An initial assessment from The Shadowserver Foundation, a non-profit organization for making the internet more secure, saw that CVE-2023-3519 was likely affecting more than 11,000 NetScaler ADC and Gateway servers exposed online.
Netscaler ADC bug exploited to breach US critical infrastructure org
Ionut Ilascu
- July 21, 2023
- 08:51 AM
- 0

The Cybersecurity and Infrastructure Security Agency (CISA) says that the attack occurred in June and hackers used their access to steal Active Directory data.
Hackers exfiltrated AD data
- The backdoor enabled the attacker to enumerate active directory (AD) objects, which include users, groups, applications, and devices on the network, as well as steal AD data.
- CISA has released an advisory with tactics, techniques, and procedures (TTPs) along with detection methods to help organizations, particularly those in the critical infrastructure segment, determine if their systems were compromised.
They did SMB scanning on the subnet and used the webshell to check and exfiltrate Active Directory inventory, with a particular interest in:
- NetScaler configuration files that contain an encrypted password whose key is on the ADC appliance
- NetScaler decryption keys, which can unlock the AD password in the configuration file
- The list of users, systems, groups, subnets, organizational units, contacts, partitions, and trusts in the Active Directory
It appears that the hackers tried to cover their tracks by deleting the authorization file, which would prevent admins from logging in remotely. To regain access, a reboot into single-user mode is necessary, which may have deleted artifacts.
With threat actors exploiting the vulnerability since it was a zero-day, NetScaler admins should install without delay the latest updates Citrix released to address the issue.
Thousands of vulnerable servers exposed
An initial assessment from The Shadowserver Foundation, a non-profit organization for making the internet more secure, saw that CVE-2023-3519 was likely affecting more than 11,000 NetScaler ADC and Gateway servers exposed online.
That number increased to 15,000, the organization told BleepingComputer today, after refining their query to tag as vulnerable all NetScaler appliances that returned a "last modified" header with a date before July 1st.
The new count is also due to improving the detection coverage for NetScaler AAA (authentication virtual server) machines. Although increased, the number likely represents a conservative estimate, the organization says.
CISA has also released a set of commands that organizations can use to check for signs of compromise by exploiting CVE-2023-3519.
Command stacking leading to root
Citrix patched CVE-2023-3519 on July 18 along with two less severe vulnerabilities. One is a reflected cross-site scripting (XSS) bug with an 8.3 severity score and tracked as CVE-2023-3466.
Exploiting this flaw is possible if the victim on the same network as the vulnerable appliance loads in the browser a malicious link from an attacker.
The other is a privilege escalation to root identified as CVE-2023-3467. It received an 8.0 severity score and it can be leveraged by an attacker with the least privileged role to the NetScaler command-line interface (CLI).
Jorren Geurts and Wouter Rijkborst, researchers at cybersecurity company Resillion, published a detailed technical analysis of the vulnerability, explaining how stacking specific commands in the NetScaler CLI allows any user with read-only permissions to obtain root privileges on the system.
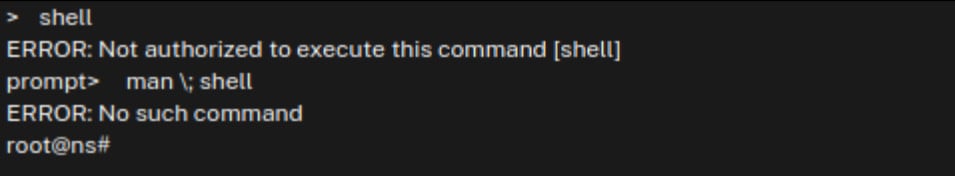
source: Resillion
The researchers told BleepingComputer that low-privileged user could also get root permission on the appliance using the same commands in the web management interface. However, Rijkborst said that this method is less stable.
There is currently no information about these less severe vulnerabilities being exploited in the wild but threat actors that already have access to the network could leverage them to increase their access on the network.
Recently, The Estée Lauder Companies got breached twice in separate attacks from Clop, through the MOVEit zero-day vulnerability, and ALPHV/BlackCat ransomware gangs.
It remains unclear how ALPH/BlackCat obtained initial access but the gang bragged that two weeks after the company engaged Microsoft DART and Mandiant services to deal with the first incident, they were still on the network.
Threat actors, especially advanced groups, don’t always rush to move laterally on the victim network and sometimes they wait silently to find a method that is less noisy and increases the success of the attack.




No comments:
Post a Comment