- The exposure of user prompts is a privacy breach that should be very concerning for organizations using the AI model for sensitive business operations.
- Additionally, the exposure of backend details and API keys could give attackers a way into DeepSeek's internal networks, privilege escalation, and potentially larger-scale breaches.
DeepSeek exposes database with over 1 million chat records

DeepSeek, the Chinese AI startup known for its DeepSeek-R1 LLM model, has publicly exposed two databases containing sensitive user and operational information.
- The unsecured ClickHouse instances reportedly held over a million log entries containing user chat history in plaintext form, API keys, backend details, and operational metadata.
Wiz Research discovered this exposure during a security assessment of DeepSeek's external infrastructure.
The security firm found two publicly accessible database instances at oauth2callback.deepseek.com:9000 and dev.deepseek.com:9000 that allowed arbitrary SQL queries via a web interface without requiring authentication.
The databases contained a 'log_stream' table that stored sensitive internal logs dating from January 6, 2025, containing:
- user queries to DeepSeek's chatbot,
- keys used by backend systems to authenticate API calls,
- internal infrastructure and services information,
- and various operational metadata.
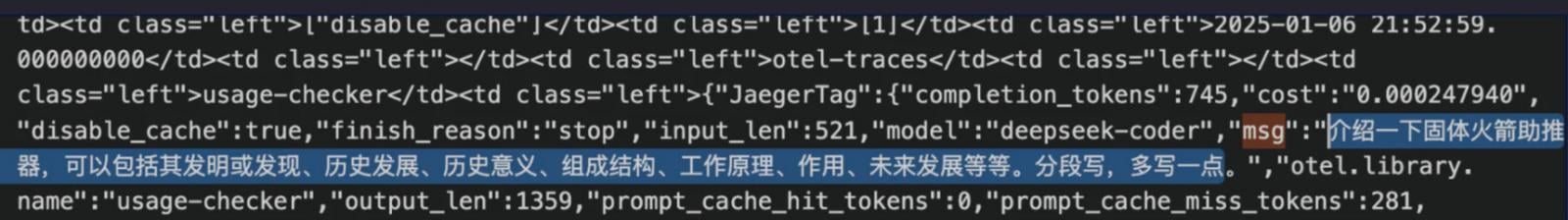
Source: Wiz
"This level of access posed a critical risk to DeepSeek's own security and for its end-users," comments Wiz.
- "Not only an attacker could retrieve sensitive logs and actual plaintext chat messages, but they could also potentially exfiltrate plaintext passwords and local files along propriety information directly from the server using queries like: SELECT * FROM file('filename') depending on their ClickHouse configuration."
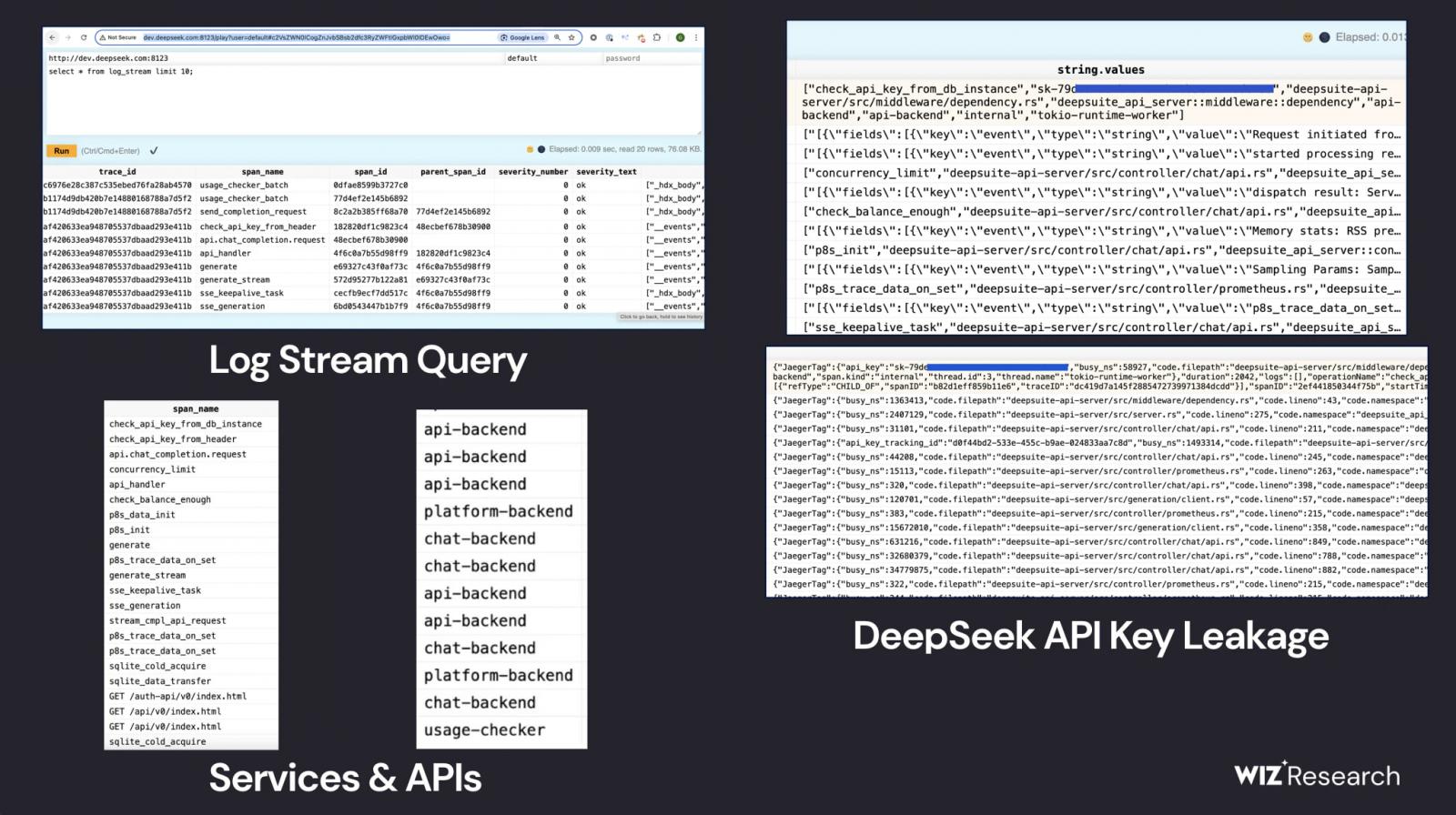
Wiz says it could execute more intrusive queries but limited its exploration to enumeration to keep its research within certain ethical constraints.
- It is unknown if Wiz's researchers were the first to discover this exposure or if malicious actors have already taken advantage of the misconfiguration.
In any case, Wiz informed DeepSeek of the matter, and the company promptly addressed the exposure, so the databases are no longer public.
=====
-
KuCoin to pay nearly $300 million in penalties after guilty plea
KuCoin's operator, PEKEN Global Limited, pleaded guilty to operating an unlicensed money-transmitting business and agreed to pay $297 million in penalties to settle charges in the U.S.
- January 30, 2025
- 07:18 PM
 0
0
-
Backdoor found in two healthcare patient monitors, linked to IP in China
The US Cybersecurity and Infrastructure Security Agency (CISA) is warning that Contec CMS8000 devices, a widely used healthcare patient monitoring device, include a backdoor that quietly sends patient data to a remote IP address and downloads and executes files on the device.
- January 30, 2025
- 06:31 PM
 0
0
-
Google blocked 2.36 million risky Android apps from Play Store in 2024
Google blocked 2.3 million Android app submissions to the Play Store in 2024 due to violations of its policies that made them potentially risky for users.
- January 30, 2025
- 03:57 PM
 0
0
-
StackSocial just dropped the price of a Babbel lifetime subscription
Babbel was developed by a team of over 100 expert linguists to help you quickly learn to speak a new language. The app has lessons for 14 different languages, and you'll have time to study as much as you want with a lifetime subscription. It's only $129.99 (reg. $599) to get Babbel for life, but that won't last long.
- January 30, 2025
- 02:04 PM
 0
0
-
Ransomware attack disrupts New York blood donation giant
The New York Blood Center (NYBC), one of the world's largest independent blood collection and distribution organizations, says a Sunday ransomware attack forced it to reschedule some appointments.
- January 30, 2025
- 12:53 PM
 0
0
-
Security· Sponsored Content
The Advantages of Cloud-Based Remote Desktop versus RDP over VPN
Remote work is now an essential part of many businesses, requiring organizations to rethink how they provide secure and efficient access to corporate resources. Learn from TruGrid about the advantages of cloud-based RDP versus RDP over VPN, especially in the context of security, performance, and cost-effectiveness.
- January 30, 2025
- 10:11 AM
 0
0
-
Major GitHub outage affects pull requests and other services
GitHub is mitigating an ongoing incident causing problems with multiple services, including performing pull requests, creating or viewing issues, and even viewing repositories and commits.
- January 30, 2025
- 10:06 AM
 0
0
-
New Syncjacking attack hijacks devices using Chrome extensions
A new attack called 'Browser Syncjacking' demonstrates the possibility of using a seemingly benign Chrome extension to take over a victim's device through the browser.
- January 30, 2025
- 09:33 AM
 3
3
-
Microsoft lifts Windows 11 update block for PCs with gaming issues
Microsoft has removed a safeguard hold that prevented devices with Auto HDR enabled from installing the Windows 11 2024 Update due to gaming issues.
- January 30, 2025
- 08:53 AM
 0
0
-
Police seizes Cracked and Nulled hacking forum servers, arrests suspects
Europol and German law enforcement confirmed the arrest of two suspects and the seizure of 17 servers in Operation Talent, which took down Cracked and Nulled, two of the largest hacking forums with over 10 million users.
- January 30, 2025
- 08:47 AM
 0
0
-
Why use 10 AI apps when this AI Magicx deal does it all (for less).
Whether you're a solo entrepreneur, small business owner, or content creator, the AI Magicx platform helps streamline tasks that used to take hours. And with the Rune Plan Lifetime Subscription now available for just $69.99 (reg. $99.99) using the code TAKE30 at checkout, there's no better time to get started.
- January 30, 2025
- 07:10 AM
 0
0
-
Time Bandit ChatGPT jailbreak bypasses safeguards on sensitive topics
A ChatGPT jailbreak flaw, dubbed "Time Bandit," allows you to bypass OpenAI's safety guidelines when asking for detailed instructions on sensitive topics, including the creation of weapons, information on nuclear topics, and malware creation.
- January 30, 2025
- 07:00 AM
 4
4
-
New Aquabotv3 botnet malware targets Mitel command injection flaw
A new variant of the Mirai-based botnet malware Aquabot has been observed actively exploiting CVE-2024-41710, a command injection vulnerability in Mitel SIP phones.
- January 29, 2025
- 07:55 PM
 0
0
-
Solana Pump.fun tool DogWifTool compromised to drain wallets
DogWifTools has disclosed on its official Discord channel that its software has been compromised by a supply chain attack that impacted its Windows client, infecting users with malware.
- January 29, 2025
- 07:33 PM
 0
0
-
Laravel admin package Voyager vulnerable to one-click RCE flaw
Three vulnerabilities discovered in the open-source PHP package Voyager for managing Laravel applications could be used for remote code execution attacks.
- January 29, 2025
- 02:27 PM
 0
0
















No comments:
Post a Comment