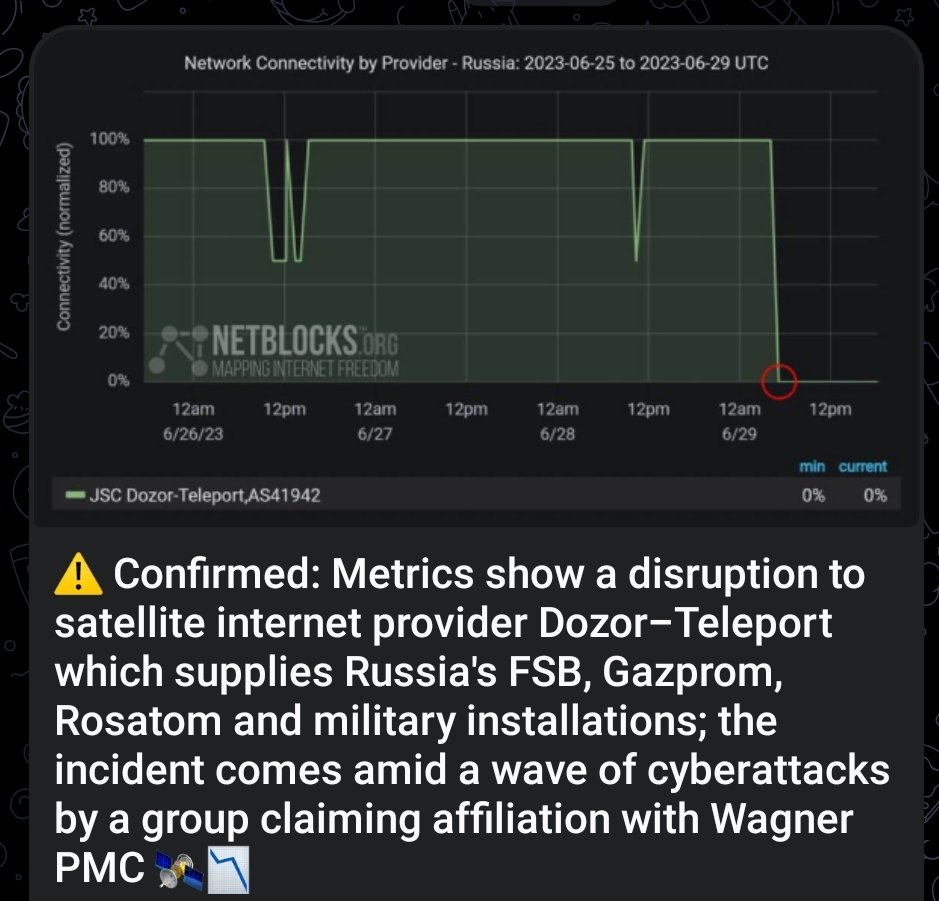
Russian satellite telecom Dozor hit by hackers
It was yet another example of the ongoing cyberwar various factions have been waging against Russian companies since the invasion of Ukraine in February 2022.
The hackers claimed affiliation with the Wagner mercenary group, which staged a short-lived mutiny against Russia’s military leadership a few days before.

Dozor-Teleport, a Russian satellite communications provider used by the country’s Ministry of Defense and security services, was hit by hackers aligned with the private military corporation (PMC) Wagner.
- According to a pro-Ukrainian hacker and malware historian Herm1t, attackers could’ve severely damaged client equipment and the network core.
According to Herm1t, Dozor-Teleport is used by Russia’s Ministry of Defense, ships of the Northern Fleet, the Federal Security Service (FSB), Rosatom, and other organizations.
- The network is also used by users in remote areas, such as tankers of Russia’s energy companies like Gazprom.
- The incident affected tens of thousands of terminals across Europe, demonstrating the dangers of relying on communications on commercial satellites.
- Interestingly, the culprits behind the attack try to portray themselves as associated with Yevgeny Prigozhin-led PMC Wagner, which recently attempted a march on Moscow. Earlier this week, researchers discovered a ransomware strain called Wagner ,that infects user devices and invites them to join the PMC Wagner.

The attackers supposedly defaced several Russian websites, publishing a message from the PMC Wagner claiming responsibility for the attacks.
- However, the Telegram page of the supposed attackers is not the same one used by PMC Wagner.
If confirmed, the attack would not be the first time hackers targeted Russian satellite networks.
- Last year, pro-Ukrainian hackers said they penetrated Gonets, a Russian low Earth orbit (LEO) satellite communications network, deleting a database that was crucial to its functioning.
- Meanwhile, a group of hackers affiliated with Anonymous, NB65, said they disrupted Russia’s vehicle monitoring system by targeting Roscosmos, the Russian space agency.
Updated on June 30th [11:50 AM GMT].
More from Cybernews:
Idea of separate US Cyber Force raises eyebrows
Pornhub accused of illegal data collection in Europe
Rise of the script kiddie: a tenth of children say they can hack websites
Hacker sets up Tor-based online shop to sell access to firms
City in Finland will pay up to €20 an hour for cycling
Subscribe to our newsletter
The Cyberattack on Dozor-Teleport
Late on Wednesday, a cyberattack hit Dozor-Teleport, the operator of the satellite communications system used by the Russian military. The attack resulted in the system going mostly offline, with only partial restoration observed on Thursday. Analysts have drawn parallels to a similar incident in Ukraine, where their satellite system was targeted during the early stages of the conflict between the two countries.
Shifting to Terrestrial Networks
During the outage, Dozor-Teleport took measures to mitigate the impact on users. JD Work, a cyberspace professor at the National Defense University, confirmed that some users were switched to terrestrial networks. However, four networks were affected, with one taken over by Dozor's parent company, Amtel-Svyaz. The company has not released an official statement regarding the cause of the disruption.
Claimed Responsibility and Potential Actors
At least two groups have claimed responsibility for the cyberattack. One group identifies as a hacktivist organisation, while the other alleges affiliation with the Wagner Group, a group of mercenaries who recently mutinied and marched towards Moscow. The attackers have stated that they deployed malicious software to the satellite terminals, prompting security experts to scramble for testing and analysis.
The Complex Landscape of Hacktivism
The ongoing conflict between Russia and Ukraine has witnessed numerous cyberattacks by self-proclaimed hacktivists. However, many of these individuals and groups are suspected of coordinating with or acting as cover for military forces. The situation becomes even more intricate with the potential for false connections to the Wagner Group. While some may aim to create division in Russia, a genuine association could indicate the continuation of mutinous actions in cyberspace.
Impact and Significance
Despite Dozor-Teleport's relatively modest estimated annual revenue of $10 million, its satellite services play a crucial role in serving the Russian military and other federal services. The extent of the impact will depend on the duration of the shutdown and whether customers have alternative reliable and secure means of communication. While satellite communications often serve as backup options, military units on the move rely heavily on them.
Brian Weeden, a director at the Secure World Foundation, suggests that unless some customers solely rely on the satellite system, the overall impact may not be crippling. Nonetheless, the incident raises concerns about the vulnerability of critical infrastructures in the face of cyber threats.
The Rarity of Satellite Hacks
Satellite hacks are infrequent occurrences; when they do happen, they are often undisclosed. The hacking attack on Ukraine's Viasat service in February 2022 is considered one of the most successful attacks during the ongoing conflict. In response, SpaceX's Starlink service emerged as a vital national alternative, successfully withstanding multiple hacking attempts.
While experts initially attributed the Viasat hack to Russia's military intelligence arm, the GRU, the possibility exists that Wagner mercenaries closely collaborated with the GRU and acquired techniques employed in that attack. If so, their ability to redirect those techniques towards Russia's Dozor system would have been facilitated.
Uncertain Attribution and Western Involvement
As the cyberattack unfolded, questions regarding its attribution arose. A U.S. military spokesperson declined to comment, leaving the situation ambiguous.
#Cyberwarfare #SatelliteHack #VulnerabilityExposed #RussianMilitaryHack #GlobalSecurityAlert
DISCLAIMER: This is a summary / rewrite from The Washington Post; read the original article
___________________________________________________
___________________________________________________






No comments:
Post a Comment