REvil ransomware is back in full attack mode and leaking data
REvil's disappearance act
REvil shut down their infrastructure and completely disappeared after their biggest caper yet - a massive attack on July 2nd that encrypted 60 managed service providers and over 1,500 businesses using a zero-day vulnerability in the Kaseya VSA remote management platform.
REvil then demanded $50 million for a universal decryptor for all Kaseya victims, $5 million for an MSP's decryption, and a $44,999 ransom for individual file encryption extensions at affected businesses.
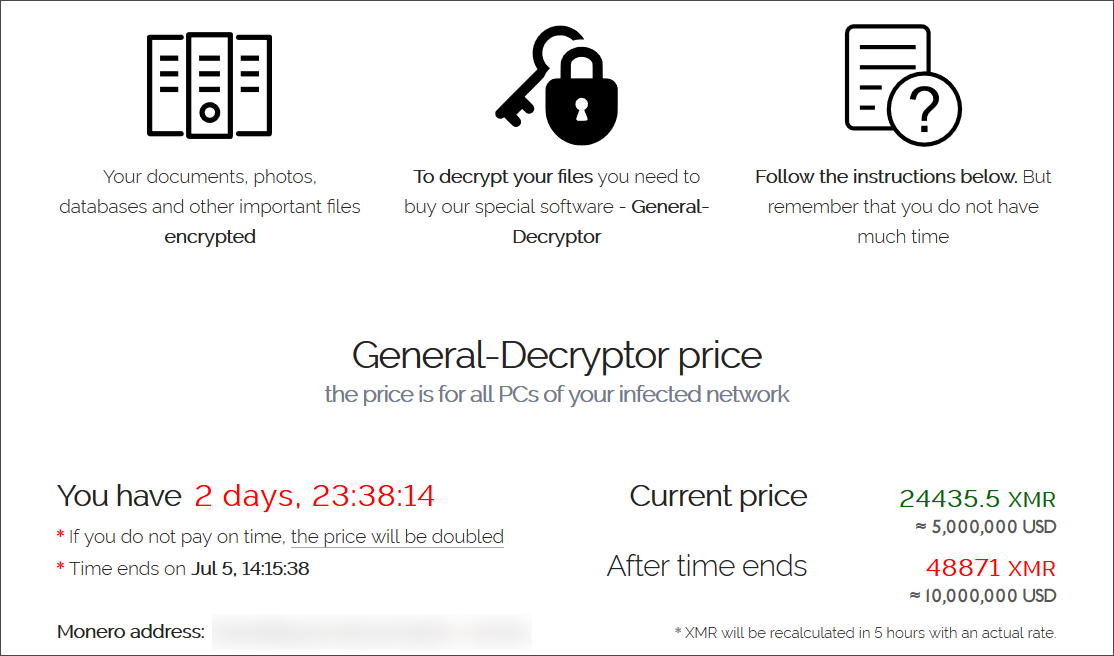
This attack had such wide-ranging consequences worldwide that it brought the full attention of international law enforcement to bear on the group.
Likely feeling pressure and concerns about being apprehended, the REvil gang suddenly shut down on July 13th, 2021, leaving many victims in a lurch with no way of decrypting their files.
The last we had heard of REvil, was that Kaseya received a universal decryptor that victims could use to decrypt files for free. It is unclear how Kaseya received the decryptor but stated it came from a "trusted third party."
REvil returns with new attacks
After their shutdown, researchers and law enforcement believed that REvil would rebrand as a new ransomware operation at some point.
However, much to our surprise, the REvil ransomware gang came back to life this week under the same name.
On September 7th, almost two months after their disappearance, the Tor payment/negotiation and data leak sites suddenly turned back on and became accessible. A day later, it was once again possible to log in to the Tor payment site and negotiate with the ransomware gang.
All prior victims had their timers reset, and it appeared that their ransom demands were left as they were when the ransomware gang shut down in July.
However, there was no proof of new attacks until September 9th, when someone uploaded a new REvil ransomware sample compiled on September 4th to VirusTotal.
Today, we have seen further proof of their renewed attacks as the ransomware gang has published screenshots of stolen data for a new victim on their data leak site.
......................................................................................................................................................................
<<< Please Read between the lines >>>
......................................................................................................................................................................
A chat between what is believed to be a security researcher and REvil, paints a different story, with an REvil operator claiming they simply took a break.
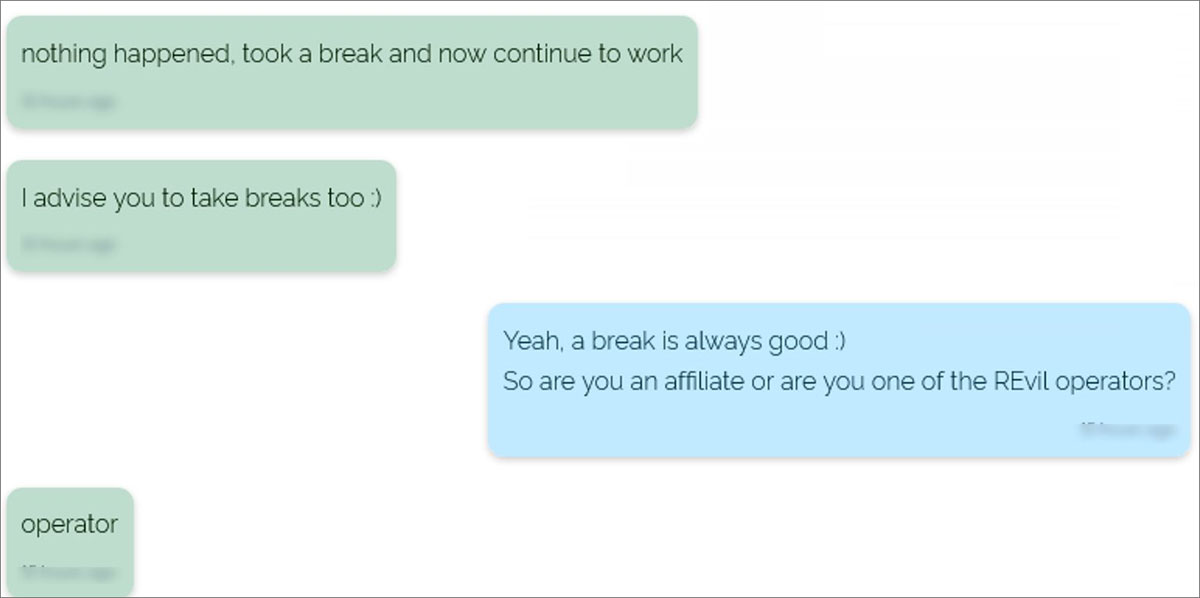
While we may never know the real reason for the disappearance or how Kaseya obtained the decryption key, what is most important is to know that REvil is back to targeting corporations worldwide.
With their skilled affiliates and ability to perform sophisticated attacks, all network admins and security professionals must become familiar with their tactics and techniques."


No comments:
Post a Comment