Revealed: leak uncovers global abuse of cyber-surveillance weapon
Spyware sold to authoritarian regimes used to target activists, politicians and journalists, data suggests
Stephanie Kirchgaessner, Paul Lewis, David Pegg,Sam Cutler,Nina Lakhani and Michael Safi
Last modified on Sun 18 Jul 2021 16.39 EDT
". . . Human rights activists, journalists and lawyers across the world have been targeted by authoritarian governments using hacking software sold by the Israeli surveillance company NSO Group, according to an investigation into a massive data leak.
The investigation by the Guardian and 16 other media organisations suggests widespread and continuing abuse of NSO’s hacking spyware, Pegasus, which the company insists is only intended for use against criminals and terrorists.
Pegasus is a malware that infects iPhones and Android devices to enable operators of the tool to extract messages, photos and emails, record calls and secretly activate microphones.
The leak contains a list of more than 50,000 phone numbers that, it is believed, have been identified as those of people of interest by clients of NSO since 2016.
Forbidden Stories, a Paris-based nonprofit media organisation, and Amnesty International initially had access to the leaked list and shared access with media partners as part of the Pegasus project, a reporting consortium. . .Through its lawyers, NSO said the consortium had made “incorrect assumptions” about which clients use the company’s technology. It said the 50,000 number was “exaggerated” and the list could not be a list of numbers “targeted by governments using Pegasus”. 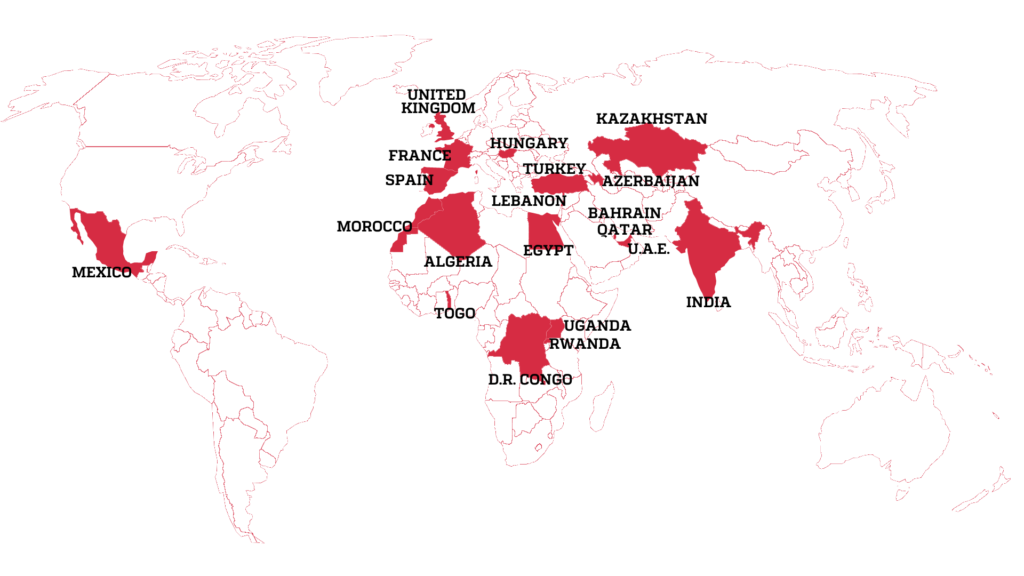
The lawyers said NSO had reason to believe the list accessed by the consortium “is not a list of numbers targeted by governments using Pegasus, but instead, may be part of a larger list of numbers that might have been used by NSO Group customers for other purposes”. After further questions, the lawyers said the consortium was basing its findings “on misleading interpretation of leaked data from accessible and overt basic information, such as HLR Lookup services, which have no bearing on the list of the customers' targets of Pegasus or any other NSO products ...
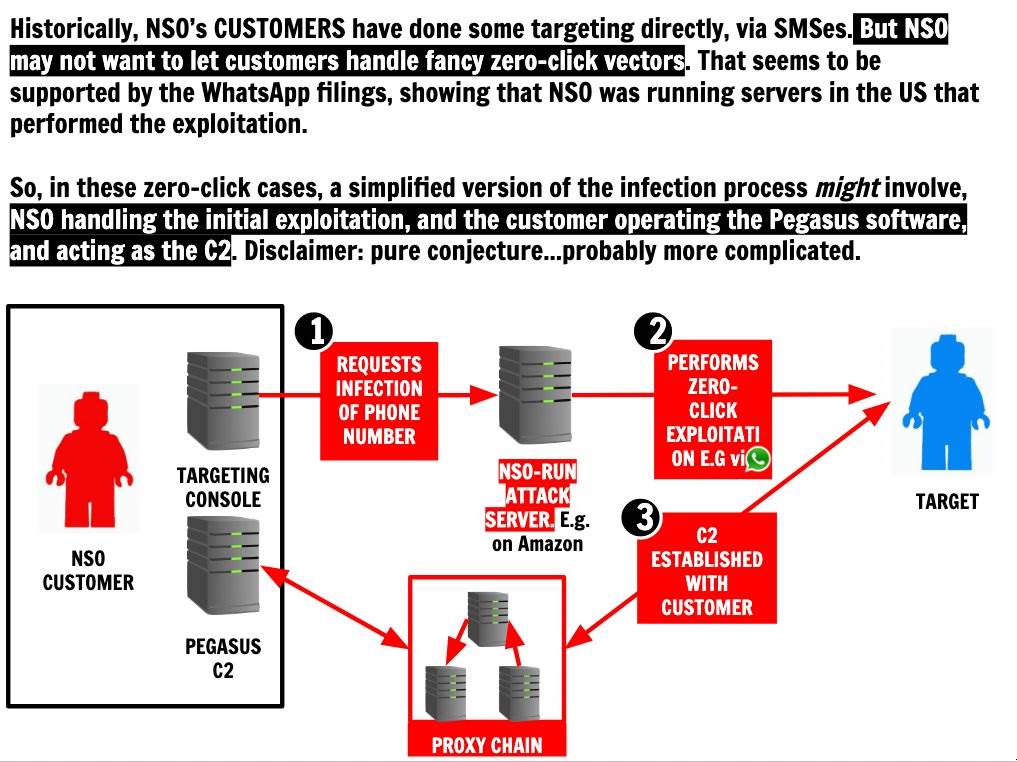
> Claudio Guarnieri, who runs Amnesty International’s Security Lab, said once a phone was infected with Pegasus, a client of NSO could in effect take control of a phone, enabling them to extract a person’s messages, calls, photos and emails, secretly activate cameras or microphones, and read the contents of encrypted messaging apps such as WhatsApp, Telegram and Signal. . . By accessing GPS and hardware sensors in the phone, he added, NSO’s clients could also secure a log of a person’s past movements and track their location in real time with pinpoint accuracy, for example by establishing the direction and speed a car was travelling in.
The latest advances in NSO’s technology enable it to penetrate phones with “zero-click” attacks, meaning a user does not even need to click on a malicious link for their phone to be infected.
_____________________________________________________________________________
Amnesty, research groups map out global reach of Israeli NSO Group’s spyware
Pegasus software ‘has been used in some of the most insidious digital attacks on human rights defenders,’ Amnesty International charges; NSO says claims are ‘recycled,’ inaccurate
"The ‘Digital Violence: How the NSO Group Enables State Terror’ platform that details the operations of Israeli startup NSO Group (Courtesy)
An interactive online platform created by research agency Forensic Architecture, and supported by Amnesty International and the internet watchdog group Citizen Lab, has mapped the global spread of the spyware Pegasus, made by Israeli cybersecurity firm NSO Group.
Titled “Digital Violence: How the NSO Group Enables State Terror,” the website shows, for what is said to be the first time, geographic areas in which Pegasus spyware has been deployed worldwide, and interviews lawyers, activists and other civil society figures about their experiences.
Forensic Architecture, based in the University of London, investigates human rights violations by states, police forces and corporations.
“The company’s Pegasus spyware has been used in some of the most insidious digital attacks on human rights defenders,” Amnesty International said on its website. “When Pegasus is surreptitiously installed on a person’s phone, an attacker has complete access to a phone’s messages, emails, media, microphone, camera, calls and contacts.”
“The investigation reveals the extent to which the digital domain we inhabit has become the new frontier of human rights violations, a site of state surveillance and intimidation that enables physical violations in real space,” said Forensic Architecture researcher Shourideh Molavi in the Amnesty statement.
Guarnieri has identified evidence NSO has been exploiting vulnerabilities associated with iMessage, which comes installed on all iPhones, and has been able to penetrate even the most up-to-date iPhone running the latest version of iOS. His team’s forensic analysis discovered successful and attempted Pegasus infections of phones as recently as this month. . ."
_____________________________________________________________________________
RELATED CONTENT ON THIS BLOG
An Opinion Piece in the New York Times caught your MesaZona blogger's eye today.What Poses a Greater Privacy Threat Than Facebook? Spyware
A lawsuit that is a genuine step forward for drawing attention to the spyware market and the need for stricter regulation of private surveillance companies like NSO.
Pegasus is a spyware that can be installed on devices running certain versions of iOS, Apple's mobile operating system, developed by the Israeli cyberarms firm, NSO Group
_________________________________________________________________________________
 FROM KASPERSKY LABS Link > https://www.kaspersky.com/blog/pegasus-spyware
FROM KASPERSKY LABS Link > https://www.kaspersky.com/blog/pegasus-spywareThe keyword here is allegedly. There actually is malware in the wild that targets iOS users — it’s been proved a number of times, and in August 2016 researchers proved it again by revealing the existence of Pegasus, spyware capable of hacking any iPad or iPhone, harvesting data about the victim, and establishing surveillance on them.
That discovery made the whole cybersecurity world… uneasy.
At our Security Analyst Summit, researchers from Lookout revealed that Pegasus exists not only for iOS, but for Android as well. The Android version is different in some ways from its iOS predecessor.
Let’s shed some light on Pegasus and explain why we use the word “ultimate” to describe it.
____________________________________________________________________________
RELATED CONTENT ON THIS BLOG
28 February 2017
Orbital ATK's Flight Systems Group 2016 Highlights + Updates
=======================================================================
Updates included from Businesswire
27 Feb 2017
Orbital ATK Artillery Precision Guidance Kit Surpasses 10,000 Units Delivered







No comments:
Post a Comment