Credentials for thousands of open source projects free for the taking—again!
Leak of credentials can be used in massive supply-chain attacks.

"A service that helps open source developers write and test software is leaking thousands of authentication tokens and other security-sensitive secrets. Many of these leaks allow hackers to access the private accounts of developers on Github, Docker, AWS, and other code repositories, security experts said in a new report.
The availability of the third-party developer credentials from Travis CI has been an ongoing problem since at least 2015. At that time, security vulnerability service HackerOne reported that a Github account it used had been compromised when the service exposed an access token for one of the HackerOne developers. A similar leak presented itself again in 2019 and again last year.The tokens give anyone with access to them the ability to read or modify the code stored in repositories that distribute an untold number of ongoing software applications and code libraries. The ability to gain unauthorized access to such projects opens the possibility of supply chain attacks, in which threat actors tamper with malware before it's distributed to users. The attackers can leverage their ability to tamper with the app to target huge numbers of projects that rely on the app in production servers. . . .
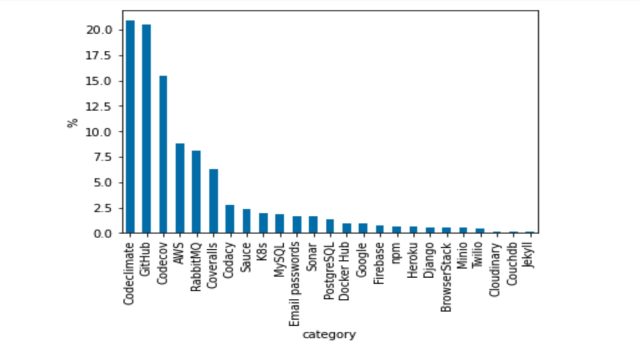
Examples of access tokens that were exposed include:
- Access tokens to GitHub that may allow privileged access to code repositories
- AWS access keys
- Sets of credentials, typically an email or username and password, which allow access to databases such as MySQL and PostgreSQL
- Docker Hub passwords, which may lead to account takeover if MFA (multi-factor authentication) is not activated
The following graph shows the breakdown:
Aqua Security researchers added:
We found thousands of GitHub OAuth tokens. It’s safe to assume that at least 10-20% of them are live. Especially those that were found in recent logs. . ."
Please continue reading >> https://arstechnica.com/information-technology/2022/06/credentials-for-thousands-of-open-source-projects-free-for-the-taking-again/


No comments:
Post a Comment