Morgan Stanley discloses data breach that resulted from Accellion FTA hacks
Financial services firm says data was stolen by exploiting flaws discovered in December.
"Morgan Stanley suffered a data breach that exposed sensitive customer data, and it became the latest known casualty of hackers exploiting a series of now-patched vulnerabilities in Accellion FTA, a widely used third-party file-transfer service.
The data obtained included names, addresses, dates of birth, Social Security numbers, and affiliated corporate company names, Morgan Stanley said in a letter first reported by Bleeping Computer. A third-party service called Guidehouse, which provides account maintenance services to the financial services company, was in possession of the data at the time. Unknown hackers obtained the data by exploiting a series of hacks that came to light in December and January.
What took so long?
Morgan Stanley stated:
According to Guidehouse, the Accellion FTA vulnerability that led to this incident was patched in January 2021, within 5 days of the patch becoming available. Although the data was obtained by the unauthorized individual around that time, the vendor did not discover the attack until March of 2021, and did not discover the impact to Morgan Stanley until May 2021, due to the difficulty in retroactively determining which files were stored in the Accellion FTA appliance when the appliance was vulnerable. Guidehouse has informed Morgan Stanley that it found no evidence that Morgan Stanley’s data had been distributed beyond the threat actor.
U.S. cybersecurity firm FireEye discloses breach, theft of internal hacking tools
FireEye, one of the largest cybersecurity companies in the United States, said on Tuesday that is has been hacked, possibly by a government, leading to the theft of an arsenal of internal hacking tools typically reserved to privately test the cyber defenses of their own clients.
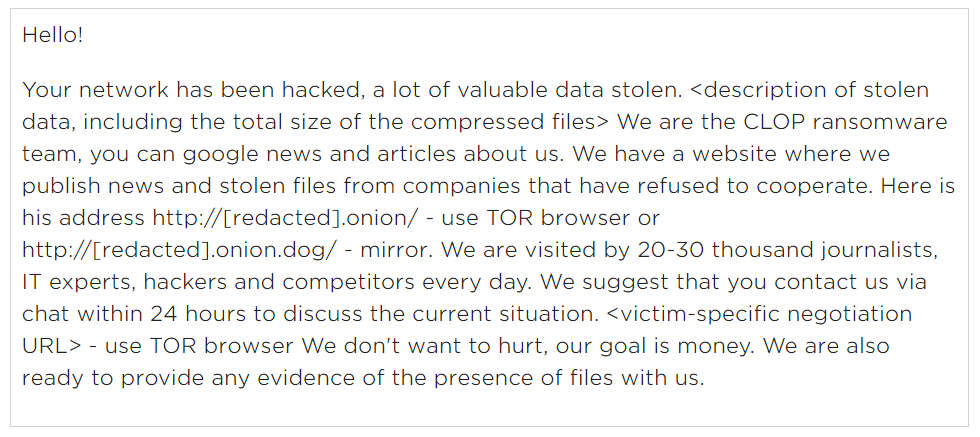
According to research Accellion commissioned from security firm Mandiant, unknown hackers exploited the vulnerabilities to install a web shell that gave them a text-based interface to install malware and issue other commands on compromised networks. Mandiant also said that many of the hacked organizations later received extortion demands that threatened to publish stolen data on a dark web site affiliated with the Cl0p ransomware group unless they paid a ransom.
The earliest detected activity in the hacking campaign came in mid-December when Mandiant identified the hackers exploiting an SQL injection vulnerability in the Accellion FTA. The exploit served as the initial intrusion point. Over time, the attackers exploited additional FTA vulnerabilities to gain enough control to install the web shell.
Mandiant researchers wrote:
In mid-December 2020, Mandiant responded to multiple incidents in which a web shell we call DEWMODE was used to exfiltrate data from Accellion FTA devices. The Accellion FTA device is a purpose-built application designed to allow an enterprise to securely transfer large files. The exfiltration activity has affected entities in a wide range of sectors and countries.
Across these incidents, Mandiant observed common infrastructure usage and TTPs, including exploitation of FTA devices to deploy the DEWMODE web shell. Mandiant determined that a common threat actor we now track as UNC2546 was responsible for this activity. While complete details of the vulnerabilities leveraged to install DEWMODE are still being analyzed, evidence from multiple client investigations has shown multiple commonalities in UNC2546's activities.
Other organizations that researchers suspect were breached through the vulnerabilities include oil company Shell, security firm Qualys, gasoline retailer RaceTrac Petroleum, international law firm Jones Day, the Washington state auditor, US bank Flagstar, US universities Stanford and the University of California, and the Reserve Bank of New Zealand. . .
No advance warning
In-the-wild exploits of the FTA vulnerabilities were first detected in late December. The company initially said that it had notified all affected customers and fixed the zero-day vulnerabilities that enabled the attack within 72 hours of learning of them. Later, Mandiant discovered two additional zero-days. . ."





No comments:
Post a Comment