New phishing attack infects devices with Cobalt Strike
Matanbuchus is a malware-as-a-service (MaaS) project first spotted in February 2021 in advertisements on the dark web promoting it as a $2,500 loader that launches executables directly into system memory.
Palo Alto Networks' Unit 42 analyzed it in June 2021 and mapped extensive parts of its operational infrastructure. The malware's features include launching custom PowerShell commands, leveraging standalone executables to load DLL payloads, and establishing persistence via the addition of task schedules.
Ongoing campaign
Threat analyst Brad Duncan captured a sample of the malware and examined how it works in a lab environment.
The malspam campaign currently underway uses lures that pretend to be replies to previous email conversations, so they feature a 'Re:' in the subject line.
> The emails carry a ZIP attachment that contains an HTML file that generates a new ZIP archive. This ultimately extracts an MSI package digitally signed with a valid certificate issued by DigiCert for "Westeast Tech Consulting, Corp."
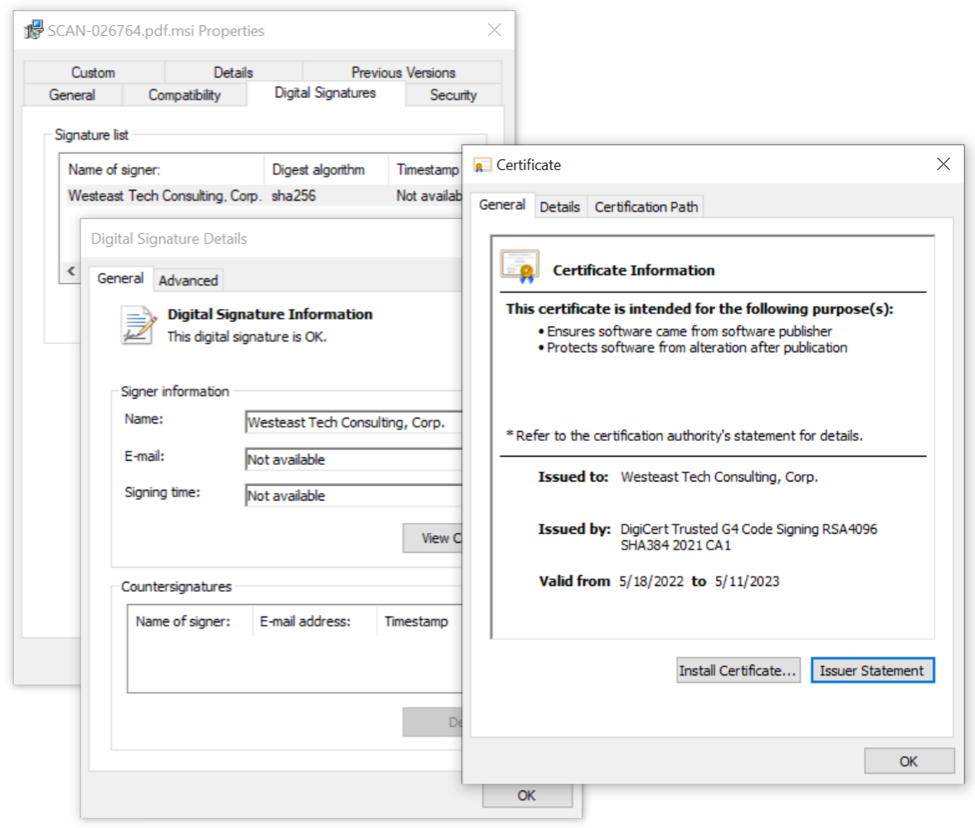
> Running the MSI installer supposedly initiates an Adobe Acrobat font catalog update that ends with an error message, to distract the victim from what happened behind the scenes.
> In the background, two Matanbuchus DLL payloads ("main.dll") are dropped in two different locations, a scheduled task is created to maintain persistence across system reboots, and communication with the command and control (C2) server is established.
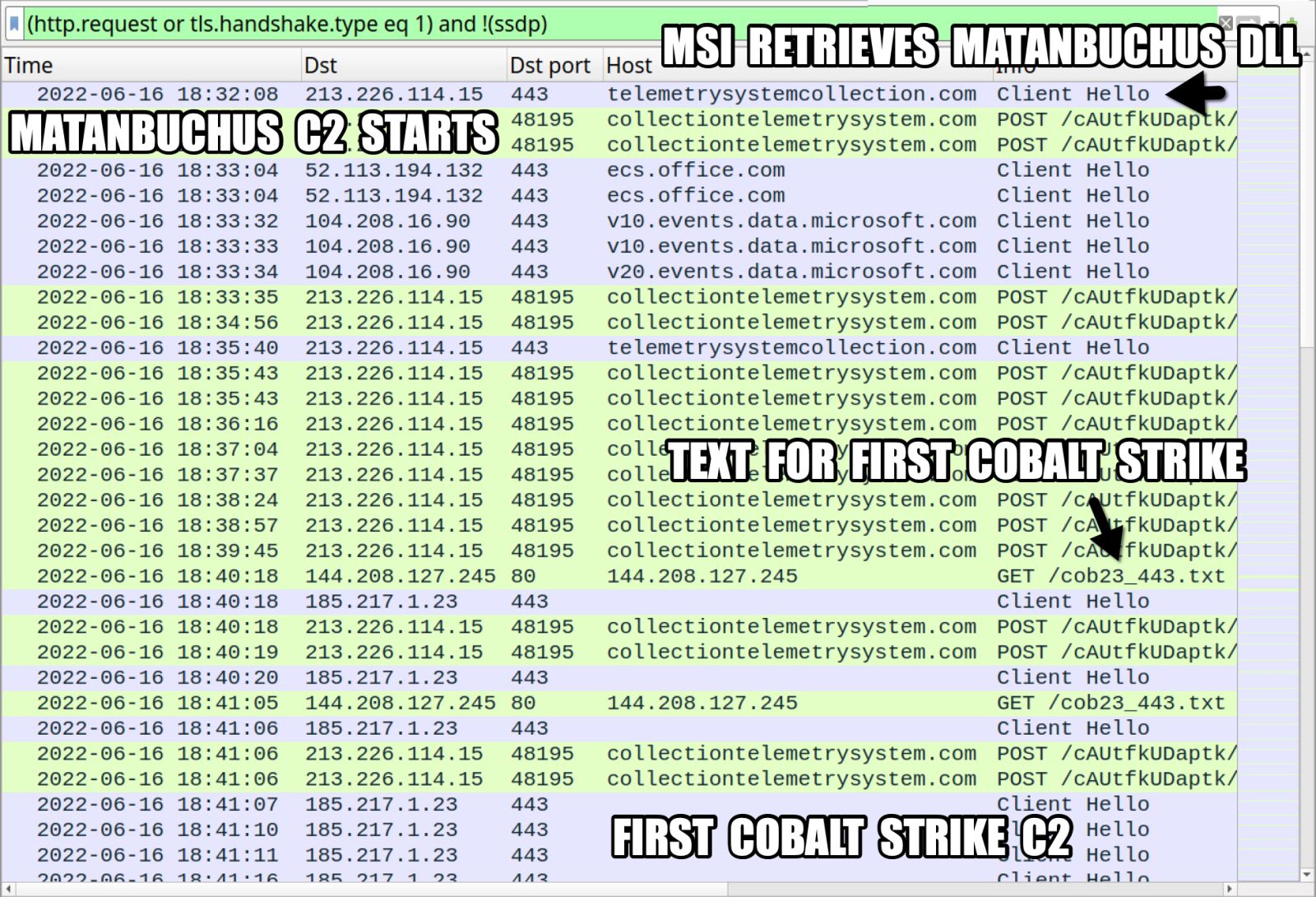
Finally, Matanbuchus loads the Cobalt Strike payload from the C2 server, opening the way to wider exploitation potential.
.jpg)
Related Articles:
Fake antivirus updates used to deploy Cobalt Strike in Ukraine
Android-wiping BRATA malware is evolving into a persistent threat
Hackers exploit three-year-old Telerik flaws to deploy Cobalt Strike
New MaliBot Android banking malware spreads as a crypto miner
Android malware on the Google Play Store gets 2 million downloads



No comments:
Post a Comment