Russian hackers attack Western military mission using malicious drive

The Russian state-backed hacking group Gamaredon (aka “Shuckworm”) has been targeting a military mission of a Western country in Ukraine in attacks likely deployed from removable drives.
Symantec threat researchers say the campaign started in February 2025 and continued until March, with hackers deploying an updated version of the GammaSteel info-stealing malware to exfiltrate data.
According to the report, initial access to the infected systems was probably achieved via removable drives containing malicious .LNK files, a vector that Gamaredon has used in the past.
Latest Gamaredon attacks in Ukraine
During the investigation, the researchers noticed in the Windows Registry of the compromised system a new value under the UserAssist key, indicating that the infection started from an external drive from a shortcut file named files.lnk.
Next, a heavily obfuscated script creates and runs two files. The first handles command and control (C2) communications, resolving the server address using legitimate services, and connecting to Cloudflare-protected URLs.
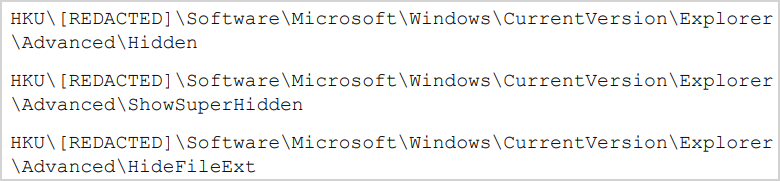
The second file handles the spreading mechanism to infect other removable and network drives using LNK files, while also hiding certain folders and system files to hide the compromise.
Source: Symantec
Next, Gamaredon used a reconnaissance PowerShell script that can capture and exfiltrate screenshots of the infected device and gather information about installed antivirus tools, files, and running processes.
The final payload used in the observed attacks is a PowerShell-based version of GammaSteel that is stored in Windows Registry.
Source: Symantec
The malware can steal documents (.DOC, .PDF, .XLS, .TXT) from various locations like Desktop, Documents, and Downloads, confirming Gamaredon’s continuing interest in espionage.
Ultimately, the malware uses ‘certutil.exe’ to hash the files and exfiltrates them using PowerShell web requests. If the exfiltration fails, Gamaredon uses cURL over Tor to transfer the stolen data.
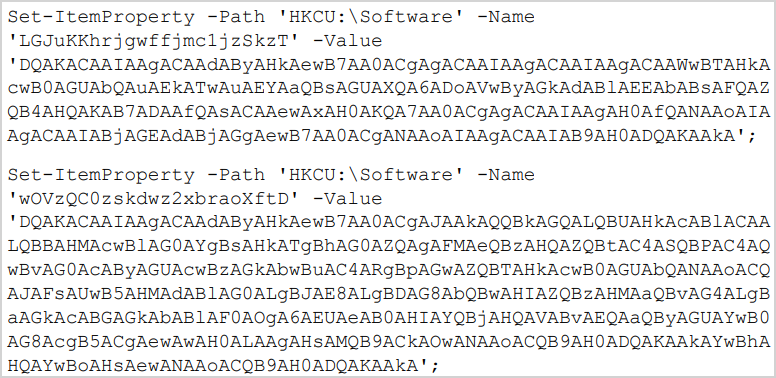
Finally, a new key is added to ‘HKCU\Software\Microsoft\Windows\CurrentVersion\Run’ to establish persistence on the target computer.
The recent Gamaredon campaign reflects an effort to increase operational stealth and effectiveness despite the threat group’s limited sophistication compared to other Russian state actors.
Symantec comments that various incremental but meaningful improvements in the threat group’s TTPs (tactics, techniques, and procedures) elevate the risks it poses to Western networks, especially considering Gamaredon’s unwavering tenacity.
-
Leak confirms OpenAI's GPT 4.1 is coming before GPT 5.0
OpenAI is working on yet another AI model reportedly called GPT-4.1, a successor to GPT-4o, which is expected to come before GPT 5.0
- April 12, 2025
- 12:09 PM
 1
1
-
Tycoon2FA phishing kit targets Microsoft 365 with new tricks
Phishing-as-a-service (PhaaS) platform Tycoon2FA, known for bypassing multi-factor authentication on Microsoft 365 and Gmail accounts, has received updates that improve its stealth and evasion capabilities.
- April 12, 2025
- 11:16 AM
 0
0
-
It's 2025 — Why Haven't We Solved Phishing Yet?!

Today's phishing attacks are bypassing defenses across email, network, and endpoint security solutions. Join Luke Jennings, VP R&D, as he breaks down why phishing attacks are more attractive then ever and how control groups are failing across all prevention techniques.
Sign up for the webinar to learn what we need to tackle the problem.
-
AI-hallucinated code dependencies become new supply chain risk
A new class of supply chain attacks named 'slopsquatting' has emerged from the increased use of generative AI tools for coding and the model's tendency to "hallucinate" non-existent package names.
- April 12, 2025
- 10:19 AM
 1
1






No comments:
Post a Comment