That's only one report yesterday
Whoosh confirms data breach after hackers sell 7.2M user records

"The Russian scooter-sharing service Whoosh has confirmed a data breach after hackers started to sell a database containing the details of 7.2 million customers on a hacking forum.
Whoosh is Russia's leading urban mobility service platform, operating in 40 cities with over 75,000 scooters.
On Friday, a threat actor began selling the stolen data on a hacking
forum, which allegedly contains promotion codes that can be used to
access the service for free, as well as partial user identification and
payment card data. . .
In a new statement shared with RIA Novosti today, Whoosh admits that there is a data leak and informs its user base they are working with law enforcement authorities to take all mea insures to stop the distribution of the data.
"The leak did not affect sensitive user data, such as account access, transaction information, or travel details," stated a Whoosh spokesperson.
"Our security procedures also exclude the possibility of third parties gaining access to full payment data of users' bank cards."
What's for sale
On Friday, a user on the 'Breached' hacking forums posted a database containing details about 7.2 millionWhoosh customers, including email addresses, phone numbers, and first names.
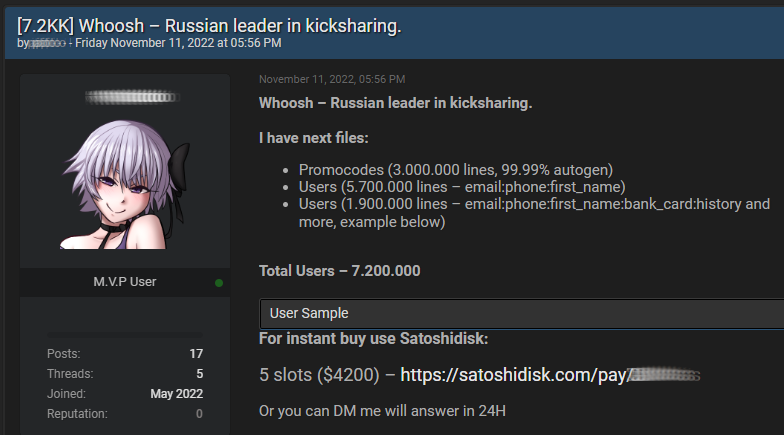
The database also contained partial payment card details for a subset of 1,900,000 users.
The seller also claimed that the stolen data included 3,000,000 promo codes, which people can use to rent Whoosh scooters without paying.
The seller says they are selling the data to only five buyers for $4,200 each, or .21490980 bitcoins, and according to the SatoshiDisk platform used for the transaction, no one has yet to purchase the database.
In a separate sale of the data on Telegram, the threat actor claims it was stolen during a November 2022 attack on Whoosh.
Russian database leaks
According to an August 2022 report from Roskomnadzor, Russia's internet watchdog, there were 40 confirmed Russian company data breaches since the beginning of the year.
In September 2022, Group-IB published a report claiming to have observed 140 database sales stolen from Russian companies this summer alone, with the total number of exposed records reaching 304 million.
The most notable leak, in terms of its impact this year, was that of the food delivery app Yandex Food, which led to multiple collateral data exposures."
LATEST ARTICLES
North Korean hackers target European orgs with updated malware
North Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and Latin America.
- November 15, 2022
- 05:24 PM
 0
0
Upgrade your Mac with this premium limited edition bundle
Whether it's your backup or your primary machine, this limited edition Mac bundle includes Microsoft Office and 6 other programs for $59.99, 96% off the $1,516 MSRP.
- November 15, 2022
- 02:08 PM
 0
0
Windows 10 KB5020030 preview update released with ten improvements
Microsoft has released this month's optional KB5020030 Preview cumulative update for all editions of Windows 10 20H2, 21H1, 21H2, and 22H2.
- November 15, 2022
- 02:04 PM
 1
1
Google to roll out Privacy Sandbox on Android 13 starting early 2023
Google announced today that they will begin rolling out the Privacy Sandbox system on a limited number of Android 13 devices starting in early 2023.
- November 15, 2022
- 01:00 PM
 0
0
Researchers release exploit details for Backstage pre-auth RCE bug
Older versions of the Spotify Backstage development portal builder are vulnerable to a critical (CVSS score: 9.8) unauthenticated remote code execution flaw allowing attackers to run commands on publicly exposed systems.
- November 15, 2022
- 11:29 AM
 0
0
MFA Fatigue attacks are putting your organization at risk
A common threat targeting businesses is MFA fatigue attacks—a technique where a cybercriminal attempts to gain access to a corporate network by bombarding a user with MFA prompts. This article includes some measures you can implement to prevent these types of attacks.
- November 15, 2022
- 10:07 AM
 1
1
Save on time and everyday items with a Costco membership deal
To help you free up more time in the day and ways to maximize our budget, this Costco Gold Star Membership helps you manage those changes and cut down on errands for $60.
- November 15, 2022
- 07:17 AM
 0
0
Chinese hackers target government agencies and defense orgs
The Chinese espionage APT (advanced persistent threat), tracked as 'Billbug' (aka Thrip, or Lotus Blossom), is currently running a 2022 campaign targeting government agencies and defense organizations in multiple Asian countries.
- November 15, 2022
- 06:00 AM
 0
0










No comments:
Post a Comment