By Bill Toulas
September 19, 2024
09:57 AM

- A curious aspect is the presence of a "LOVE" ASCII string in the generated ICMP packets, which adds further speculation as to their purpose and makes the case more intriguing.
Characteristics of the noise storms
GreyNoise observes large waves of spoofed internet traffic coming from millions of spoofed IP addresses from various sources such as QQ, WeChat, and WePay.
- The "storms" create massive traffic directed to specific internet service providers like Cogent, Lumen, and Hurricane Electric but avoid others, most notably Amazon Web Services (AWS).
The traffic mainly focuses on TCP connections, particularly targeting port 443, but there's also an abundance of ICMP packets, lately including an embedded ASCII string "LOVE" within them, as shown below.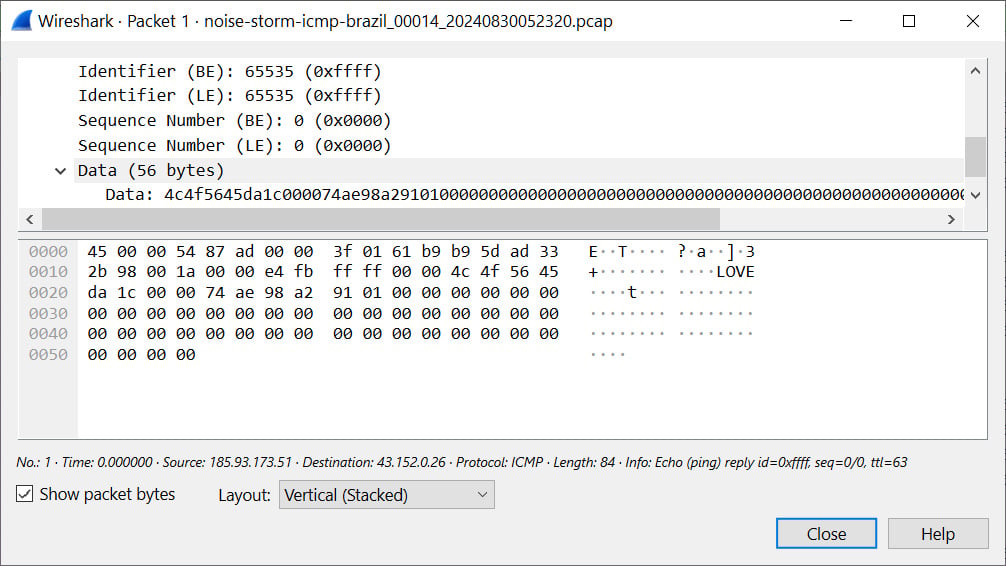
GreyNoise observes large waves of spoofed internet traffic coming from millions of spoofed IP addresses from various sources such as QQ, WeChat, and WePay.
- The "storms" create massive traffic directed to specific internet service providers like Cogent, Lumen, and Hurricane Electric but avoid others, most notably Amazon Web Services (AWS).
Source: BleepingComputer
The Time to Live (TTL) values, which dictate how long a packet stays on the network before it's discarded, are set between 120 and 200 to resemble realistic network hops.
All in all, the form and characteristics of these "noise storms" indicate a deliberate effort by a knowledgeable actor rather than a large-scale side effect of a misconfiguration.
This strange traffic mimics legitimate data streams, and while it's not known if it's malicious, its true purpose remains a mystery.
GreyNoise published packet captures (PCAPs) for two recent noise storm events on GitHub, inviting cybersecurity researchers to join in the investigation and contribute their insights or independent discoveries that will help solve this mystery.
"Noise Storms are a reminder that threats can manifest in unusual and bizarre ways, highlighting the need for adaptive strategies and tools that go beyond traditional security measures," underlines GreyNoise.
You can learn more about these Noise Storms in GreyNoise's recent Storm Watch video, shown below.
===
-
Get started in ethical hacking with this $45 online course bundle
The Complete Ethical Hacking Boot Camp offers a practical approach to preparing for specialized cybersecurity positions, particularly in penetration testing and security analysis, and It's also on sale for $44.99 (reg. $143).
- September 22, 2024
- 08:12 AM
 0
0
-
Global infostealer malware operation targets crypto users, gamers
A massive infostealer malware operation encompassing thirty campaigns targeting a broad spectrum of demographics and system platforms has been uncovered, attributed to a cybercriminal group named "Marko Polo."
- September 21, 2024
- 12:45 PM
 0
0
-
This cybersecurity study bundle blends theory with hands-on training
Invest in your cybersecurity education. Get the A to Z Cyber Security and IT Certification Training Bundle for $45.99 (reg. $372).
- September 21, 2024
- 08:17 AM
 0
0
-
Microsoft ends development of Windows Server Update Services (WSUS)
Microsoft has officially announced that Windows Server Update Services (WSUS) is now deprecated, but plans to maintain current functionality and continue publishing updates through the channel.
- September 20, 2024
- 04:43 PM
 0
0
-
Windows Server 2025 previews security updates without restarts
Microsoft announced today that Hotpatching is now available in public preview for Windows Server 2025, allowing installation of security updates without restarting.
- September 20, 2024
- 03:07 PM
 1
1
-
Disney ditching Slack after massive July data breach
The Walt Disney Company is reportedly ditching Slack after a July data breach exposed over 1TB of confidential messages and files posted to the company's internal communication channels.
- September 20, 2024
- 02:33 PM
 0
0
-
Ukraine bans Telegram on military, govt devices over security risks
Ukraine's National Coordination Centre for Cybersecurity (NCCC) has restricted the use of the Telegram messaging app within government agencies, military units, and critical infrastructure, citing national security concerns.
- September 20, 2024
- 01:37 PM
 4
4
-
Dell investigates data breach claims after hacker leaks employee info
Dell has confirmed to BleepingComputer that they are investigating recent claims that it suffered a data breach after a threat actor leaked the data for over 10,000 employees.
- September 20, 2024
- 12:30 PM
 0
0
-
macOS Sequoia change breaks networking for VPN, antivirus software
Users of macOS 15 'Sequoia' are reporting network connection errors when using certain endpoint detection and response (EDR) or virtual private network (VPN) solutions, and web browsers.
- September 20, 2024
- 11:45 AM
 0
0
-
Clickbaity or genius? 'BF cheated on you' QR codes pop up across UK
A new wave of QR codes has popped up across UK claiming to share a video of a boyfriend who "cheated" on a girl named Emily last night. Clickbaity or genius?
- September 20, 2024
- 10:10 AM
 0
0
-
Study for GSEC, CISSP, and more certifications with this $56 bundle deal
Prepare for your next IT job with over 90 cybersecurity courses through an InfoSec4TC Lifetime Membership for $55.97 (reg. $280).
- September 20, 2024
- 07:14 AM
 0
0
-
Suspects behind $230 million cryptocurrency theft arrested in Miami
Two suspects were arrested in Miami this week and charged with conspiracy to steal and launder over $230 million in cryptocurrency using crypto exchanges and mixing services.
- September 19, 2024
- 06:57 PM
 1
1
-
CISA warns of actively exploited Apache HugeGraph-Server bug
The U.S. Cybersecurity and Infrastructure Agency (CISA) has added five flaws to its Known Exploited Vulnerabilities (KEV) catalog, among which is a remote code execution (RCE) flaw impacting Apache HugeGraph-Server.
- September 19, 2024
- 06:53 PM
 0
0
-
Microsoft Edge will flag extensions causing performance issues
Microsoft is testing a new feature in the Edge browser called the "extension performance detector," which warns you when browser extensions cause performance issues on web pages you visit.
- September 19, 2024
- 04:56 PM
 0
0
-
Tor says it’s "still safe" amid reports of police deanonymizing users
The Tor Project is attempting to assure users that the network is still safe after a recent investigative report warned that law enforcement from Germany and other countries are working together to deanonymize users through timing attacks.
- September 19, 2024
- 03:15 PM
 5
5

.jfif)

















No comments:
Post a Comment