It has also been available for deployment by bridge operators as part of a trial soft launch since June 2023, with the Tor Projects asking for more testers in October in "regions or using Internet providers where the Tor network is blocked or partially blocked."
Tor’s new WebTunnel bridges mimic HTTPS traffic to evade censorship
- March 12, 2024
- 12:49 PM
- 0

Tor bridges are relays not listed in the public Tor directory that keep the users' connections to the network hidden from oppressive regimes. While some countries, like China and Iran, have found ways to detect and block such connections, Tor also provides obfsproxy bridges, which add an extra layer of obfuscation to fight censorship efforts.
WebTunnel, the censorship-resistant pluggable transport inspired by the HTTPT probe-resistant proxy, takes a different approach.
- It makes it harder to block Tor connections by ensuring that the traffic blends in with HTTPS-encrypted web traffic.
"It works by wrapping the payload connection into a WebSocket-like HTTPS connection, appearing to network observers as an ordinary HTTPS (WebSocket) connection," said the Tor Project.
"So, for an onlooker without the knowledge of the hidden path, it just looks like a regular HTTP connection to a webpage server giving the impression that the user is simply browsing the web."
To be able to use a WebTunnel bridge, you'll first have to get bridge addresses from here and add them manually to Tor Browser for desktop through the following procedure:
- Open Tor Browser and go to the Connection preferences window (or click "Configure Connection").
- Click on "Add a Bridge Manually" and add the bridge addresses.
- Close the bridge dialog and click on "Connect."
- Note any issues or unexpected behavior while using WebTunnel.
The WebTunnel pluggable transport was first introduced in December 2022 as an integration that could be tested using a Tor Browser test build.
It has also been available for deployment by bridge operators as part of a trial soft launch since June 2023, with the Tor Projects asking for more testers in October in "regions or using Internet providers where the Tor network is blocked or partially blocked."
- "Right now, there are 60 WebTunnel bridges hosted all over the world, and more than 700 daily active users using WebTunnel on different platforms.
- However, while WebTunnel works in regions like China and Russia, it does not currently work in some regions in Iran," the Tor Project said.
"Our goal is to ensure that Tor works for everyone. Amid geopolitical conflicts that put millions of people at risk, the internet has become crucial for us to communicate, to witness and share what is happening around the world, to organize, to defend human rights, and to build solidarity."
___________________________________________________________________________________
On Friday, Roku first disclosed the data breach, warning that 15,363 customer accounts were hacked in a credential stuffing attack.
Over 15,000 hacked Roku accounts sold for 50¢ each to buy hardware
Bill Toulas
- March 11, 2024
- 01:49 PM
- 3

However, BleepingComputer has learned there is more to this attack, with threat actors selling the stolen accounts for as little as $0.50 per account, allowing purchasers to use stored credit cards to make illegal purchases.
On Friday, Roku first disclosed the data breach, warning that 15,363 customer accounts were hacked in a credential stuffing attack.
A credential stuffing attack is when threat actors collect credentials exposed in data breaches and then attempt to use them to log in to other sites, in this case, Roku.com.
This effectively locked a user out of the account, allowing the threat actors to make purchases using stored credit card information without the legitimate account holder receiving order confirmation emails.
"It appears likely that the same username/password combinations had been used as login information for such third-party services as well as certain individual Roku accounts," reads the data breach notice.
"As a result, unauthorized actors were able to obtain login information from third-party sources and then use it to access certain individual Roku accounts."
"After gaining access, they then changed the Roku login information for the affected individual Roku accounts, and, in a limited number of cases, attempted to purchase streaming subscriptions.
Additionally, the platform's security team investigated for any charges due to unauthorized purchases performed by the hackers and took steps to cancel the relevant subscriptions and refund the account holders.
After accessing the account, head to the Roku dashboard and review the activity, connected devices, and active subscriptions to ensure everything is legitimate.
Unfortunately, Roku does not support two-factor authentication, which prevents hijacks even in the case of credentials compromise.
Roku accounts are only worth 50 cents
- To generate revenue, Roku also allows customers to purchase streaming subscriptions directly through their Roku account. This enables customers to manage all their streaming services through one account.
- However, when adding a subscription, Roku stores customers' credit card information in their online accounts so that they can easily be used for future purchases.
- These programs allow you to import custom configs (configuration files) that are created to perform credential stuffing attacks against specific websites, such as Netflix, Steam, Chick-fil-A, and Roku.
- Successfully hacked accounts are then sold on stolen account marketplaces for as little as 50 cents, as seen below where 439 accounts are being sold.

Source: BleepingComputer
- The seller of these accounts provides information on how to change information on the account to make fraudulent purchases.
- Those who purchase the stolen accounts hijack them with their own information and use stored credit cards to purchase cameras, remotes, soundbars, light strips, and streaming boxes.
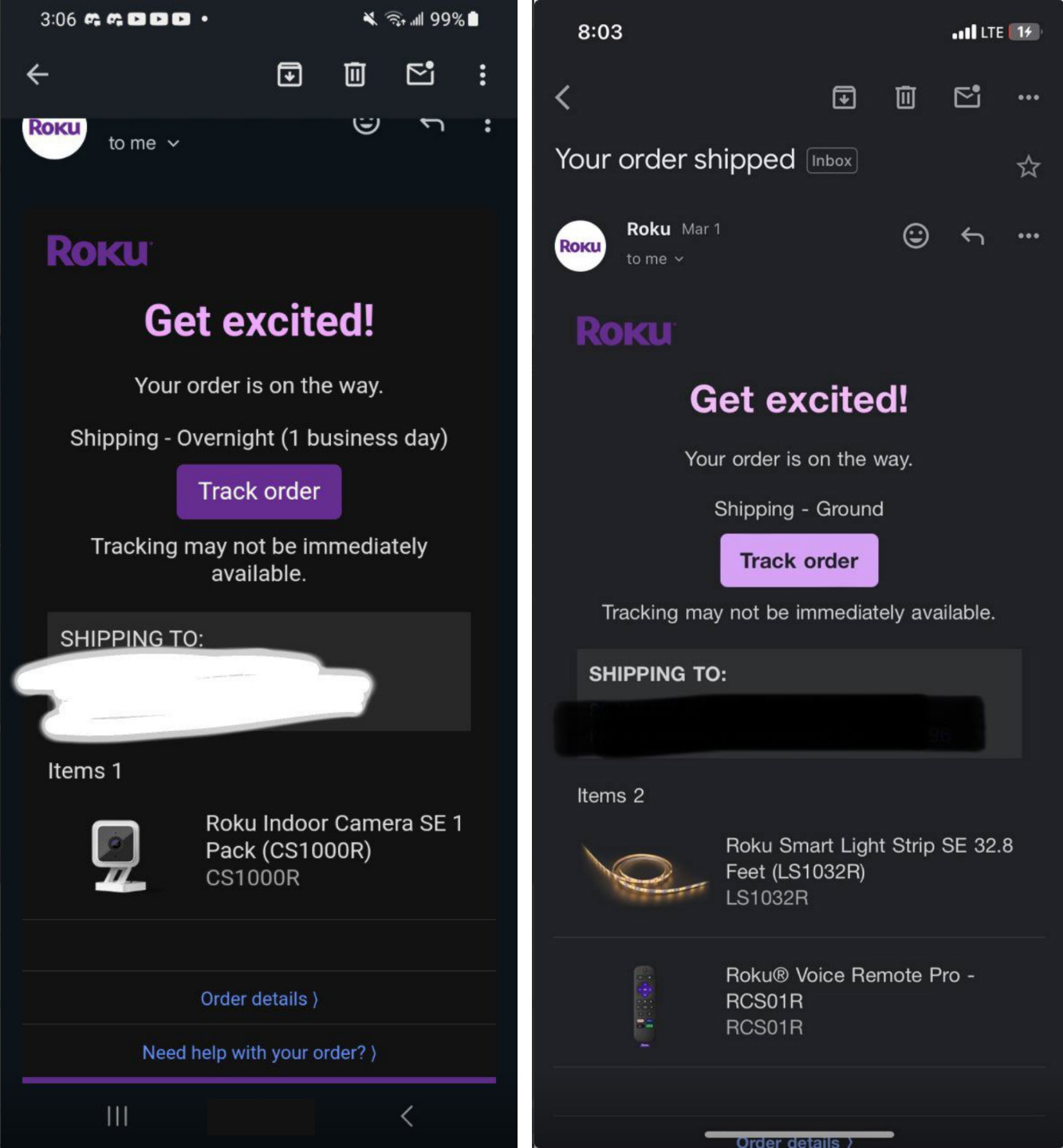
Source: BleepingComputer
Recently, Roku has been under fire for making changes to its "Dispute Resolution Terms" and preventing customers from using their streaming devices until they agree to them.
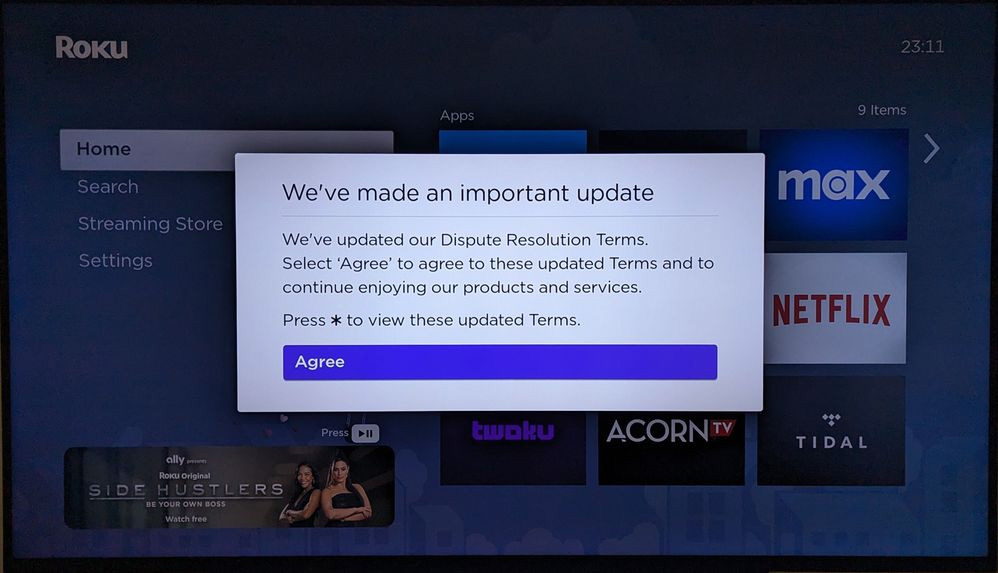
Source: AJCxZ0 on Roku Community Forums
However, as shown in the image above, there is no way to continue using a Roku streaming device without first agreeing to the terms.
A source told BleepingComputer that the new Dispute Resolution Terms are in part related to the ongoing credential stuffing attacks and financial fraud being conducted through the hacked accounts.
Update 3/11/24: After the publication of our article, Roku disputed what we we were told, stating that the new Dispute Resolution Terms are not related to the hacked accounts and fraudulent activities.
-
Stanford: Data of 27,000 people stolen in September ransomware attack
Stanford University says the personal information of 27,000 individuals was stolen in a ransomware attack impacting its Department of Public Safety (SUDPS) network.
- MARCH 12, 2024
- 03:49 PM
 0
0
-
Acer confirms Philippines employee data leaked on hacking forum
Acer Philippines confirmed that employee data was stolen in an attack on a third-party vendor who manages the company's employee attendance data after a threat actor leaked the data on a hacking forum.
- MARCH 12, 2024
- 03:31 PM
 0
0
-
Get Microsoft Office for $200 off with this StackCommerce deal
Get a lifetime license to Microsoft Office Professional 2021 for Windows or Microsoft Office Home & Business for Mac 2021 for $29.97.
- MARCH 12, 2024
- 02:09 PM
 0
0
-
Windows 11 KB5035853 update released, here's what's new
Microsoft has released the KB5035853 cumulative update for Windows 11 23H3 and 22H2, with 21 fixes and changes, including fixing a bug causing 0x800F0922 errors when installing updates.
- MARCH 12, 2024
- 02:08 PM
 0
0
-
Windows 10 KB5035845 update released with 9 new changes, fixes
Microsoft has released the KB5035845 cumulative update for Windows 10 21H2 and Windows 10 22H2, which includes nine new changes and fixes.
- MARCH 12, 2024
- 01:59 PM
 0
0
-
Microsoft March 2024 Patch Tuesday fixes 60 flaws, 18 RCE bugs
Today is Microsoft's March 2024 Patch Tuesday, and security updates have been released for 60 vulnerabilities, including eighteen remote code execution flaws.
- MARCH 12, 2024
- 01:52 PM
 1
1
-
Google paid $10 million in bug bounty rewards last year
Google awarded $10 million to 632 researchers from 68 countries in 2023 for finding and responsibly reporting security flaws in the company's products and services.
- MARCH 12, 2024
- 12:00 PM
 0
0
-
Over 12 million auth secrets and keys leaked on GitHub in 2023
GitHub users accidentally exposed 12.8 million authentication and sensitive secrets in over 3 million public repositories during 2023, with the vast majority remaining valid after five days.
- MARCH 12, 2024
- 11:23 AM
 0
0
-
Tuta Mail adds new quantum-resistant encryption to protect email
Tuta Mail has announced TutaCrypt, a new post-quantum encryption protocol to secure communications from powerful and anticipated decryption attacks.
- MARCH 11, 2024
- 05:21 PM
 1
1
-
Microsoft says Windows 10 21H2 support is ending in June
Microsoft announced today that it would end support for Windows 10 21H2 in June when the Enterprise and Education editions reach the end of service.
- MARCH 11, 2024
- 04:59 PM
 0
0
-
Okta says data leaked on hacking forum not from its systems
Okta denies that its company data was leaked after a threat actor shared files allegedly stolen during an October 2023 cyberattack on a hacker forum.
- MARCH 11, 2024
- 04:16 PM
 0
0
-
Researchers expose Microsoft SCCM misconfigs usable in cyberattacks
Security researchers have created a knowledge base repository for attack and defense techniques based on improperly setting up Microsoft's Configuration Manager, which could allow an attacker to execute payloads or become a domain controller.
- MARCH 11, 2024
- 03:15 PM
 0
0
-
Equilend warns employees their data was stolen by ransomware gang
New York-based securities lending platform EquiLend Holdings confirmed in data breach notification letters sent to employees that their data was stolen in a January ransomware attack.
- MARCH 11, 2024
- 02:00 PM
 0
0















No comments:
Post a Comment