-
US govt sanctions cybercrime gang behind massive 911 S5 botnet
The U.S. Treasury Department has sanctioned a cybercrime network comprising three Chinese nationals and three Thailand-based companies linked to a massive botnet controlling a residential proxy service known as "911 S5."
- MAY 28, 2024
- 03:02 PM
 0
0
US govt sanctions cybercrime gang behind massive 911 S5 botnet
- May 28, 2024
- 03:02 PM
- 0

The U.S. Treasury Department has sanctioned a cybercrime network comprising three Chinese nationals and three Thailand-based companies linked to a massive botnet controlling a residential proxy service known as "911 S5."
Researchers at the Canadian University of Sherbrooke found almost two years ago that this illegitimate residential proxy service lured potential victims by offering free VPN services to install malware designed to add their IP addresses to the 911 S5 botnet.
At the time, the botnet controlled approximately 120,000 residential proxy nodes from all over the world, all of which communicated with multiple command-and-control servers located offshore or hosted within a cloud server.
-
Ad blocker users say YouTube videos are now skipping to the end
Many users report that YouTube videos automatically skip to the end or muting video if they are using an ad blocker, making it impossible for them to watch the video.
- MAY 28, 2024
- 10:21 AM
 5
5
Ad blocker users say YouTube videos are now skipping to the end
Bill Toulas
- May 28, 2024
- 10:21 AM
- 5

Many users report that YouTube videos automatically skip to the end or muting video if they are using an ad blocker, making it impossible for them to watch the video.
The issue began yesterday, and although it does not appear to impact everyone, it is far from isolated, with affected users reporting that it affects all YouTube videos.
-
Christie’s confirms breach after RansomHub threatens to leak data
Christie's confirmed that it suffered a security incident earlier this month after the RansomHub extortion gang claimed responsibility and threatened to leak stolen data.
- MAY 28, 2024
- 12:10 PM
 0
0
Christie’s confirms breach after RansomHub threatens to leak data
Bill Toulas
- May 28, 2024
- 12:10 PM
- 0

Christie's confirmed that it suffered a security incident earlier this month after the RansomHub extortion gang claimed responsibility and threatened to leak stolen data.
Christie's is a prominent auction house with a history spanning 2.5 centuries. It operates in 46 countries and specializes in selling art, luxury items, and high-valued collectibles.
-
Microsoft links North Korean hackers to new FakePenny ransomware
Microsoft has linked a North Korean hacking group it tracks as Moonstone Sleet to FakePenny ransomware attacks, which have led to millions of dollars in ransom demands.
- MAY 28, 2024
- 01:58 PM
 0
0
Microsoft links North Korean hackers to new FakePenny ransomware
- May 28, 2024
- 01:58 PM
- 0

Microsoft has linked a North Korean hacking group it tracks as Moonstone Sleet to FakePenny ransomware attacks, which have led to millions of dollars in ransom demands.
While this threat group's tactics, techniques, and procedures (TTPs) largely overlapped with those of other North Korean attackers, it has also slowly adopted novel attack methods, as well as its own custom infrastructure and tooling.
Previously tracked as Storm-17, Moonstone Sleet has been observed attacking both financial and cyberespionage targets using trojanized software (e.g., PuTTY), malicious games and npm packages, custom malware loaders, and fake software development companies (e.g., StarGlow Ventures, C.C. Waterfall) set up to interact with potential victims on LinkedIn, Telegram, freelancing networks, or via email.
-
Update your cybersecurity skills with $684 off this training bundle
Training in cybersecurity is a smart career move. This 26-course cybersecurity and IT skills bundle helps you train at your pace for $69.99, $684 off the $754 MSRP.
- MAY 28, 2024
- 02:11 PM
 0
0
-
Russian indicted for selling access to US corporate networks
A 31-year-old Russian national named Evgeniy Doroshenko has been indicted for wire and computer fraud in the United States for allegedly acting as an "initial access broker" from February 2019 to May 2024.
- MAY 28, 2024
- 02:32 PM
 0
0
Russian indicted for selling access to US corporate networks
Bill Toulas
- May 28, 2024
- 02:32 PM
- 0

A 31-year-old Russian national named Evgeniy Doroshenko has been indicted for wire and computer fraud in the United States for allegedly acting as an "initial access broker" from February 2019 to May 2024.
An initial access broker (IAB) is a threat actor who breaches corporate networks and then sells that access to other threat actors, who commonly use the access to conduct data theft or ransomware attacks.
Doroshenko, allegedly known online by the aliases "FlankerWWH" and "Flanker," is accused of gaining unauthorized access to corporate networks and then offering to sell this access on Russian-language cybercrime forums.

Hackers target Check Point VPNs to breach enterprise networks

Hackers phish finance orgs using trojanized Minesweeper clone
State hackers turn to massive ORB proxy networks to evade detection
Ionut Ilascu
- May 22, 2024
- 01:37 PM
- 0

Security researchers are warning that China-linked state-backed hackers are increasingly relying on a vast proxy server network created from virtual private servers and compromised online devices for cyberespionage operations.
Called operational relay box (ORBs) networks, these proxy meshes are administered by independent cybercriminals that provide access to multiple state-sponsored actors (APTs).
ORBs are similar to botnets but they may be a hybrid of commercially leased VPS services and compromised devices, including end-of-life routers and other IoT products.
The growing use of ORBs by adversaries comes with challenges in both detection and attribution as the attack infrastructure is no longer controlled by the threat actor, who can cycle through nodes distributed over a broad geography.
Malicious proxy networks
One of them called ORB3/SPACEHOP is described as “a very active network leveraged by multiple China-nexus threat actors, including APT5 and APT15” for reconnaissance and vulnerability exploitation.
For instance, SPACEHOP was used in December 2022 to exploit CVE-2022-27518, a critical vulnerability in Citrix ADC and Gateway, which the National Security Agency (NSA) linked to APT5 (a.k.a. Manganese, Mulberry Typhoon, Bronze Fleetwood, Keyhole Panda, and UNC2630).
Mandiant researchers say that SPACEHOP is a provisioned network that uses a relay server hosted in Hong Kong or China by a cloud provider. It installs an open-source command and control (C2) framework that allows managing downstream nodes.
The relay nodes are typically cloned Linux-based images and their role is to proxy malicious traffic to an exit node that communicates with targeted victim environments.
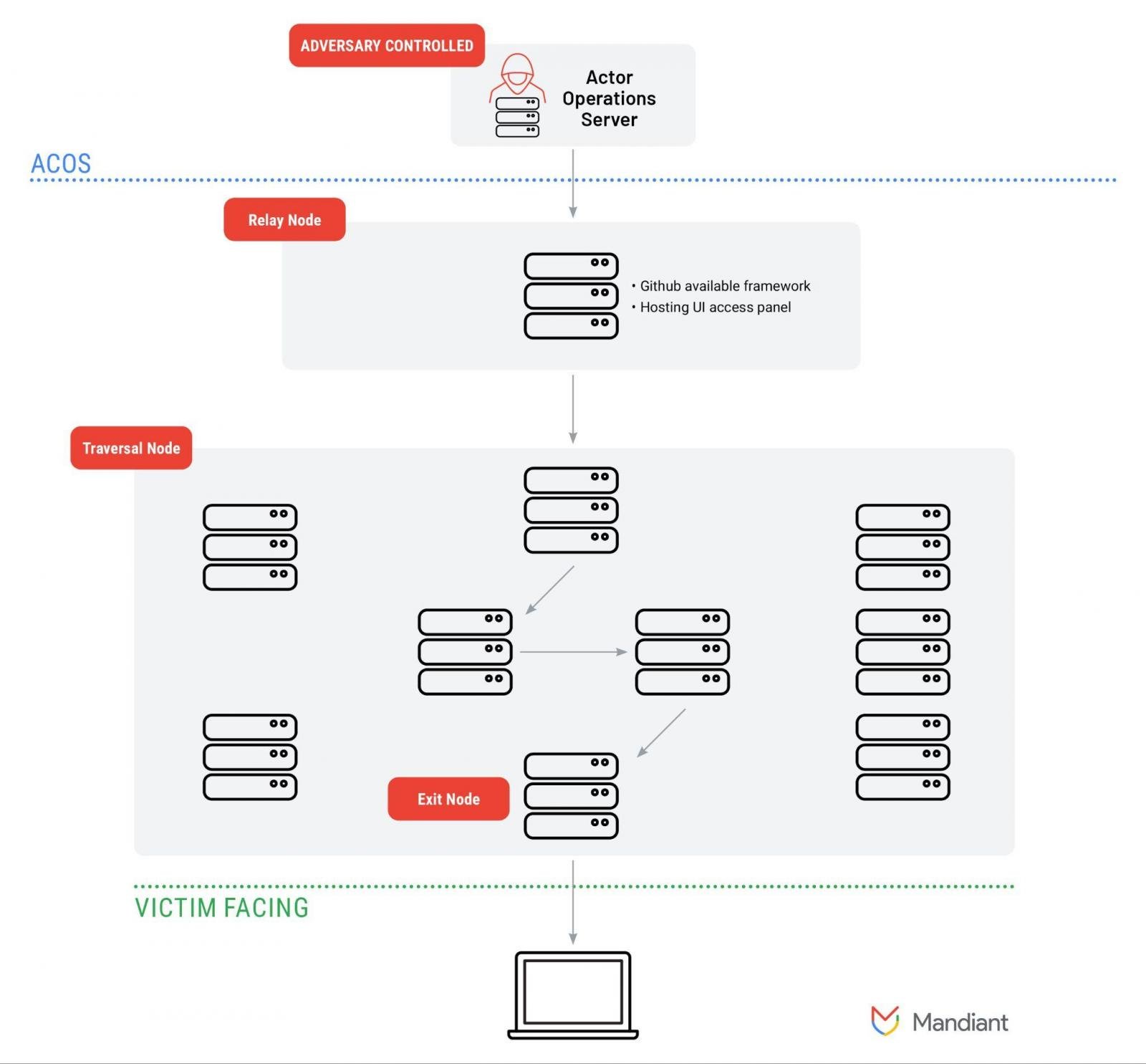
source: Mandiant
The researchers believe that this mesh is “used in cyber espionage campaigns by a diverse set of China-nexus threat actors” to obfuscate the traffic from the source.
The network appears to contain several subnetworks composed of compromised devices recruited by the router implant FLOWERWATER as well as other router-based payloads.
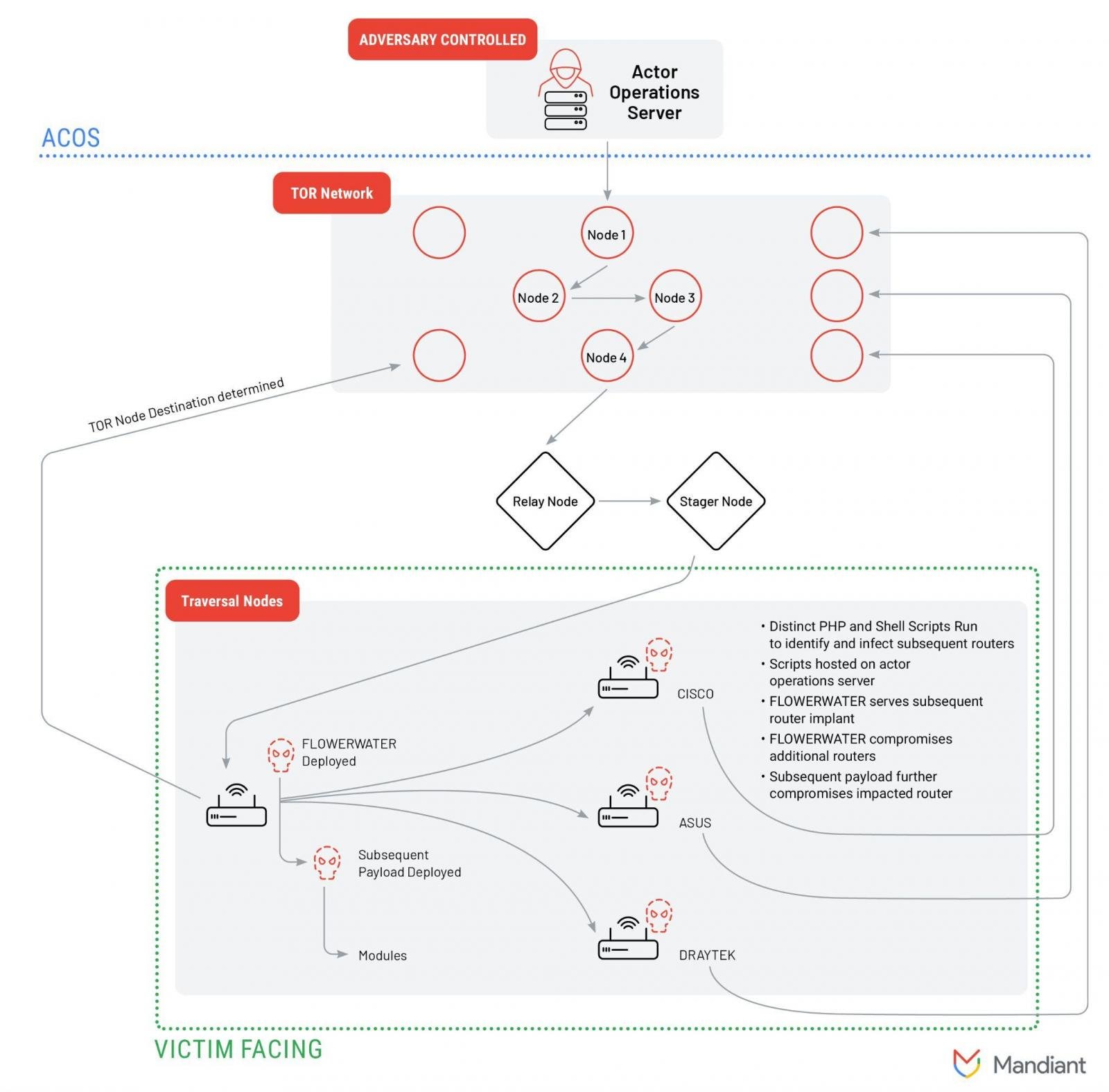
source: Mandiant
Although ORB2/FLORAHOX is used by multiple threat actors, Mandiant says that trusted third-party sources have reported clusters of activity attributed to China-linked adversaries APT31/Zirconium that focus on intellectual property theft.
“ORB2 represents a more complicated design including the relay of traffic through TOR nodes, provisioned VPS servers, and different types of compromised routers including CISCO, ASUS, and Draytek end-of-life devices” - Mandiant
Apart from FLOWERWATER, the researchers say that additional payloads and tools (MIPS router tunneler PETALTOWER, SHIMMERPICK bash scripts) are used to navigate the ORB2 network and pre-existing nodes based on command-line inputs.
Regardless of the type of devices used, an ORB network has a set of essential components that allow it to work properly:
- Adversary Controlled Operations Server (ACOS) - server for administering nodes in an ORB network
- Relay node - lets users authenticate to the network and relay traffic through the larger traversal pool on ORB nodes
- Traversal nodes - the main nodes composing an ORB network, obfuscate the origin of the traffic
- Exit/Staging nodes - used to launch attacks on targets
- Victim server: victim infrastructure communicating with the node on the ORB network
Enterprise defense challenges
Because of how malicious ORBs function, they provide stealth, resilience, and independence from the internet infrastructure in a country.
Multiple threat actors use these network infrastructures for limited periods, which impacts tracking them and attribution.
According to Mandiant, the lifespan of an IPv4 address of an ORB node can be as short as 31 days. This appears to be a feature of ORB network contractors in China, who can “cycle significant percentages of their compromised or leased infrastructure on a monthly basis.”
Defenders can miss malicious traffic from these networks because ORB administrators use Autonomous System Number (ASN) providers in various parts of the world.
Apart from making them more reliable, this also allows adversaries to target enterprises from devices in close geographic proximity, which raises less suspicions when analyzing traffic.
“One such example would be traffic from a residential ISP that is in the same geographic location as the target that is regularly used by employees and would be less likely to get picked up for manual review” - Mandiant
With attackers increasingly using ORBs, protecting enterprise environments becomes even more difficult since detection becomes more complex, attribution is more complicated, and indicators for adversary infrastructure are less useful for defenders.







No comments:
Post a Comment