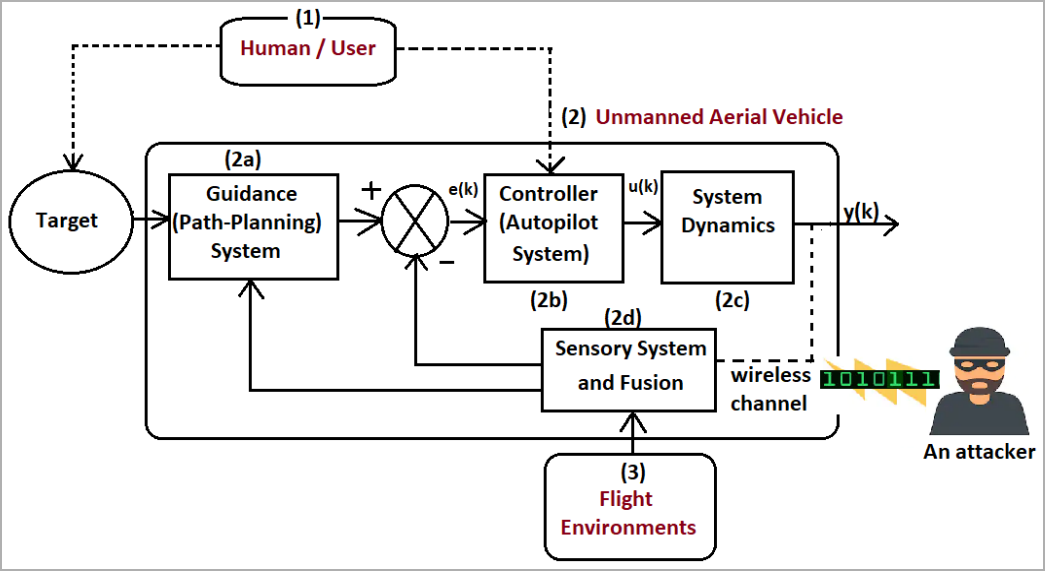
"We are also interested in investigating the efficacy of our intrusion detection system on different robotic platforms, such as unmanned aerial vehicles, whose dynamics are reasonably faster and more complex compared to a ground robot," concludes the paper published on IEEE's portal.






No comments:
Post a Comment