FBI investigates data breach impacting U.S. House members and staff

"The FBI is investigating a data breach affecting U.S. House of Representatives members and staff after their account and sensitive personal information was stolen from DC Health Link's servers.
DC Health Link is the organization that administers the health care plans of U.S. House members, their staff, and their families.
Impacted individuals were notified today of the breach in an email from Catherine L. Szpindor, the U.S. House Chief Administrative Officer, as first reported by DailyCaller.
Update March 08, 18:24 ET: In a statement to BleepingComputer, Adam Hudson, the Public Information Officer for Health Benefit Exchange Authority, confirmed that some of the stolen DC Health Link data was exposed online and that notifications will be sent to those affected.
"We can confirm reports that data for some DC Health Link customers has been exposed on a public forum. We have initiated a comprehensive investigation and are working with forensic investigators and law enforcement. Concurrently, we are taking action to ensure the security and privacy of our users’ personal information. We are in the process of notifying impacted customers and will provide identity and credit monitoring services. In addition, and out of an abundance of caution, we will also provide credit monitoring services for all of our customers. The investigation is still ongoing and we will provide more information as we have more to share."
Update March 09, 10:15 EST: NBC News reports that House Speaker Kevin McCarthy and House Minority Leader Hakeem Jeffries said in a letter to the head of the DC Health Benefit Exchange Authority that the FBI had purchased some of the stolen information put up for sale online.
Stolen data already up for sale online
While the email sent by House CAO Szpindor doesn't have any details regarding the stolen data, BleepingComputer discovered that at least one threat actor (known as IntelBroker) is selling the U.S. House members' information stolen from DC Health Link's servers on a hacking forum.
A sample of stolen data with the database header shows it contains the information of roughly 170,000 affected individuals, including their names, dates of birth, addresses, email addresses, phone numbers, Social Security Numbers, and much more (the entire list is available below).
Subscriber ID,Member ID,Policy ID,Status,First Name,Last Name,SSN,DOB,Gender,Relationship,Benefit Type,Plan Name,HIOS ID,Plan Metal Level,Carrier Name,Premium Amount,Premium Total,Policy APTC,Policy Employer Contribution,Coverage Start,Coverage End,Employer Name,Employer DBA,Employer FEIN,Employer HBX ID,Home Address,Mailing Address,Work Email,Home Email,Phone Number,Broker,Race,Ethnicity,Citizen Status,Plan Year Start,Plan Year End,Plan Year StatusThe data was posted for sale on Monday, March 6, and IntelBroker claims it was stolen after breaching the DC.gov Health Benefit Exchange Authority.
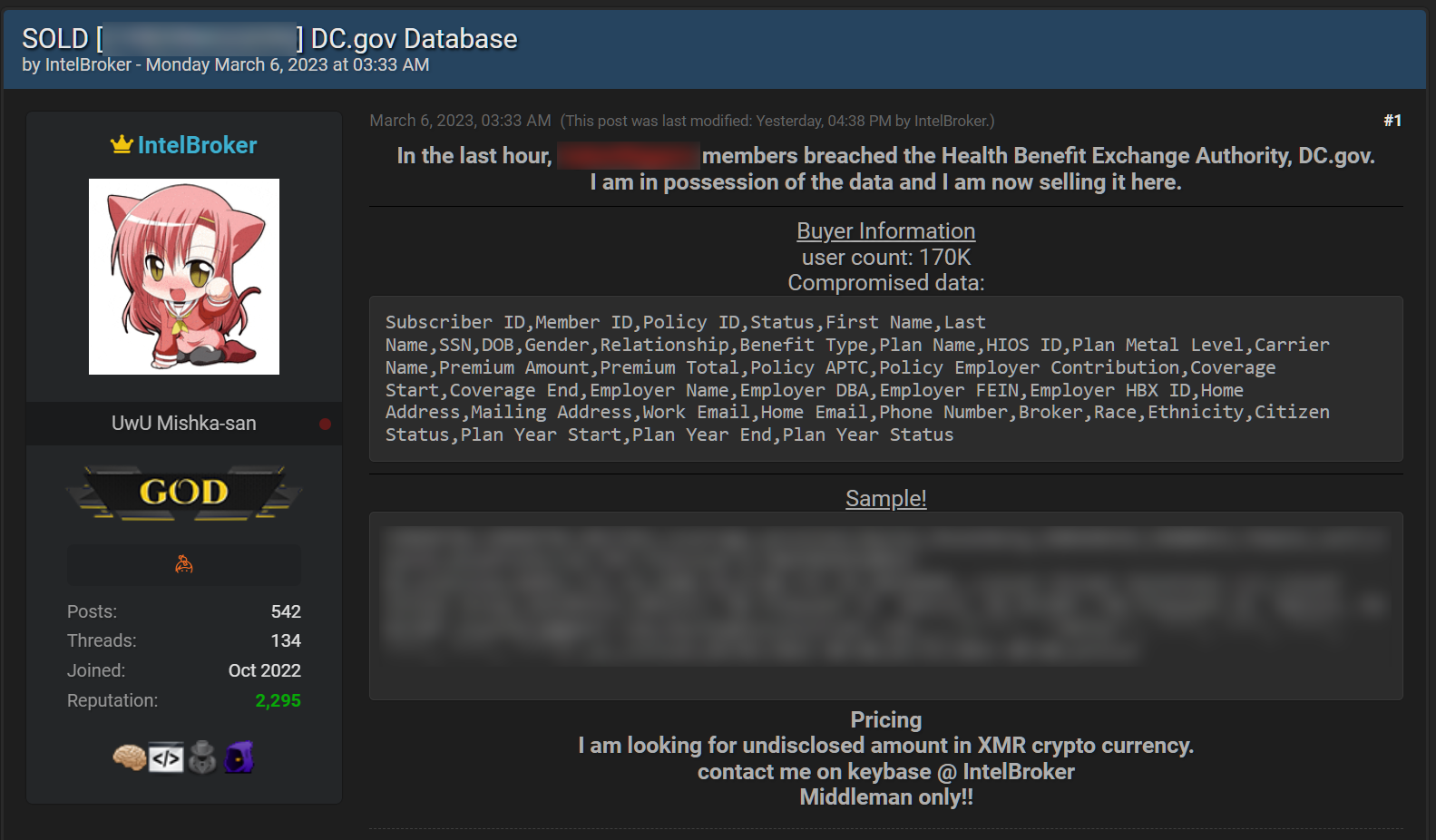
"I am looking for undisclosed amount in XMR crypto currency. Contact me on keybase @ IntelBroker. Middleman only," the threat actor says.
✓ The threat actor also claims that the stolen information has already been sold to at least one buyer." READ MORE
LATEST ARTICLES
GitHub makes 2FA mandatory next week for active developers
GitHub will start requiring active developers to enable two-factor authentication (2FA) on their accounts beginning next week, on March 13.
- March 09, 2023
- 12:00 PM
 0
0
Protecting collocated servers from DDoS attacks using GRE tunnels
You can get DDoS protection remotely for your collocated server using a generic routing encapsulation (GRE) tunnel. We will explain how GRE tunnels combined with Gcore scrubbing centers can help keep your data safe.
- March 09, 2023
- 10:10 AM
 0
0
IceFire ransomware now encrypts both Linux and Windows systems
Threat actors linked to the IceFire ransomware operation are now actively targeting Linux systems worldwide with a new dedicated encryptor.
- March 09, 2023
- 09:00 AM
 0
0
Turn any website into an app with this AppMySite deal
Don't miss your chance to get five years' worth of access to the AppMySite tool at a rate far below its MSRP. Get the AppMySite Mobile App Builder's Pro Plan for just $49.99 for a limited time.
- March 09, 2023
- 07:17 AM
 0
0
FBI investigates data breach impacting U.S. House members and staff
The FBI is investigating a data breach affecting U.S. House of Representatives members and staff after their account and personal information was stolen from DC Health Link's servers.
- March 08, 2023
- 05:48 PM
 0
0
Bitwarden flaw can let hackers steal passwords using iframes
Bitwarden's credentials autofill feature contains a risky behavior that could allow malicious iframes embedded in trusted websites to steal people's credentials and send them to an attacker.
- March 08, 2023
- 05:08 PM
 2
2
Microsoft enables LSA protection by default in Windows Canary build
Microsoft says the latest Windows 11 build that is rolling out to Insiders in the Canary channel will try to enable Local Security Authority (LSA) protection by default.
- March 08, 2023
- 03:38 PM
 0
0
Fortinet warns of new critical unauthenticated RCE vulnerability
Fortinet has disclosed a "Critical" vulnerability impacting FortiOS and FortiProxy, which allows an unauthenticated attacker to execute arbitrary code or perform denial of service (DoS) on the GUI of vulnerable devices using specially crafted requests.
- March 08, 2023
- 02:25 PM
 0
0
Microsoft testing File Explorer access keys, new VPN status icon
Microsoft has released a new Windows 11 preview build with new features such as File Explorer access keys, a new VPN status indicator, and a new way to copy two-factor authentication (2FA) codes from text messages.
- March 08, 2023
- 02:17 PM
 1
1
Prep for IT certifications with this this CompTIA course bundle deal
Don't miss your chance to get best-of-web pricing for The Complete 2023 CompTIA Certification Courses Super Bundle while it's on sale for just $89.99.
- March 08, 2023
- 02:11 PM
 0
0
Veeam fixes bug that lets hackers breach backup infrastructure
Veeam urged customers to patch a high-severity Backup Service security vulnerability impacting its Backup & Replication software.
- March 08, 2023
- 01:13 PM
 0
0
Ransomware gang posts video of data stolen from Minneapolis schools
The Medusa ransomware gang is demanding a $1,000,000 ransom from the Minneapolis Public Schools (MPS) district to delete data allegedly stolen in a ransomware attack.
- March 08, 2023
- 12:37 PM
 0
0
DuckDuckGo launches AI-powered search query answering tool
Privacy-focused search engine DuckDuckGo has launched the first beta version of DuckAssist, an AI-assisted feature that writes accurate summaries to answer users' search queries.
- March 08, 2023
- 10:22 AM
 5
5
Pen Testers using Vulnerability Scanners – Closing the Gap
Both penetration testing and vulnerability scanning are essential to upholding and maintaining a strong security posture. Here are the benefits of combining both to maximize coverage and your web application security.
- March 08, 2023
- 10:07 AM
 0
0















No comments:
Post a Comment