DUELING SEIZURES —
AlphV ransomware site is “seized” by the FBI. Then it’s “unseized.” And so on.
In a bizarre twist, both groups issue dueling notices to ransomware website.
The FBI spent much of Tuesday locked in an online tug-of-war with one of the Internet’s most aggressive ransomware groups after taking control of infrastructure the group has used to generate more than $300 million in illicit payments to date.
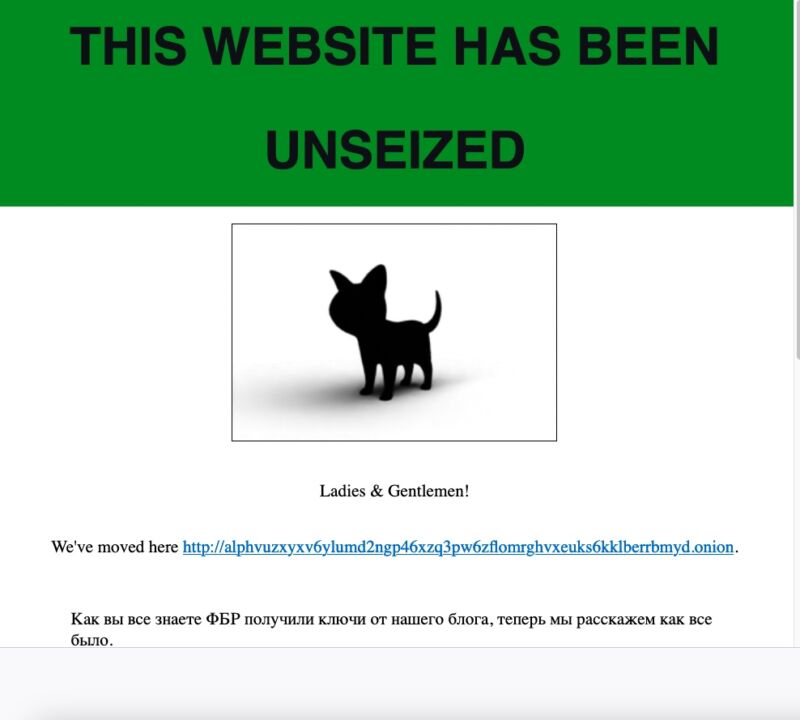
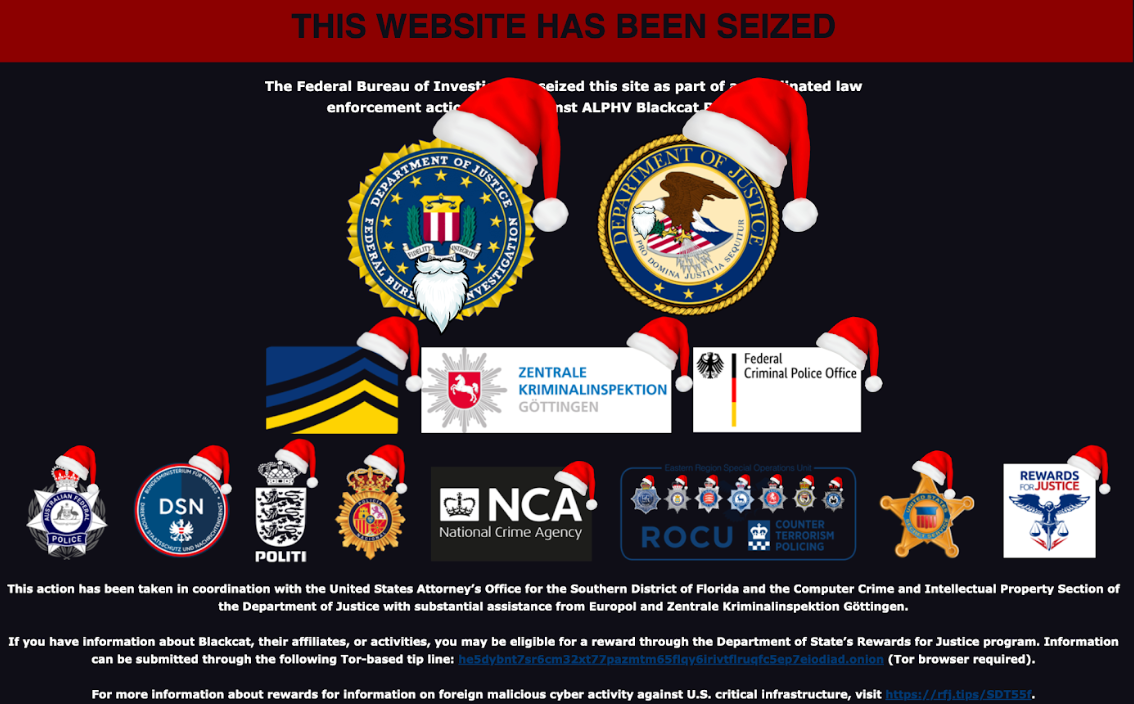
Early Tuesday morning, the dark-web site belonging to AlphV, a ransomware group that also goes by the name BlackCat, suddenly started displaying a banner that said it had been seized by the FBI as part of a coordinated law enforcement action. Gone was all the content AlphV had posted to the site previously.
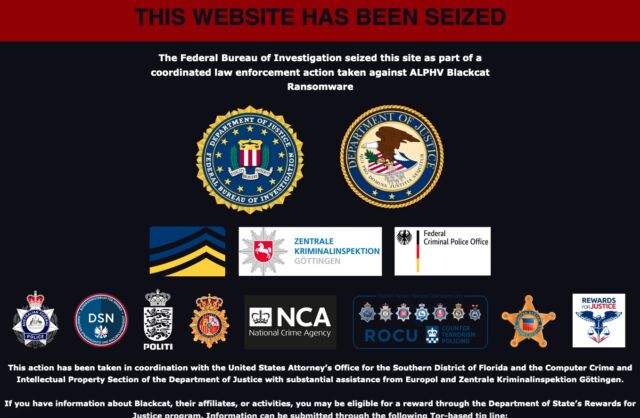
Around the same time, the Justice Department said it had disrupted AlphV’s operations by releasing a software tool that would allow roughly 500 AlphV victims to restore their systems and data. In all, Justice Department officials said, AlphV had extorted roughly $300 million from 1,000 victims.
An affidavit unsealed in a Florida federal court, meanwhile, revealed that the disruption involved FBI agents obtaining 946 private keys used to host victim communication sites. The legal document said the keys were obtained with the help of a confidential human source who had "responded to an advertisement posted to a publicly accessible online forum soliciting applicants for Blackcat affiliate positions."
“In disrupting the BlackCat ransomware group, the Justice Department has once again hacked the hackers,” Deputy Attorney General Lisa O. Monaco said in Tuesday’s announcement. “With a decryption tool provided by the FBI to hundreds of ransomware victims worldwide, businesses and schools were able to reopen, and health care and emergency services were able to come back online. We will continue to prioritize disruptions and place victims at the center of our strategy to dismantle the ecosystem fueling cybercrime.”
Within hours, the FBI seizure notice displayed on the AlphV dark-web site was gone. In its place was a new notice proclaiming: “This website has been unseized.” The new notice, written by AlphV officials, downplayed the significance of the FBI’s action. While not disputing the decryptor tool worked for 400 victims, AlphV officials said that the disruption would prevent data belonging to another 3,000 victims from being decrypted.
“Now because of them, more than 3,000 companies will never receive their keys.”
As the hours went on, the FBI and AlphV sparred over control of the dark-web site, with each replacing the notices of the other.
One researcher described the ongoing struggle as a “tug of Tor,” a reference to Tor, the network of servers that allows people to browse and publish websites anonymously. Like most ransomware groups, AlphV hosts its sites over Tor. Not only does this arrangement prevent law enforcement investigators from identifying group members, it also hampers investigators from obtaining court orders compelling the web host to turn over control of the site.
The only way to control a Tor address is with possession of a dedicated private encryption key. Once the FBI obtained it, investigators were able to publish Tuesday’s seizure notice to it. Since AlphV also maintained possession of the key, group members were similarly free to post their own content. Since Tor makes it impossible to change the private key corresponding to an address, neither side has been able to lock the other out.
With each side essentially deadlocked, AlphV has resorted to removing some of the restrictions it previously placed on affiliates. Under the common ransomware-as-a-service model, affiliates are the ones who actually hack victims. When successful, the affiliates use the AlphV ransomware and infrastructure to encrypt data and then negotiate and facilitate a payment by bitcoin or another cryptocurrency.
Up to now, AlphV placed rules on affiliates forbidding them from targeting hospitals and critical infrastructure. Now, those rules no longer apply unless the victim is located in the Commonwealth of Independent States—a list of countries that were once part of the former Soviet Union.
"Because of their actions, we are introducing new rules, or rather, we are removing ALL rules except one, you cannot touch the CIS, you can now block hospitals, nuclear power plants, anything, anywhere,” the AlphV notice said. The notice said that AlphV was also allowing affiliates to retain 90 percent of any ransom payments they get, and that ‘VIP’ affiliates would receive a private program on separate isolated data centers. The move is likely an attempt to stanch the possible defection by affiliates spooked by the FBI’s access to the AlphV infrastructure.
The back and forth has prompted some to say that the disruption failed, since AlphV retains control of its site and continues to possess the data it stole from victims. In a discussion on social media with one such critic, ransomware expert Allan Liska pushed back.
“The server and all of its data is still in possession of FBI—and ALPHV ain’t getting none of that back,” Liska, a threat researcher at security firm Recorded Future, wrote.
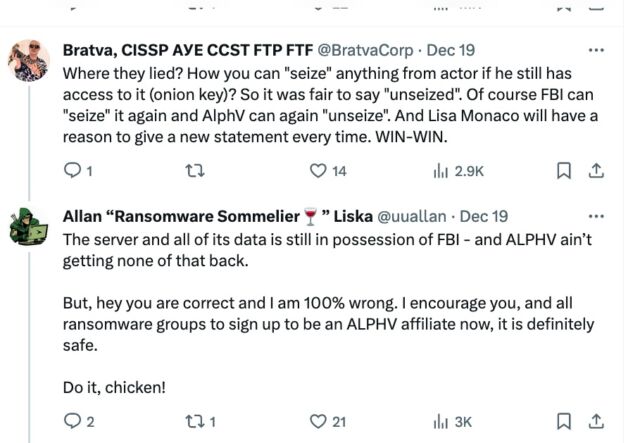
“But, hey you are correct and I am 100% wrong. I encourage you, and all ransomware groups to sign up to be an ALPHV affiliate now, it is definitely safe. Do it, Chicken!”
The Week in Ransomware - December 22nd 2023 - BlackCat hacked
- December 22, 2023
- 04:20 PM
- 0

The FBI revealed this week that they hacked the BlackCat/ALPHV ransomware operation, which raked in $300 million from over 1,000 victims. While quietly surveilling the ransomware gang, law enforcement retrieved decryption and Tor private keys.
Law enforcement says that they were able to help decrypt 400 victims for free using the retrieved decryptors and used the Tor private keys to seize the URLs for the gang's data leak site and negotiation sites.
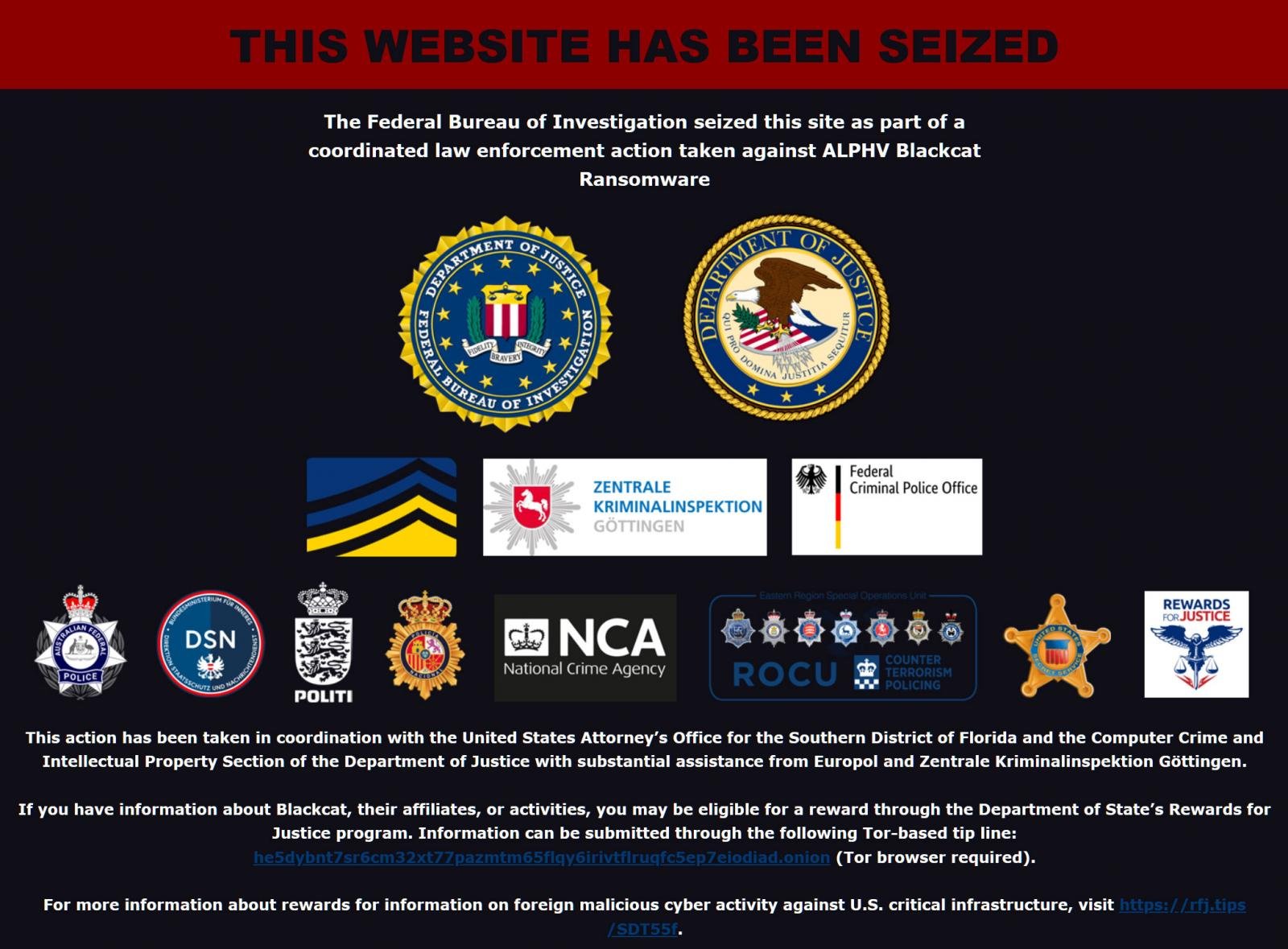
Source: BleepingComputer.com
Some have seen this constant change in ownership of the URL as a failed operation by law enforcement. However, retrieving 400 decryption keys and likely more data from the hacked servers has significantly tarnished the ransomware operation's reputation.
- BleepingComputer has learned that this has caused some affiliates to contact victims directly via email, as they have lost trust in the ransomware gang's ability to secure the servers.
- Others are said to have moved to competing ransomware operations, such as LockBit.
Source: 3xp0rt
Previous "ransomware cartels" allegedly created by Maze didn't succeed in helping the ransomware operation, as Ukrainian police arrested gang members after they rebranded as Egregor.
We also learned this week about new ransomware attacks or information about old ones, including:
- Akira claimed the ransomware attack on Nissan Australia.
- A ransomware attack on ESO Solutions exposed the data of 2.7 million people.
- University of Buenos Aires (UBA) suffered a ransomware cyberattack.
- Vans, North Face, Supreme owner VF Corp hit by ransomware attack.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @BleepinComputer, @demonslay335, @Seifreed, @billtoulas, @Ionut_Ilascu, @fwosar, @serghei, @LawrenceAbrams, @BrettCallow, @PRODAFT, @AShukuhi, @uuallan, @SophosXOps, @pcrisk, @3xp0rtblog, @oct0xor, @MorganDemboski, and @juanbrodersen.
December 18th 2023
Mortgage giant Mr. Cooper data breach affects 14.7 million people
Mr. Cooper is sending data breach notifications warning that a recent cyberattack has exposed the data of 14.7 million customers who have, or previously had, mortgages with the company.
FBI: Play ransomware breached 300 victims, including critical orgs
The Federal Bureau of Investigation (FBI) says the Play ransomware gang has breached roughly 300 organizations worldwide between June 2022 and October 2023, some of them critical infrastructure entities.
Vans and North Face owner VF Corp hit by ransomware attack
American global apparel and footwear giant VF Corporation, the owner of brands like Supreme, Vans, Timberland, and The North Face, has disclosed a security incident that caused operational disruptions
The UBA suffered a ransomware cyber attack: teachers and students cannot access the systems
The University of Buenos Aires (UBA) suffered a ransomware cyberattack , a type of malicious program that encrypts the victim's files, makes them inaccessible and demands a ransom money in exchange. Since Thursday, servers in part of the educational institution have been compromised and this prevents teachers and students from managing grades, enrolling in summer courses and more.
December 19th 2023
FBI disrupts Blackcat ransomware operation, creates decryption tool
The Department of Justice announced today that the FBI successfully breached the ALPHV ransomware operation's servers to monitor their activities and obtain decryption keys.
How the FBI seized BlackCat (ALPHV) ransomware’s servers
An unsealed FBI search warrant revealed how law enforcement hijacked the ALPHV/BlackCat ransomware operations websites and seized the associated URLs.
FBI: ALPHV ransomware raked in $300 million from over 1,000 victims
The ALPHV/BlackCat ransomware gang has made over $300 million in ransom payments from more than 1,000 victims worldwide as of September 2023, according to the Federal Bureau of Investigation (FBI).
Smoke and Mirrors: Understanding The Workings of Wazawaka
This research provides a comprehensive analysis of Wazawaka’s background, affiliations, and tactics in the threat landscape associated with his activities. It includes information about Wazawaka’s team and his close relations with other threat actors.
December 20th 2023
Healthcare software provider data breach impacts 2.7 million
ESO Solutions, a provider of software products for healthcare organizations and fire departments, disclosed that data belonging to 2.7 million patients has been compromised as a result of a ransomware attack.
Fake F5 BIG-IP zero-day warning emails push data wipers
The Israel National Cyber Directorate warns of phishing emails pretending to be F5 BIG-IP zero-day security updates that deploy Windows and Linux data wipers.
New BO Team ransomware
PCrisk found a new ransomware that appends the .bot extension and drops a ransom note named How To Restore Your Files.txt.
December 21st 2023
Akira, again: The ransomware that keeps on taking
Following our initial report on Akira ransomware, Sophos has responded to over a dozen incidents involving Akira impacting various sectors and regions. According to our dataset, Akira has primarily targeted organizations located in Europe, North America, and Australia, and operating in the government, manufacturing, technology, education, consulting, pharmaceuticals, and telecommunication sectors.
Windows CLFS and five exploits used by ransomware operators
Seeing a Win32k driver zero-day being used in attacks isn’t really surprising these days, as the design issues with that component are well known and have been exploited time and time again. But we had never seen so many CLFS driver exploits being used in active attacks before, and then suddenly there are so many of them captured in just one year.
New Phobos ransomware variant
PCrisk found a new ransomware that appends a unique extension and drops ransom notes named info.txt and info.hta.
New Tprc ransomware
PCrisk found a new ransomware that appends the .tprc extension and drops a ransom note named !RESTORE!.txt.
December 22nd 2023
Nissan Australia cyberattack claimed by Akira ransomware gang
Japanese car maker Nissan is investigating a cyberattack that targeted its systems in Australia and New Zealand, which may have let hackers access personal information.
That's it for this week! Hope everyone has a nice weekend!
>



No comments:
Post a Comment