Securing your digital life, part two: The bigger picture—and special circumstances
We did the basics—now let's look at some more detailed steps to protect yourself.
"In the first half of this guide to personal digital security, I covered the basics of assessing digital risks and protecting what you can control: your devices. But the physical devices you use represent only a fraction of your overall digital exposure.
According to a report by Aite Group, nearly half of US consumers experienced some form of identity theft over the last two years. Losses from these thefts are expected to reach $721.3 billion for 2021—and that’s only counting cases where criminals take over and abuse online accounts. Other valuable parts of your digital life may not carry specific monetary risks to you but could still have a tangible impact on your privacy, safety, and overall financial health.
Case in point: last September, my Twitter account was targeted for takeover by an unidentified attacker. Even though I had taken multiple measures to prevent the theft of my account (including two-factor authentication), the attacker made it impossible for me to log in (though they were locked out of the account as well). It took several weeks and some high-level communication with Twitter to restore my account. As someone whose livelihood is tied to getting the word out about things with a verified Twitter account, this went beyond inconvenience and was really screwing with my job.
The attacker found the email address associated with my Twitter account through a breach at a data aggregator—information probably gleaned from other applications that I had linked to my Twitter account at some point. No financial damage was done, but it made me take a long, hard look at how I protect online accounts.

h hey, it's this guy again. (Maybe this is the guy who tried to get into my Twitter account?)Aitor Diago / Getty Images
Some of the risk tied to your digital life is taken on by service providers who are more directly impacted by fraud than you. Credit card companies, for example, have invested heavily in fraud detection because their business is built on mitigating the risk of financial transactions. But other organizations that handle your personal identifying information—information that proves you are you to the rest of the digitally connected world—are just as big a target for cyber crime but may not be as good at preventing fraud.
Everything counts in multiple accounts
You can do a number of things to reduce the risks posed by data breaches and identity fraud. The first is to avoid accidentally exposing the credentials you use with accounts. A data breach of one service provider is especially dangerous if you haven’t followed best practices in how you set up credentials. These are some best practices to consider:
- Use a password manager that generates strong passwords you don’t have to remember. This can be the manager built into your browser of choice, or it can be a standalone app. Using a password manager ensures that you have a different password for every account, so a breach of one account won’t spill over into others. (Sorry to again call out the person reusing
letmein123!for everything, but it's time to face the music.) - When possible, use two-factor or multi-factor authentication ("2FA" or "MFA"). This combines a password with a second, temporary code or acknowledgment from someplace other than your web browser or app session. Two-factor authentication ensures that someone who steals your password can’t use it to log in. If at all possible, don’t use SMS-based 2FA, because this is more prone to interception (more on this in a minute). Applications like Authy, Duo, Google Authenticator, or Microsoft Authenticator can be paired with a wide variety of services to generate 2FA temporary passwords or to send “push” notifications to your device so that you can approve a login. You can also use a hardware key, such as a Yubico YubiKey, to further segment authentication from your devices.
Special cases
There's one oft-suggested technology that hasn't appeared on this list so far: the VPN or virtual private network. I use VPNs for very specific purposes—namely, to keep the virtual machines I use for malware hunting segmented from the rest of my network or to make them look like they’re in different parts of the world so I can test malware targeting.
Some people use them to evade geographic content licensing restrictions, so they can get their Dr. Who fix or watch The Mandalorian outside of the Disney Co-Prosperity Sphere. I will not comment on those use cases.

When 2FA is not enough
Security measures vary. I discovered after my Twitter experience that setting up 2FA wasn’t enough to protect my account—there’s another setting called “password protection” that prevents password change requests without authentication through email. Sending a request to reset my password and change the email account associated with it disabled my 2FA and reset the password. Fortunately, the account was frozen after multiple reset requests, and the attacker couldn’t gain control.Further Reading
Securing your digital life, part one: The basicsSocial exposure
Social networks, online communities, and apps or services intended to foster social interaction (such as dating) are a major source of information used in targeted attacks. Social media accounts are frequent targets for takeover, and social media users all too often leave essential information about themselves, their family and friends, their activities, and even their finances in the open for others to see and potentially target. If you must use social media, here are some tips to limit your exposure:
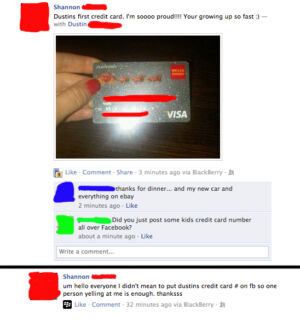
- I shouldn't have to say this, but I'm going to say it anyway: don’t post unredacted pictures of driver's licenses, vaccination cards, credit cards, passports, or other documents with PII on social media. There are no circumstances where this is a good idea. Don't do it, even for a TikTok challenge.
- Lock down access to your social media accounts with 2FA and unique, strong passwords to prevent "brute force" breaches and "password reuse" hacks.
- On Facebook, set the default privacy for posts to “friends only." This will prevent casual leaks of information you don’t want anyone but friends and family to know about.
Do not use “precise location”
 information on posts that can be used to locate you in realtime. If I’m posting a picture of a location, I typically wait until I’ve left the place to post it to social media (especially Twitter or Instagram). If you've got someone stalking you, the last thing you want to do is broadcast your precise location—with pictures, even.
information on posts that can be used to locate you in realtime. If I’m posting a picture of a location, I typically wait until I’ve left the place to post it to social media (especially Twitter or Instagram). If you've got someone stalking you, the last thing you want to do is broadcast your precise location—with pictures, even.- Don’t post pictures with your home address or other identifying information about your residence clearly visible. Your friends and family already know where you live. Nobody else needs to.
- Don’t drop personal email addresses or phone numbers into public online conversations.
- Don’t allow dating apps, ride-sharing apps, or any other apps that use your location data to collect that data while you’re not actively using them. Time and time again, this data has leaked, and it has been used to establish home addresses and patterns of life that can make users vulnerable. I don’t care if Uber has apologized—it will happen again.
- If you are sending your location to someone in one of these apps, make sure it is a public place and that a friend or family member is in sight of that location, or at least knows to check in with you shortly after the appointed meeting time. The Grindr robbery and kidnapping cases in Texas are evidence enough of the importance of this. You don’t need to tell anyone who or why you’re meeting—just ask for a call or text at a certain time.
- Be aware of links sent in Facebook Messenger and of friend requests claiming to be from people you already know—but coming from new accounts. The first is a common account-hacking scheme, and the second is often a sign of someone trying to create a “clone” account to distribute fraudulent messages.
- Don’t download and run anything from Discord without a malware scan. Discord is convenient and handy and widely used, but it is also a veritable hive of scum and villainy.
Never take a conversation in one app over to another—say, from a dating app to WhatsApp—before you’ve met a person in person and feel safe. This app-shifting move is a signature part of romance scams and other fraud cases, intended to get the victim out from under the moderation radar of the dating and social apps and into a more private conversation. There, web links to downloads and other malicious or fraudulent content can be shared.
Or, instead of trying to follow all these suggestions, you could mitigate this entire category of risks by never using social media again.
Some people evaluate the risks involved from a social media presence and do just that. (Though in some countries, Facebook effectively is the Internet, which greatly complicates things.)
You’ll also want Tor or a VPN in situations where you’re on a network that has a TLS proxy that breaks traditional HTTPS encryption by using proxy certificates to decrypt traffic in the middle. At least in those scenarios, the worst that can happen is you can’t get an outbound connection.

READ MORE: ecuring your digital life, part two: The bigger picture—and special circumstances
We did the basics—now let's look at some more detailed steps to protect yourself.


No comments:
Post a Comment