The US Cybersecurity and Infrastructure Security Agency (CISA) said on Friday evening it was “taking action to understand and address the recent supply-chain ransomware attack against Kaseya” and providers that employ their software.
Supply chain attack of Kaseya, commonly used in managed service provider environments in the United States, leading to mass ransomware event.Details in link and thread as they develop:https://t.co/YStENYMTdW
— Kevin Beaumont (@GossiTheDog) July 2, 2021
Kaseya has taken their cloud service offline. It initially said 200 companies were affected, but later changed that to “a small number.” Neither the company nor CISA have said anything about how the hackers may have gained access.
John Hammond of the cybersecurity firm Huntress Labs said “thousands” of computers were affected. “We currently have three Huntress partners who are impacted with roughly 200 businesses that have been encrypted,” he said, calling it a “colossal and devastating supply chain attack.” . . .
While the US government has blamed last year’s SolarWinds breach on Russia – Moscow has denied any involvement, calling the insinuations “absurd”and “pathetic” – the Kaseya hack seemed to be the work of REvil, a group many US researchers have described as “Russian-speaking.”
“Based on everything we are seeing right now, we strongly believe this (is) REvil/Sodinikibi,” Hammond said. . .
While the White House did not blame Russia for the JBS attack, White House Press Secretary Jen Psaki said that “responsible states do not harbour ransomware criminals” after the FBI pointed to REvil as the likely culprit behind the breach.
Cyber-sleuths also don’t believe the timing of the reported Kaseya hack was an accident. It came as the US was gearing up for a three-day weekend to celebrate the Independence Day holiday, and many companies as well as government agencies were closing up shop early.
“There’s zero doubt in my mind that the timing here was intentional,” Jake Williams of Rendition Infosec told AP.
Washington has repeatedly accused Moscow of either orchestrating cyber attacks on US infrastructure or “harboring criminal entities” that do so. Last month’s summit between US President Joe Biden and Russian President Vladimir Putin in Geneva prominently featured a discussion on hacking.
WHO'S ATTACKING WHO? . .On Friday morning, the Russian Embassy in Washington issued a statement noting that “constant attacks on critical infrastructure in Russia” are coming from US soil, and expressed hope the Americans would “abandon the practice of unfounded accusations and focus on professional work with Russian experts to strengthen international information security.”
=========================================================================
Who’s Attacking Whom?
Realtime Attack Trackers
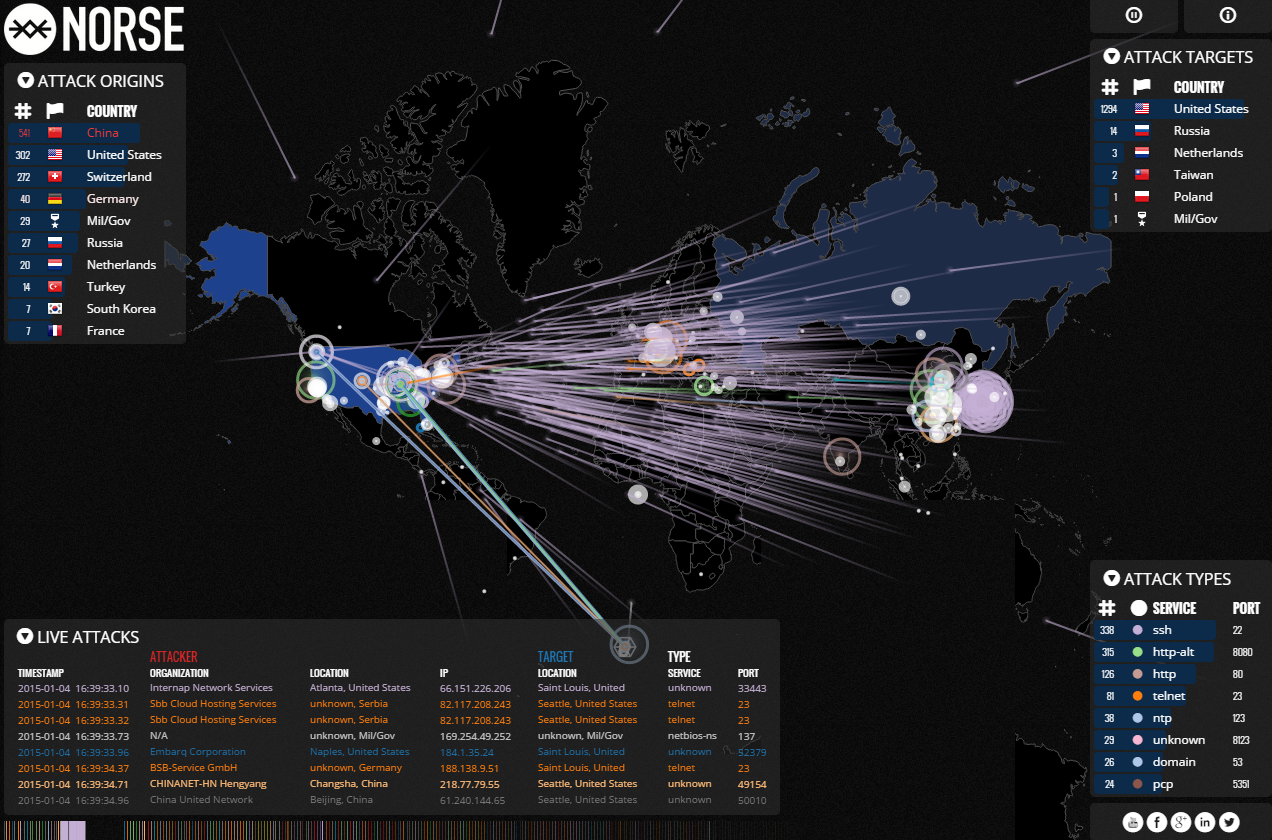
It seems nearly every day we’re reading about Internet attacks aimed at knocking sites offline and breaking into networks, but it’s often difficult to visualize this type of activity. In this post, we’ll take a look at multiple ways of tracking online attacks and attackers around the globe and in real-time.
A couple of notes about these graphics. Much of the data that powers these live maps is drawn from a mix of actual targets and “honeypots,” decoy systems that security firms deploy to gather data about the sources, methods and frequency of online attacks. Also, the organizations referenced in some of these maps as “attackers” typically are compromised systems within those organizations that are being used to relay attacks launched from someplace else.
The Cyber Threat Map from FireEye recently became famous in a 60 Minutes story on cyberattacks against retailers and their credit card systems. This graphic reminds me of the ICBM monitors from NORAD, as featured in the 1984 movie War Games (I’m guessing that association is intentional). Not a lot of raw data included in this map, but it’s fun to watch.





No comments:
Post a Comment