CISA warns of critical Citrix ShareFile flaw exploited in the wild
- August 16, 2023
- 05:31 PM
- 0

The service also offers a 'Storage zones controller' solution that allows enterprise customers to configure their private data storage to host files, whether on-premise or at supported cloud platforms, such as Amazon S3 and Windows Azure.
- On June 13th, 2023, Citrix released a security advisory on a new ShareFile storage zones vulnerability tracked as CVE-2023-24489 with a critical severity score of 9.8/10, which could allow unauthenticated attackers to compromise customer-managed storage zones.
- Cybersecurity firm AssetNote disclosed the vulnerability to Citrix, warning in a technical writeup that the flaw is caused by a few small errors in ShareFile's implementation of AES encryption.
- Using this flaw, a threat actor could upload a web shell to a device to gain full access to the storage and all its files.
- One ransomware operation, known as Clop, has taken a particular interest in targeting these types of flaws, using them in widescale data theft attacks since 2021, when they exploited a zero-day flaw in the Accellion FTA solution.
Active exploitation
- On July 26th, GreyNoise began monitoring for attempts to exploit the vulnerability. After CISA warned about the flaw today, GreyNoise updated its report to say there had been a significant uptick in attempts by different IP addresses.
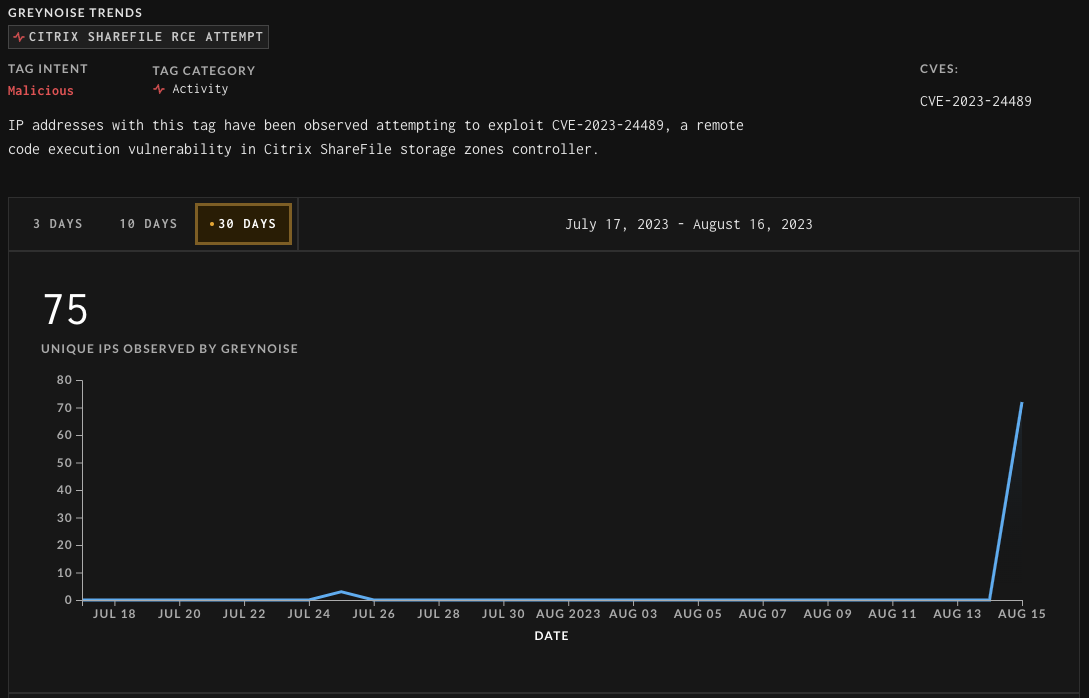
Source: GreyNoise
- While no publicly known exploitation or data theft has been linked to this flaw, CISA now requires Federal Civilian Executive Branch (FCEB) agencies to apply patches for this bug by September 6th, 2023.
However, due to the highly targeted nature of these bugs, it would be strongly advised that all organizations apply the updates as soon as possible.
LAWRENCE ABRAMS
Lawrence Abrams is the owner and Editor in Chief of BleepingComputer.com. Lawrence's area of expertise includes Windows, malware removal, and computer forensics. Lawrence Abrams is a co-author of the Winternals Defragmentation, Recovery, and Administration Field Guide and the technical editor for Rootkits for Dummies.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
File-sharing site Anonfiles shuts down due to overwhelming abuse
- August 16, 2023
- 07:25 PM
- 1

- Anonfiles is an anonymous file-sharing site that allows people to share files anonymously without their activity being logged.
- However, it soon became one of the most popular file-sharing services used by threat actors to share samples of stolen data, stolen credentials, and copyrighted material.
As spotted by cybersecurity researcher g0njxa, the Anonfiles operators have now shut down the service, stating that their proxy provider recently shut them down and that they can no longer deal with the overwhelming amount of abusive material uploaded to the site.
The statement shown on Anonfiles site is reproduced in its entirety below:
"After trying endlessly for two years to run a file sharing site with user anonymity we have been tired of handling the extreme volumes of people abusing it and the headaches it has created for us.
Maybe it is hard to understand but after tens of million uploads and many petabytes later all work of handling abuse was automated through all available channels to be fast as possible.
We have auto banned contents of hundreds of thousands files.
Banned file names and also banned specific usage patterns connected to abusive material to the point where we did not care if we accidental delete thousands of false positive in this process.
- Even after all this the high volume of abuse will not stop.
- This is not the kind of work we imagine when acquiring it and recently our proxy provider shut us down.
This can not continue.
Domain 4sale.
domain@anonfiles.com"
For example, when attempting to download a file from Anonfiles, users said you would often be first redirected to a site that downloaded an ISO file using the same name as the file you thought you were downloading.
- However, these ISO files contained various malware, including information-stealing malware, remote access trojans, and ad clickers.
- In 2021, CronUp researcher Germán Fernández warned that Anonfiles malvertising was pushing the RedLine Stealer malware, a notorious information-stealing malware that steals your credentials and cryptocurrency wallets.
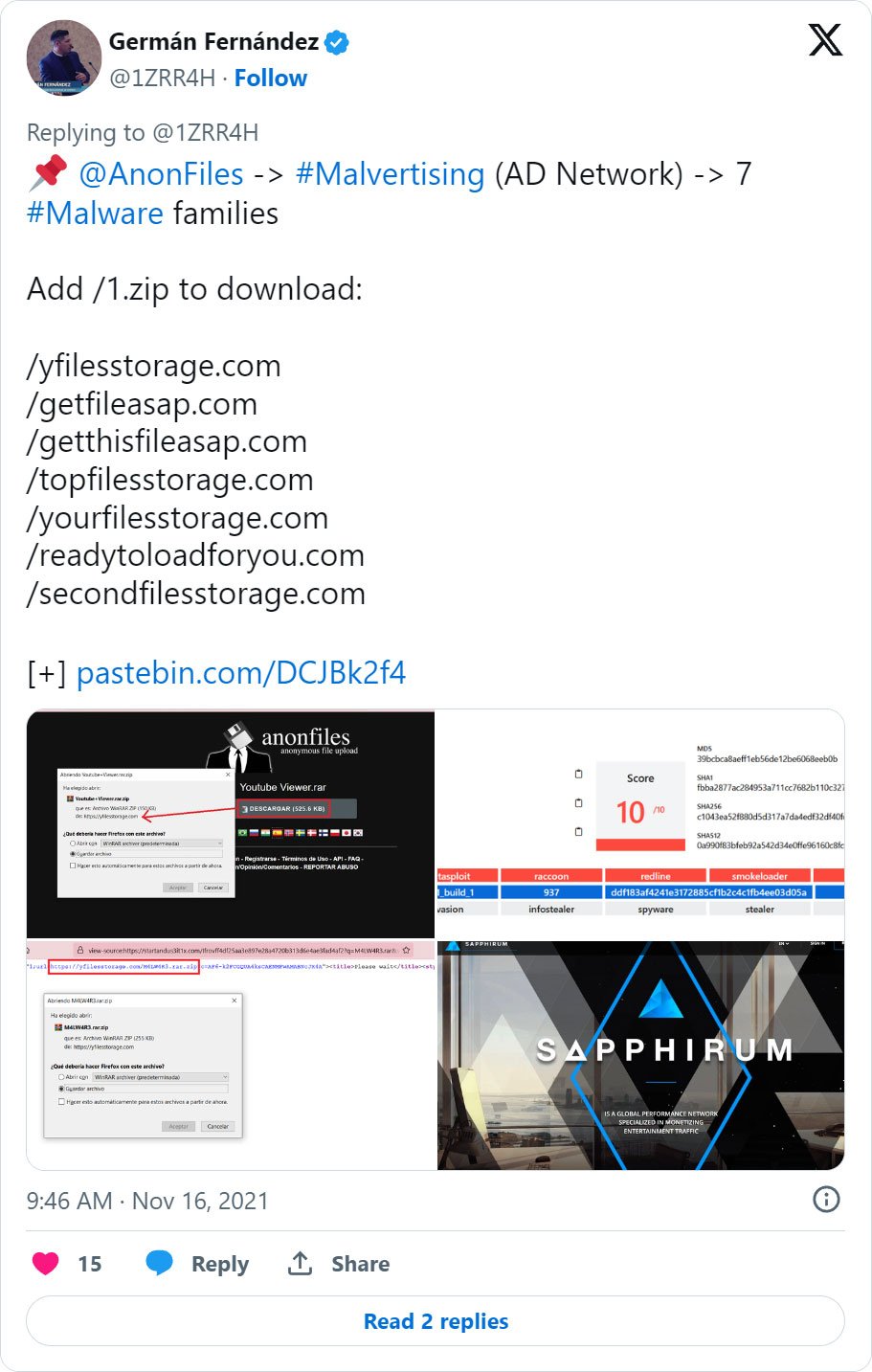
Other malvertising campaigns seen by Fernández and Malwarebytes on Anonfiles pushed search hijacking extensions, Amadey botnet, Vidar stealer, and even STOP ransomware.
The Anonfiles operators are now looking for someone to purchase their domain, likely to launch their own file sharing service.
However, in the interim, the shutdown will cause many files used by cybersecurity researchers and threat actors alike to no longer be available.
Related Articles:
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-
Google released first quantum-resilient FIDO2 key implementation
Google has announced the first open-source quantum resilient FIDO2 security key implementation, which uses a unique ECC/Dilithium hybrid signature schema co-created with ETH Zurich.
- AUGUST 16, 2023
- 02:35 PM
 0
0
-
Pick up new coding skills with 74% off this premium coding training
Coding is only going to become more important as both a specialized and general skill. This 14-course bundle gives you top instruction from experienced coders for $39.99, 74% off the $154 MSRP.
- AUGUST 16, 2023
- 02:11 PM
 0
0
-
Massive 400,000 proxy botnet built with stealthy malware infections
A new campaign involving the delivery of proxy server apps to Windows systems has been uncovered, where users are reportedly involuntarily acting as residential exit nodes controlled by a private company.
- AUGUST 16, 2023
- 11:31 AM
 0
0
-
Major U.S. energy org targeted in QR code phishing attack
A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security.
- AUGUST 16, 2023
- 10:16 AM
 0
0
- SPONSORED CONTENT
Just announced: AI and security standards keynotes at mWISE
Get ready for the mWISE cybersecurity conference from Mandiant, taking place September 18-20, 2023 in Washington, DC. mWISE just announced new keynote panels focused on Artificial Intelligence (AI) and advanced adversaries.
- AUGUST 16, 2023
- 10:02 AM
 0
0
-
Score a refurbished Dell laptop in near-mint condition for under $140
While supplies last, you can get this 14" Dell Latitude E5450 for $137.99, down a full 31% from the original sale price.
- AUGUST 16, 2023
- 07:16 AM
 0
0
-
Ivanti Avalanche impacted by critical pre-auth stack buffer overflows
Two stack-based buffer overflows collectively tracked as CVE-2023-32560 impact Ivanti Avalanche, an enterprise mobility management (EMM) solution designed to manage, monitor, and secure a wide range of mobile devices.
- AUGUST 15, 2023
- 06:05 PM
 0
0
-
LinkedIn accounts hacked in widespread hijacking campaign
LinkedIn is being targeted in a wave of account hacks resulting in many accounts being locked out for security reasons or ultimately hijacked by attackers.
- AUGUST 15, 2023
- 05:21 PM
 4
4
-
Almost 2,000 Citrix NetScaler servers backdoored in hacking campaign
A threat actor has compromised close to 2,000 thousand Citrix NetScaler servers in a massive campaign exploiting the critical-severity remote code execution tracked as CVE-2023-3519.
- AUGUST 15, 2023
- 03:41 PM
 0
0
-
Save 85% on a lifetime of learning with International Open Academy
Lifelong learning keeps your mind sharp and your career on track. Get over 200 courses across a wide range of subjects for $59.99, 85% off the $400 MSRP, and the best price on the web.
- AUGUST 15, 2023
- 02:09 PM
 0
0
-
Raccoon Stealer malware returns with new stealthier version
The developers of Raccoon Stealer information-stealing malware have ended their 6-month hiatus from hacker forums to promote a new 2.3.0 version of the malware to cyber criminals.
- AUGUST 15, 2023
- 01:24 PM
 0
0
-
New CVE-2023-3519 scanner detects hacked Citrix ADC, Gateway devices
Mandiant has released a scanner to check if a Citrix NetScaler Application Delivery Controller (ADC) or NetScaler Gateway Appliance was compromised in widespread attacks exploiting the CVE-2023-3519 vulnerability.
- AUGUST 15, 2023
- 11:32 AM
 0
0
















No comments:
Post a Comment