3 reports
DoorDash is the most popular food delivery app in the United States.
The company claims a 57% market share in the US and operates in three international markets: Australia, Canada, and Japan.
Today, the food delivery platform has more than 20 million active consumers and processed $9.9 billion in gross order value in Q1 2021.
How Many People Use DoorDash in 2022? [New Data]
Continue reading to find the latest stats on DoorDash in 2022:
- DoorDash Usage Statistics
- DoorDash customers
- DoorDash merchants
- DoorDash couriers
- DoorDash total orders
- DoorDash marketplace GOV
- DoorDash market share in the US
- DoorDash market share in select US metro areas
- DoorDash customer overlap in the US
- DoorDash revenue
- DoorDash operating expenses
- DoorDash employees
1✓
Hackers accessed DoorDash customer information and some partial payment data
Food delivery giant DoorDash has confirmed a data breach that exposed customers’ personal information.
In a blog post shared with TechCrunch ahead of its publication at market close, DoorDash said malicious hackers stole credentials from employees of a third-party vendor that were then used to gain access to some of DoorDash’s internal tools.
DoorDash said the attackers accessed names, email addresses, delivery addresses and phone numbers of DoorDash customers. For a “smaller subset” of users, hackers accessed partial payment card information, including card type and the last four digits of the card number.
For DoorDash delivery drivers, or Dashers, hackers accessed data that “primarily included name and phone number or email address.” Users of Wolt, the Helsinki-based online ordering and delivery company acquired by DoorDash last year, are unaffected.
DoorDash says that a “small percentage” of users were affected by the incident but declined to say how many users it currently has or provide an accurate number of affected users.
The company said it cut off the third-party vendor’s access to its systems after discovering “unusual and suspicious” activity.
DoorDash did not name the third-party vendor, which “provides services that require limited access to some internal tools,” according to DoorDash spokesperson Justin Crowley, but confirmed to TechCrunch that the vendor breach is linked to the phishing campaign that compromised SMS and messaging giant Twilio on August 4. Researchers linked these attacks to a wider phishing campaign by the same hacking group, dubbed “0ktapus,” which has stolen close to 10,000 employee credentials from at least 130 organizations, including Twilio, Signal, internet companies and outsourced customer service providers, since March.
DoorDash would not say when it discovered it was compromised, but its spokesperson said that the company took time to “fully investigate what happened, which users were impacted and how they were impacted” before disclosing the data breach.
DoorDash says that since discovering the compromise the company hired an unnamed cybersecurity expert to help with its ongoing investigation and is taking action to “further enhance DoorDash’s already robust security systems.”
This isn’t the first time that hackers have stolen customer data from DoorDash’s systems. In 2019, the company reported a data breach affecting 4.9 million customers, delivery workers and merchants who had their information stolen by hackers. It also blamed the breach on an unnamed third-party service provider.
Read more:
- DoorDash is ending its delivery partnership with Walmart
- DoorDash introduces dual ID verification for alcohol deliveries
- DoorDash tests a full-time employment option in New York as it launches ‘ultra-fast’ delivery
From the archives:
2✓
Twilio hackers hit over 130 orgs in massive Okta phishing attack

Hackers responsible for a string of recent cyberattacks, including those on Twilio, MailChimp, and Klaviyo, compromised over 130 organizations in the same phishing campaign.
This phishing campaign utilized a phishing kit codenamed '0ktapus' to steal 9,931 login credentials that the hackers then used to gain access to corporate networks and systems through VPNs and other remote access devices.
According to a Group-IB report, the 0ktapus campaign has been underway since at least March 2022, aiming to steal Okta identity credentials and 2FA codes and use them to carry out subsequent supply chain attacks.
These attacks were very successful, leading to a series of reported data breaches at Twilio, MailChimp, and Klaviyo, and an attempted attack against Cloudflare that was thwarted.
Based on the phishing domains created in this campaign, the threat actors targeted companies in multiple industries, including cryptocurrency, technology, finance, and recruiting.
Some of the targeted companies include T-Mobile, MetroPCS, Verizon Wireless, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, Evernote, AT&T, HubSpot, TTEC, and Best Buy.
.png)
The many arms of the 0ktapus
The attack begins with an SMS message and a link to a phishing page impersonating an Okta login page where victims are prompted to enter their account credentials and the 2FA codes.
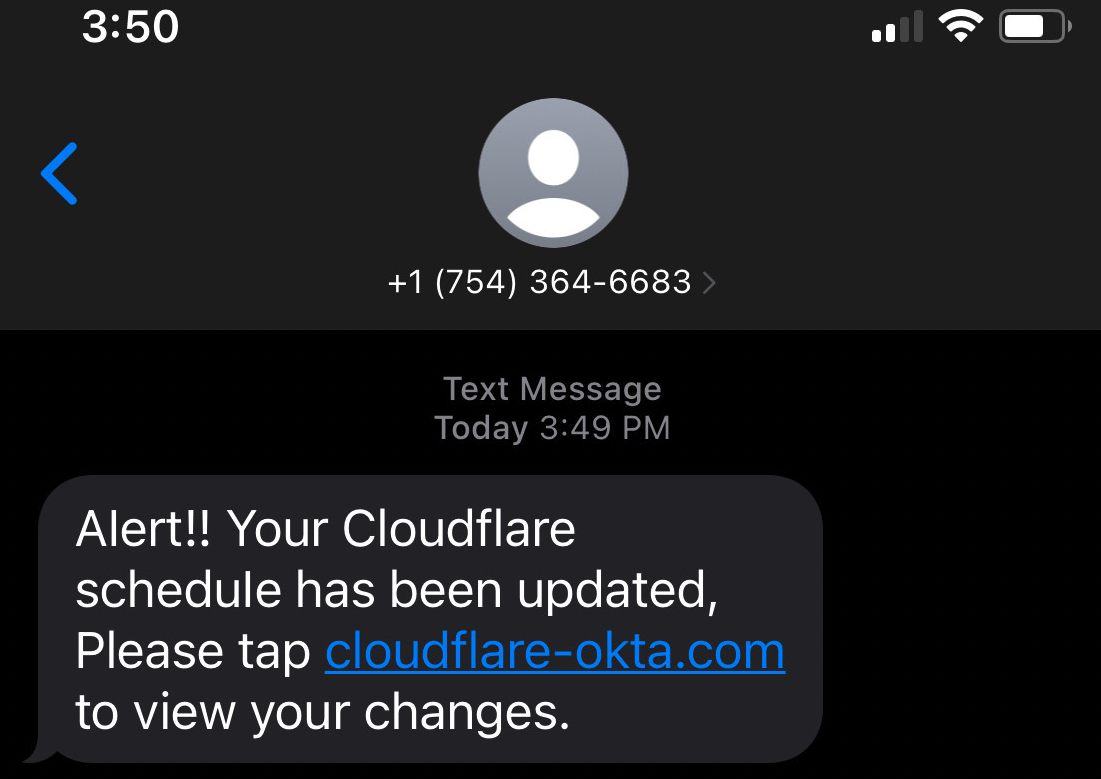
Okta is an identity-as-a-service (IDaaS) platform enabling employees to use a single login to access all software assets in their company.
Researchers discovered 169 unique phishing domains supporting the 0ktapus campaign, using the keywords "OKTA," "HELP," "VPN," and "SSO," such as the examples below.
t-mobile-okta[.]org
att-citrix[.]com
vzwcorp[.]co
mailchimp-help[.]com
slack-mailchimp[.]com
kucoin-sso[.]comThese sites feature the specific theming of the target companies, so they appear exactly like the genuine portals the employees are used to seeing in their daily login procedure.
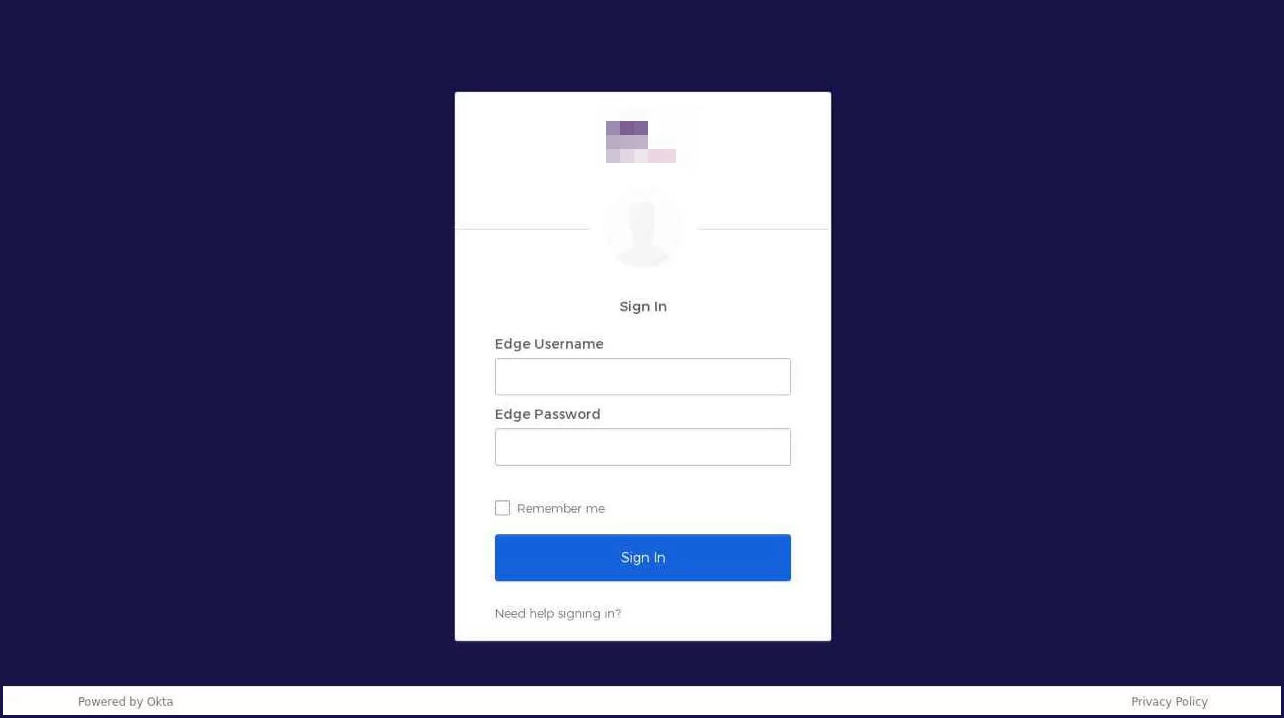
When victims enter their credentials and 2FA codes, the sites transmit them to a private Telegram channel where the threat actors can retrieve them.
The hackers then used these login credentials to gain access to corporate VPNs, networks, and internal customer support systems to steal customer data. This customer data was then used to perform further supply-chain attacks, as we saw with DigitalOcean and Signal.
Based on the disclosures of past victims, the threat actors commonly targeted data belonging to companies in the cryptocurrency industry.
Group-IB says that the threat actors managed to steal 9,931 user credentials from 136 companies, 3,129 records with emails, and 5,441 records with MFA codes, with the majority of the compromised organizations located in the U.S.
.jpg)
Of those, almost half belong to the software and telecom sector, while finance, business services, education, and retail also had significant shares.
Unmasking user "X"
Group-IB's investigators leveraged the little info "hiding" in the phishing kit to find the admin account of the Telegram channel used for account data exfiltration.
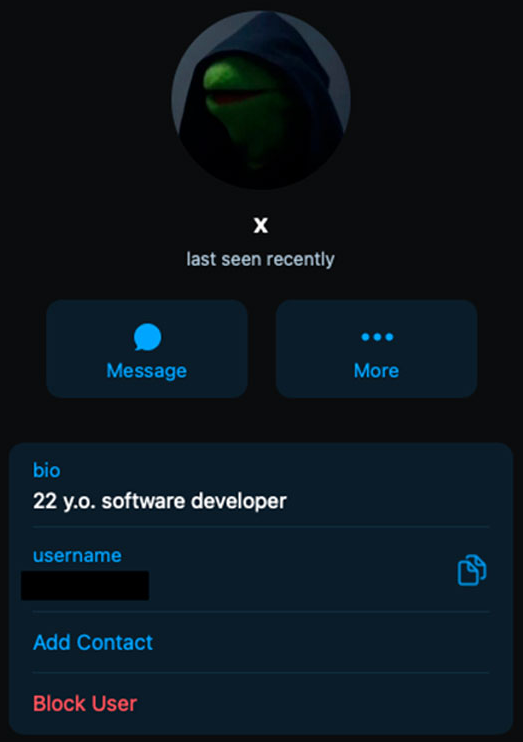
Tracing back the user's activity, the threat intelligence firm found that in 2019, the user named "X," posted something pointing to their Twitter account.
From there, the analysts found a GitHub account linked to the hacker, who used the nickname "Subject X" at the time. Group-IB says this account had a location of North Carolina, United States, associated with it.
Group-IB claims to have more information about the alleged identity of the threat actor, but it reserved further details for law enforcement agencies.
✓ ONE MORE
DoorDash says some customers' details accessed by 'unauthorized party'
A Doordash delivery bag is seen in Brooklyn, New York City, U.S., May 9, 2022. REUTERS/Andrew Kelly/File Photo
Register now for FREE unlimited access to Reuters.com
Aug 25 (Reuters) - DoorDash Inc (DASH.N) on Thursday said personal details of some customers and drivers had been accessed by an "unauthorized party" in a phishing attack on a third-party vendor.
The U.S. food delivery firm said details accessed included order and partial payment card information, email, delivery address and phone number of some customers.
The unauthorized party, which used stolen credentials of the vendor's employees to gain access to some internal tools, also got hold of names, phone numbers or email addresses of some drivers, DoorDash added. (https://bit.ly/3ctgYGa)
The company said it quickly disabled the vendor's access to its system after detecting unusual and suspicious activity from the vendor's computer network.
"We have no reason to believe that affected personal information has been misused for fraud or identity theft," DoorDash said.
Register now for FREE unlimited access to Reuters.com
Reporting by Praveen Paramasivam in Bengaluru; Editing by Vinay Dwivedi
.png)
.png)
.jpg)
.jpg)


No comments:
Post a Comment