“Users with infected Android devices that connect to free or public Wi-Fi networks may spread the malware to other devices on the network if the Wi-Fi network they are connected to is vulnerable,” Thursday’s report stated. “Kaspersky experts are concerned about the potential for the DNS changer to be used to target other regions and cause significant issues...
Hacker group incorporates DNS hijacking into its malicious website campaign
Biz & IT / Information Technology
The DNS hijacking threat can be especially high for people using public Wi-Fi.

DNS hijacking concept.
"Researchers have uncovered a malicious Android app that can tamper with the wireless router the infected phone is connected to and force the router to send all network devices to malicious sites.
✓ The malicious app, found by Kaspersky, uses a technique known as DNS (Domain Name System) hijacking. Once the app is installed, it connects to the router and attempts to log in to its administrative account by using default or commonly used credentials, such as admin:admin. When successful, the app then changes the DNS server to a malicious one controlled by the attackers. From then on, devices on the network can be directed to imposter sites that mimic legitimate ones but spread malware or log user credentials or other sensitive information.
Capable of spreading widely
“We believe that the discovery of this new DNS changer implementation is very important in terms of security,” Kaspersky researchers wrote. “The attacker can use it to manage all communications from devices using a compromised Wi-Fi router with the rogue DNS settings.”
The researchers continued: “Users connect infected Android devices to free/public Wi-Fi in such places as cafes, bars, libraries, hotels, shopping malls, and airports. When connected to a targeted Wi-Fi model with vulnerable settings, the Android malware will compromise the router and affect other devices as well. As a result, it is capable of spreading widely in the targeted regions.”
DNS is the mechanism that matches a domain name like ArsTechnica.com to 18.188.231.255, the numerical IP address where the site is hosted. DNS lookups are performed by servers operated by a user’s ISP or by services from companies such as Cloudflare or Google. By changing the DNS server address in a router’s administrative panel from a legitimate one to a malicious one, attackers can cause all devices connected to the router to receive malicious domain lookups that lead to lookalike sites used for cybercrime.
The Android app is known as Wroba.o, and has been in use for years in various countries, including the US, France, Japan, Germany, Taiwan, and Turkey. Curiously, the DNS hijacking technique the malware is capable of is being used almost exclusively in South Korea. From 2019 to most of 2022, attackers lured targets to malicious sites that were sent through text messages, a technique known as smishing. Late last year, the attackers incorporated DNS hijacking into their activities in that Asian nation.
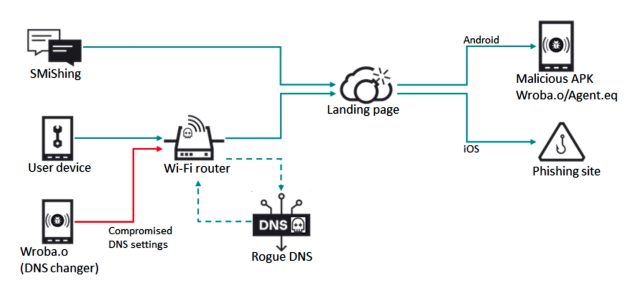
Enlarge / Infection flow with DNS hijacking and smishing.
The attackers, known in the security industry as Roaming Mantis, designed the DNS hijacking to work only when devices visit the mobile version of a spoofed website, most likely to ensure the campaign goes undetected..." READ MORE
Roaming Mantis implements new DNS changer in its malicious mobile app in 2022
Roaming Mantis (a.k.a Shaoye) is well-known as a long-term cyberattack campaign that uses malicious Android package (APK) files to control infected Android devices and steal device information; it also uses phishing pages to steal user credentials, with a strong financial motivation.
Kaspersky has been
investigating the actor’s activity throughout 2022, and we observed a
DNS changer function used for getting into Wi-Fi routers and undertaking
DNS hijacking. This was newly implemented in the known Android malware
Wroba.o/Agent.eq (a.k.a Moqhao, XLoader), which was the main malware
used in this campaign. . .
DNS changer via malicious mobile app
"Back in 2018, Kaspersky first saw Roaming Mantis activities targeting the Asian region, including Japan, South Korea and Taiwan. At that time, the criminals compromised Wi-Fi routers for use in DNS hijacking, which is a very effective technique. It was identified as a serious issue in both Japan and South Korea. Through rogue DNS servers, all users accessing a compromised router were redirected to a malicious landing page. From mid-2019 until 2022, the criminals mainly used smishing instead of DNS hijacking to deliver a malicious URL as their landing page. The landing page identified the user’s device platform to provide malicious APK files for Android or redirect to phishing pages for iOS.
Investigation of landing page statistics
As we mentioned above, the main target regions of the DNS changer were mainly South Korea. However, the attackers not only targeted South Korea but also France, Japan, Germany, the United States, Taiwan, Turkey and other regions. Smishing has been observed to be the main initial infection method in these regions, except South Korea, though we should keep in mind that the criminals may update the DNS changer function to target Wi-Fi routers in those regions in the near future.
In December 2022, we confirmed some landing pages and got an understanding of the number of downloaded APK files. Below are some examples of the download URLs from the landing page statistics.
| Target regions | Landing page IP | # of Downloaded APK | Examples of download URLs |
| Japan | 103.80.134[.]40 103.80.134[.]41 103.80.134[.]42 103.80.134[.]48 103.80.134[.]49 103.80.134[.]50 103.80.134[.]51 103.80.134[.]52 103.80.134[.]53 103.80.134[.]54 |
24645 | http://3.wubmh[.]com/chrome.apk http://5.hmrgt[.]com/chrome.apk http://9v.tbeew[.]com/chrome.apk |
| Austria | 199.167.138[.]36 199.167.138[.]38 199.167.138[.]39 199.167.138[.]40 |
7354 | http://8.ondqp[.]com/chrome.apk http://5c2d.zgngu[.]com/chrome.apk http://d.vbmtu[.]com/chrome.apk |
| France | 199.167.138[.]48 199.167.138[.]49 199.167.138[.]51 199.167.138[.]52 |
7246 | http://j.vbrui[.]com/chrome.apk http://vj.nrgsd[.]com/chrome.apk http://k.uvqyo[.]com/chrome.apk |
| Germany | 91.204.227[.]144 91.204.227[.]145 91.204.227[.]146 |
5827 | https://mh.mgtnv[.]com/chrome.apk http://g.dguit[.]com/chrome.apk http://xtc9.rvnbg[.]com/chrome.apk |
| South Korea | 27.124.36[.]32 27.124.36[.]34 27.124.36[.]52 27.124.39[.]241 27.124.39[.]242 27.124.39[.]243 |
508 | http://m.naver.com/chrome.apk https://m.daum.net/chrome.apk (legitimate domains because DNS hijacking) |
| Turkey | 91.204.227[.]131 91.204.227[.]132 |
381 | http://y.vpyhc[.]com/chrome.apk http://r48.bgxbm[.]com/chrome.apk http://t9o.qcupn[.]com/chrome.apk |
| Malaysia | 134.122.137[.]14 134.122.137[.]15 134.122.137[.]16 |
154 | http://3y.tmztp[.]com/chrome.apk http://1hy5.cwdqh[.]com/chrome.apk http://53th.xgunq[.]com/chrome.apk |
| India | 199.167.138[.]41 199.167.138[.]43 199.167.138[.]44 199.167.138[.]45 |
28 | http://w3.puvmw[.]com/chrome.apk http://o.wgvpd[.]com/chrome.apk http://kwdd.cehsg[.]com/chrome.apk |
The number of downloaded APK
files was reset at the beginning of December 2022. After a few days, we
got the above numbers from the landing pages, and it showed us that
Android malware was still being actively downloaded for some targeted
regions. It also showed us that the most affected region was Japan,
followed by Austria and France. From this investigation, we noted that
the criminals have now also added Austria and Malaysia to their main
target regions. . .
Geography based on KSN
Our telemetry showed the detection rate of Wroba.o (Trojan-Dropper.AndroidOS.Wroba.o) for each region such as France (54.4%), Japan (12.1%) and the United States (10.1%). When compared with the landing page statistics above, the results are similar in that many detections have been observed in France, Japan, Austria and Germany. On the other hand, while we had previously monitored landing pages for the United States, this time we haven’t seen those landing pages.
Conclusions
From 2019 to 2022, Kaspersky observed that the Roaming Mantis campaign mainly used smishing to deliver a malicious URL to their landing page. In September 2022, we analyzed the new Wroba.o Android malware and discovered a DNS changer function that was implemented to target specific Wi-Fi routers used mainly in South Korea. Users with infected Android devices that connect to free or public Wi-Fi networks may spread the malware to other devices on the network if the Wi-Fi network they are connected to is vulnerable. Kaspersky experts are concerned about the potential for the DNS changer to be used to target other regions and cause significant issues. Kaspersky products detect this Android malware as HEUR:Trojan-Dropper.AndroidOS.Wroba.o or HEUR:Trojan-Dropper.AndroidOS.Agent.eq, providing protection from this cyberthreat to Kaspersky’s customers and users.
IoCs
MD5 of Wroba.o
2036450427a6f4c39cd33712aa46d609
8efae5be6e52a07ee1c252b9a749d59f
95a9a26a95a4ae84161e7a4e9914998c
ab79c661dd17aa62e8acc77547f7bd93
d27b116b21280f5ccc0907717f2fd596
f9e43cc73f040438243183e1faf46581
Domains of landing pages:
1hy5.cwdqh[.]com
3.wubmh[.]com
3y.tmztp[.]com
53th.xgunq[.]com
5c2d.zgngu[.]com
5.hmrgt[.]com
8.ondqp[.]com
9v.tbeew[.]com
d.vbmtu[.]com
g.dguit[.]com
j.vbrui[.]com
k.uvqyo[.]com
kwdd.cehsg[.]com
mh.mgtnv[.]com
o.wgvpd[.]com
r48.bgxbm[.]com
t9o.qcupn[.]com
vj.nrgsd[.]com
w3.puvmw[.]com
xtc9.rvnbg[.]com
y.vpyhc[.]com
IPs of landing pages:
103.80.134[.]40
103.80.134[.]41
103.80.134[.]42
103.80.134[.]48
103.80.134[.]49
103.80.134[.]50
103.80.134[.]51
103.80.134[.]52
103.80.134[.]53
103.80.134[.]54
134.122.137[.]14
134.122.137[.]15
134.122.137[.]16
199.167.138[.]36
199.167.138[.]38
199.167.138[.]39
199.167.138[.]40
199.167.138[.]41
199.167.138[.]43
199.167.138[.]44
199.167.138[.]45
199.167.138[.]48
199.167.138[.]49
199.167.138[.]51
199.167.138[.]52
27.124.36[.]32
27.124.36[.]34
27.124.36[.]52
27.124.39[.]241
27.124.39[.]242
27.124.39[.]243
91.204.227[.]131
91.204.227[.]132
91.204.227[.]144
91.204.227[.]145
91.204.227[.]146
Rogue DNS:
193.239.154[.]15
193.239.154[.]16
193.239.154[.]17
193.239.154[.]18
193.239.154[.]22
Hardcoded malicious accounts of vk.com to obtain live rogue DNS servers:
id728588947
Providing live rogue DNS servers:
107.148.162[.]237:26333/sever.ini
Suspicious accounts/pages of some legitimate services for obtaining C2s
http://m.vk[.]com/id668999378?act=info
http://m.vk[.]com/id669000526?act=info
http://m.vk[.]com/id669000956?act=info
http://m.vk[.]com/id674309800?act=info
http://m.vk[.]com/id674310752?act=info
http://m.vk[.]com/id730148259?act=info
http://m.vk[.]com/id730149630?act=info
http://m.vk[.]com/id761343811?act=info
http://m.vk[.]com/id761345428?act=info
http://m.vk[.]com/id761346006?act=info
https://www.youtube[.]com/channel/UCP5sKzxDLR5yhO1IB4EqeEg/about
https://docs.google[.]com/document/d/1s0n64k12_r9MglT5m9lr63M5F3e-xRyaMeYP7rdOTrA/mobilebasic
https://docs.google[.]com/document/d/1IIB6hhf_BB1DaxzC1aNfLEG1K97LsPsN55AT5pFWYKo/mobilebasic
C&C
91.204.227[.]32
91.204.227[.]33
92.204.255[.]173
91.204.227[.]39
118.160.36[.]14
198.144.149[.]131








No comments:
Post a Comment