Understandably, many people are overwhelmed by a sentiment that motivates them to act against unprovoked large-scale military invasions, but taking part in cyberattacks is always a bad idea.
Malware disguised as security tool targets Ukraine's IT Army
A new malware campaign is taking advantage of people's willingness to support Ukraine's cyber warfare against Russia to infect them with password-stealing Trojans.
Last month, the Ukrainian government announced a new IT Army composed of volunteers worldwide who conduct cyberattacks and DDoS attacks against Russian entities.
This initiative has led to a outpouring of support by many people worldwide who have been helping target Russian organizations and sites, even if that activity is considered illegal.
Mimicking a real DDoS tool
As is common with malware distributors, threat actors are taking advantage of the IT Army by promoting a fake DDoS tool on Telegram that installs a password and information-stealing trojan.
In a new report by Cisco Talos, researchers warn that threat actors are mimicing a DDoS tool called the “Liberator”, which is a website bomber for use against Russian propaganda outlets.
While the versions downloaded from the real site are “clean”, and likely illegal to use, those circulated in Telegram hide malware payloads, and there’s no way to tell the difference before executing them as neither is digitally signed.
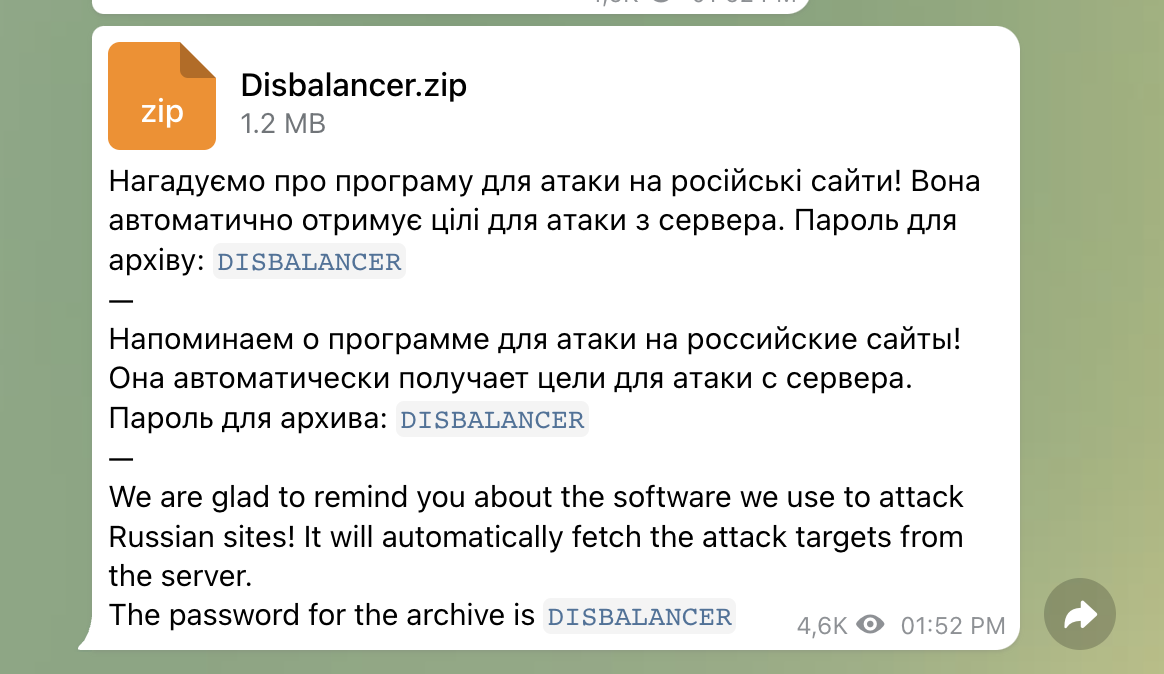
The Telegram posts claim that the tool fetches a list of Russian targets to attack from a server, so the user doesn’t need to do much other than execute it on their machine.
This ease of use is likely to appeal to Ukraine supporters who are not very technical and do not know how to conduct their own attacks to “bomb” Russian sites.
The infostealer
The malware that’s dropped on the victims’ systems performs anti-debug checks before it executes and then follows a process injection step to load the Phoenix information stealer in memory.
Phoenix was first spotted in the summer of 2019, sold in the cybercrime underground as MaaS (malware as a service) for $15/month or $80 for a lifetime subscription.
The particular info-stealer can gather data from web browsers, VPN tools, Discord, filesystem locations, and cryptocurrency wallets, and send them to a remote address, in this case, a Russian IP.
Talos researchers found that this particular IP has been distributing Phoenix since November 2021. Hence, the recent theme change indicates this campaign is just an opportunistic attempt to exploit the war in Ukraine for financial profit.


No comments:
Post a Comment