The UDP-based attack occurred last year on October 29 and targeted an internet service provider (ISP) in Eastern Asia in an attempt to bring its services offline.
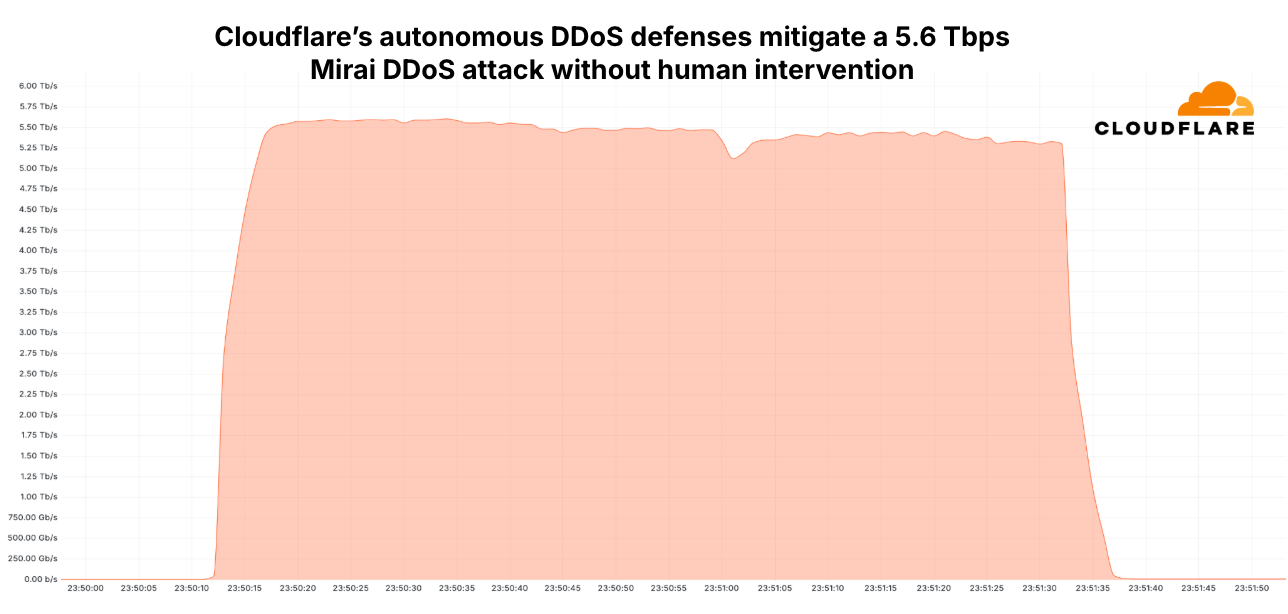
Cloudflare mitigated a record-breaking 5.6 Tbps DDoS attack
Bill Toulas
- January 21, 2025
- 04:04 PM
- 2

The largest distributed denial-of-service (DDoS) attack to date peaked at 5.6 terabits per second and came from a Mirai-based botnet with 13,000 compromised devices.
Security and connectivity services provider Cloudflare says that the assault lasted 80 seconds but had no impact on the target and generated no alerts because its detection and mitigation was completely autonomous.
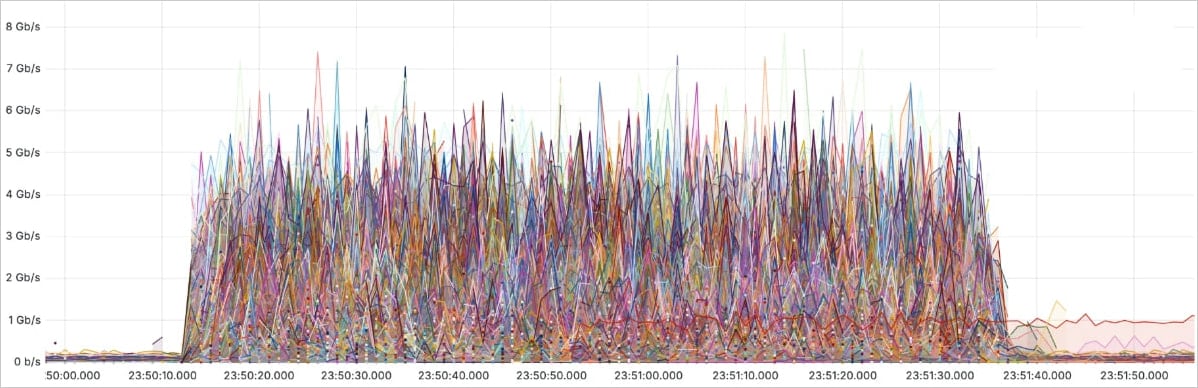
Source: Cloudflare
An earlier DDoS attack that Cloudflare reported in early October 2024 peaked at 3.8 Tbps, lasted for 65 seconds, and held the record for the largest volumetric assault.
Hyper volumetric DDoS attacks have started to become more frequent, a trend that became noticeable in the third quarter of 2024, according to Cloudflare. In the fourth quarter of the year attacks started to exceed 1Tbps, with a quarter-over-quarter growth of 1,885%.
Attacks that exceeded 100 million packets per second (pps) also increased by 175%, with a notable 16% of them also going over 1 billion pps.
.jpg)
Source: Cloudflare
Hyper-volumetric HTTP DDoS attacks only accounted for 3% of the total recorded, with 63% of the remaining being small attacks that did not exceed 50,000 requests per second (rps).
The stats are similar for network layer (Layer 3/Layer 4) DDoS attacks, where 93% did not go beyond 500 Mbps, and 87% were limited to numbers below 50,000 pps.
Cloudflare warns that DDoS attacks are becoming increasingly short-lived, to a point that it is impractical for a human to respond, analyze the traffic, and apply mitigations.
Roughly 72% of HTTP and 91% of network layer DDoS attacks ended in less than10 minutes. On the other side of the spectrum, only 22% of HTTP and 2% of network layer DDoS attacks lasted for more than an hour.
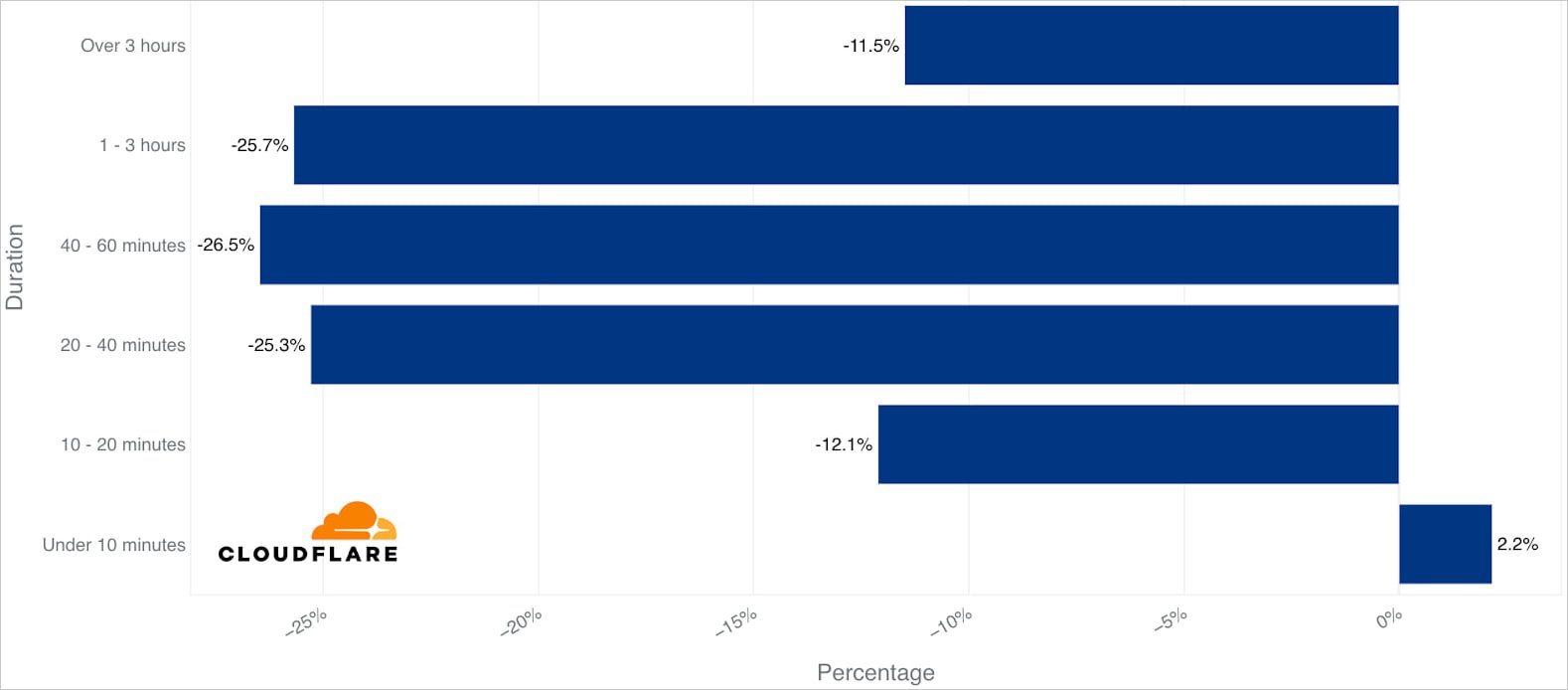
Source: Cloudflare
The internet security firm says these short bursts of overwhelming traffic usually occur during peak usage periods, like during holidays and sales events for a maximum impact.
This lays the ground for ransom DDoS attacks, which also had a notable 78% increase QoQ and 25% growth YoY, peaking during Q4 and the Christmas holiday season.
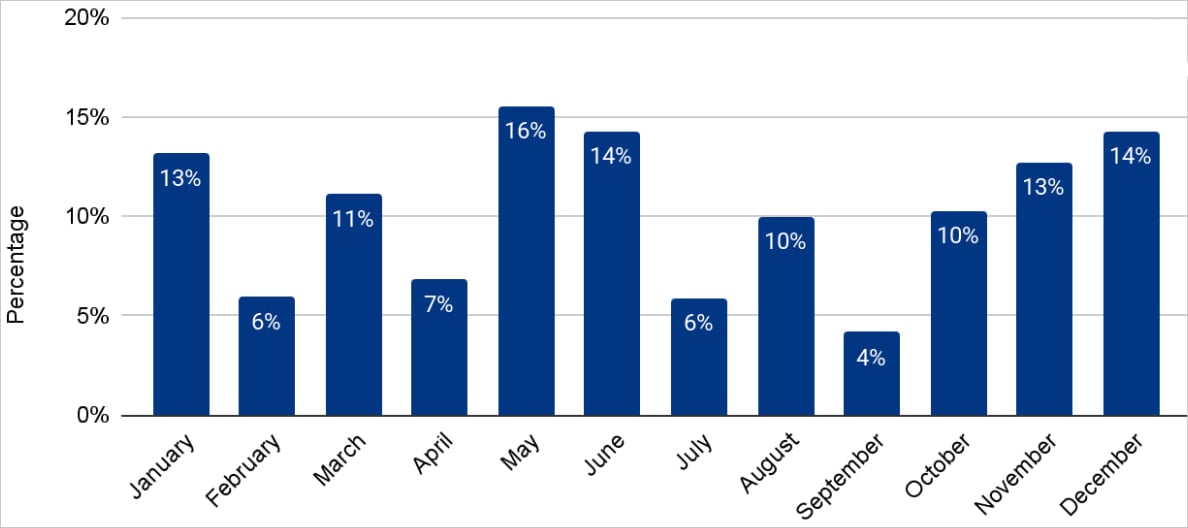
Source: Cloudflare
- The company says that the most attacked targets in the last quarter of 2024 were in China, Philippines, and Taiwan, followed by Hong Kong and Germany.
-
Bitbucket services “hard down” due to major worldwide outage
Bitbucket is investigating a massive outage affecting Atlassian Bitbucket Cloud customers worldwide, with the company saying its cloud services are "hard down."
- January 21, 2025
- 12:23 PM
 0
0
-
7-Zip fixes bug that bypasses Windows MoTW security warnings, patch now
A high-severity vulnerability in the 7-Zip file archiver allows attackers to bypass the Mark of the Web (MotW) Windows security feature and execute code on users' computers when extracting malicious files from nested archives.
- January 21, 2025
- 11:05 AM
 2
2
-
Ransomware gangs pose as IT support in Microsoft Teams phishing attacks
Ransomware gangs are increasingly adopting email bombing followed by posing as tech support in Microsoft Teams calls to trick employees into allowing remote control and install malware that provides access to the company network.
- January 21, 2025
- 10:59 AM
 0
0
- Security· Sponsored Content
Criminal IP Teams Up with OnTheHub for Digital Education Cybersecurity
AI SPERA announced today that it has partnered with education platform OnTheHub to provide its integrated cybersecurity solution, Criminal IP, to students and educational institutions.
- January 21, 2025
- 10:02 AM
 0
0








No comments:
Post a Comment