FBI, Federal Judge Agree Fighting Botnets Means Allowing The FBI To Remotely Install Software On People’s Computers
from the all's-fair-in-love-and-cyber-war dept
The ends aren’t always supposed to justify the means. And a federal agency that already raised the hackles of defense lawyers around the nation during a CSAM investigation probably shouldn’t be in this much of hurry to start sending out unsolicited software to unknowing recipients.
But that’s the way things work now. As a result of the DOJ-propelled push to change Rule 41 jurisdiction limitations, the FBI is now able to infect computers anywhere in the United States using a single warrant. In the “Playpen” case, the software was used to obtain information about users and devices visiting a seized (but still live) dark web CSAM site.
A couple of years later, the lack of jurisdiction limitations were used for something a bit more useful for even innocent computer users: the FBI secured a single warrant authorizing it to send its botnet-battling software to computers all over the nation, resulting in the disinfection of thousands of computers.
And while this all seems like a net positive for US computer users, the underlying facts are a bit more worrying: judges will allow the FBI to place its software on any user’s computer at any time, provided it can convince a court the end result will be something other than a massive number of privacy violations.
It’s inarguable that disrupting botnets is a public good. But is it inarguable that disruption should occur by any means necessary… or, at least, any means convenient. The disruption of another botnet has been achieved with the assistance of the FBI, a federal judge, and some government software deployed without notification to an unknown number of infected devices.
The FBI quietly wiped malicious programs from more than 700,000 computers around the world in recent days, the agency said Tuesday, part of an operation to take down a major component of the cybercrime ecosystem.
[…]
The FBI got a court’s permission to proceed with the operation on Aug. 21, according to a copy of the warrant. Agents proceeded to hack into Qakbot’s central computer infrastructure four days later, the FBI announced, and forced it to tell the computers in its botnet to stop listening to Qakbot.
An unnamed FBI “source” added this:
Victims will not be notified that their devices had been fixed or that they had ever been compromised, he said.
All of that was accomplished with a five-page warrant [PDF] that doesn’t have much to say about the probable cause compelling this invasion of users’ computers. The warrant authorized the FBI to, in effect, “search” every computer it sent its software to. . .
Given that lack of disclosure, it’s going to make it almost impossible to challenge evidence of other criminal activity that might have been obtained during this mass search. It also means users aren’t able to double-check the FBI’s work by ensuring their devices are free of either botnet infections or FBI software.
And there’s a very good chance the FBI handled this all honestly and decently and actually performed a useful public service.
Filed Under: 4th amendment, botnets, fbi, qakbot, remote installs, warrant
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
___________________________________________________________________________________
Qakbot Botnet Disruption
On Tuesday 29th August 2023, the US Department of Justice (DoJ) and US Federal Bureau of Investigations (FBI) – along with law enforcement partners in France, Germany, the Netherlands, and the United Kingdom – announced a disruption action against the very long running Qakbot botnet.
Qakbot (also known as QBot, Pinkslipbot, Quakbot and Oakbot) has been active since around 2007, having initially been developed as information stealer and banking trojan malware, before later becoming primarily a distribution network for other malware/ransomware. See Malpedia’s timeline for more information about its lengthy evolution, and CISA’s advisory for Indicators of Compromise (IOCs) and mitigation information.
In recent years, Qakbot has been used as an initial infection vector by many ransomware groups including Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta. This has likely enabled significant financial losses globally.
The outcomes from the coordinated law enforcement action included:
- deleting the Qakbot malware from infected victim computers (to reduce the risk of further harm)
- taking down the Qakbot technical infrastructure
- seizing $8.6M of alleged illicit cryptocurrency profits.
As part of the takedown, the FBI was able to gain access to Qakbot infrastructure and identify over 700,000 computers worldwide that appear to have been infected with Qakbot, including more than 200,000 in the United States. To disrupt the botnet, the FBI was able to redirect Qakbot botnet traffic to and through servers controlled by the FBI, which in turn instructed infected computers in the United States and elsewhere to download a file created by law enforcement that would uninstall the Qakbot malware – thus preventing additional malware from being deployed on victim systems in future.
More detailed information is available in the DoJ court documents, including the hash of the Qakbot Uninstall file (SHA-256 7cdee5a583eacf24b1f142413aabb4e556ccf4ef3a4764ad084c1526cc90e117) and associated search warrants. Independent technical analysis of observed deletion activity was reported by Secureworks.
The scope of this law enforcement action was limited to information installed on the victim computers by the Qakbot actors. It did not extend to remediating other malware already installed on the victim computers and did not involve access to or modification of the information of the owners and users of the infected computers. It is therefore important that anyone who is notified that they might have been infected with Qakbot also looks for and remediates other malware infections that are likely also running on the same computer. Even after the removal of Qakbot, they may still be infected with other malware and be a part of other botnets, so at risk from cybercriminals...
Recent Articles
Qakbot Historical Bot Infections Special Report
SEPTEMBER 8, 2023On Tuesday 29th August 2023, the US DoJ and FBI, together with other global law enforcement partners, announced a disruption… Read more »
QAKBOT HISTORICAL BOT INFECTIONS – DATA ANALYSIS
We are publicly sharing some high level analysis of the Qakbot historical bot infections dataset from the period between July 2019 to August 2023. For each of the images below you can click on it to view a higher resolution version.
The world maps below show the total number of Qakbot infections logged per country:
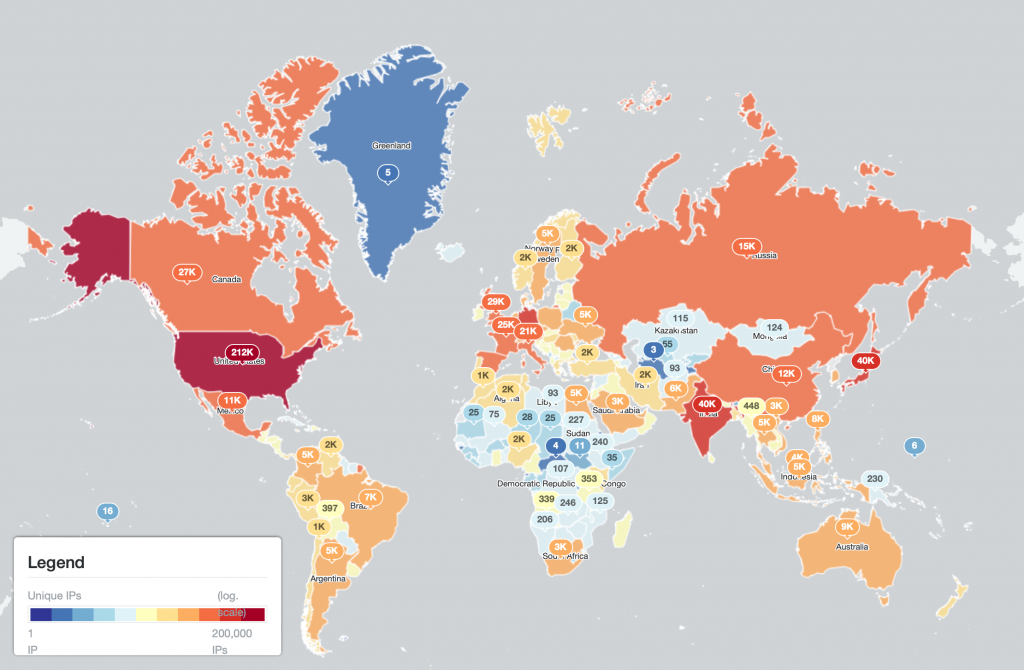 (Qakbot infections per country – linear scale)
(Qakbot infections per country – linear scale)
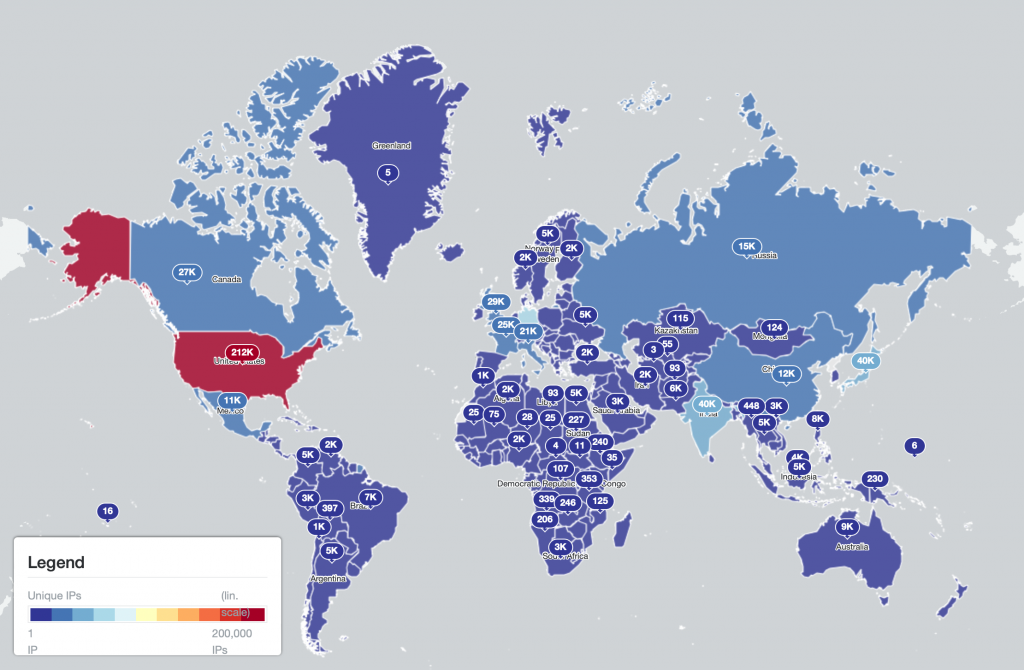 (Qakbot infections per country – logarithmic scale)
(Qakbot infections per country – logarithmic scale)
The IP-geolocated locations of each logged Qakbot infection (note that since there can be multiple bot infections behind a single IP address, these visualizations show unique geolocated IP addresses and may therefore under-represent the actual victim distribution globally):
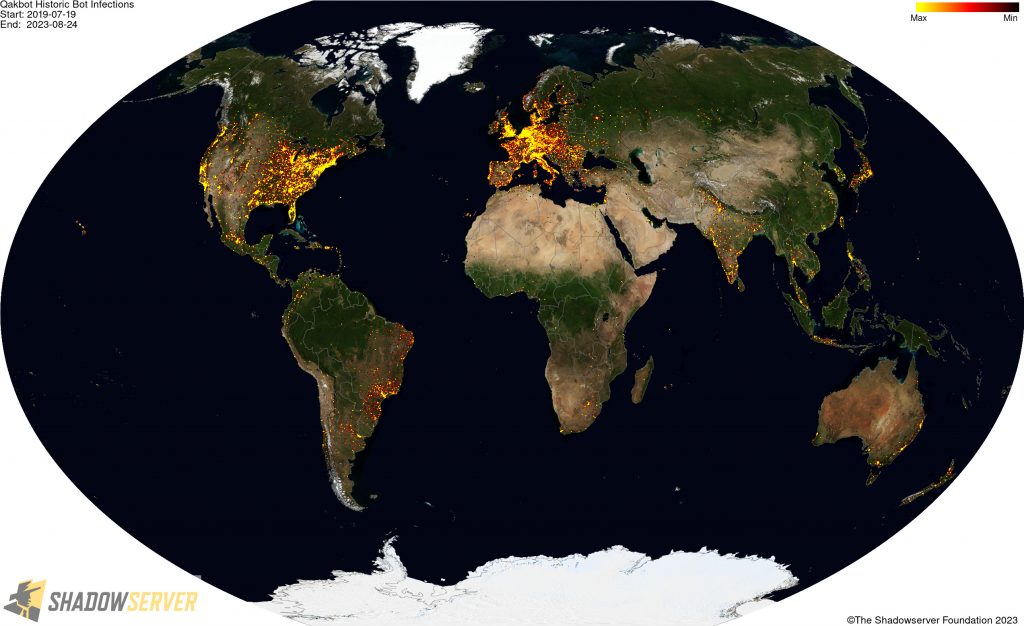 (IP-geolocated Qakbot infections – Worldwide)
(IP-geolocated Qakbot infections – Worldwide)
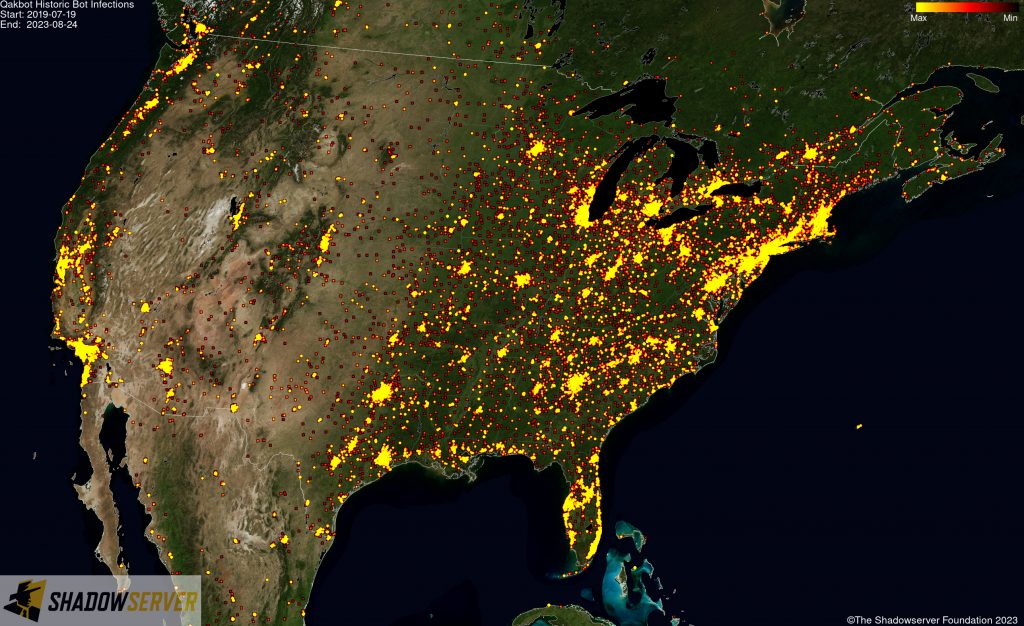 (IP-geolocated Qakbot infections – USA)
(IP-geolocated Qakbot infections – USA)
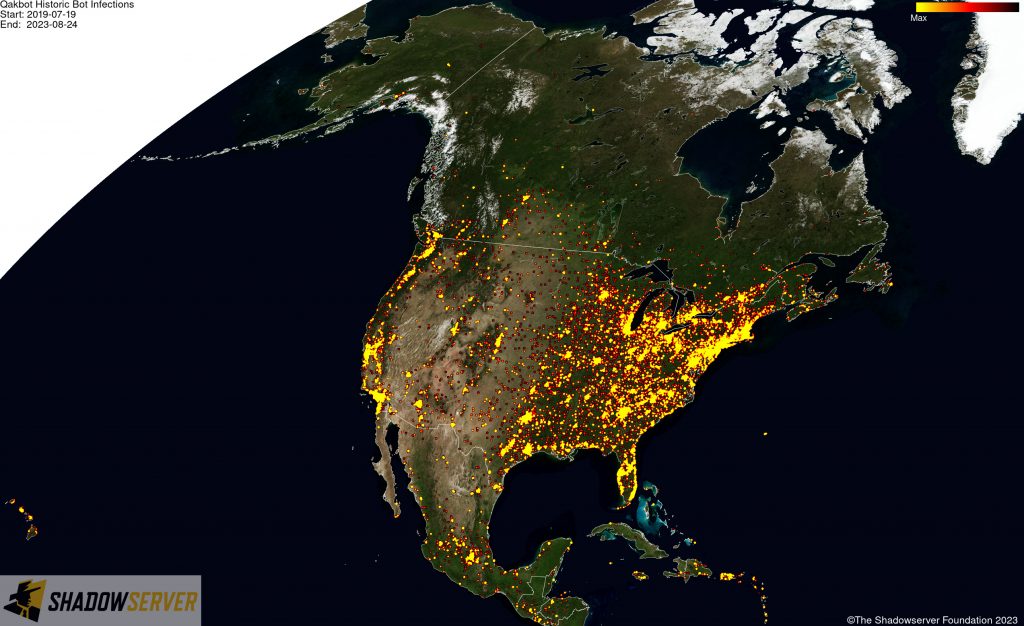 (IP-geolocated Qakbot infections – North America)
(IP-geolocated Qakbot infections – North America)
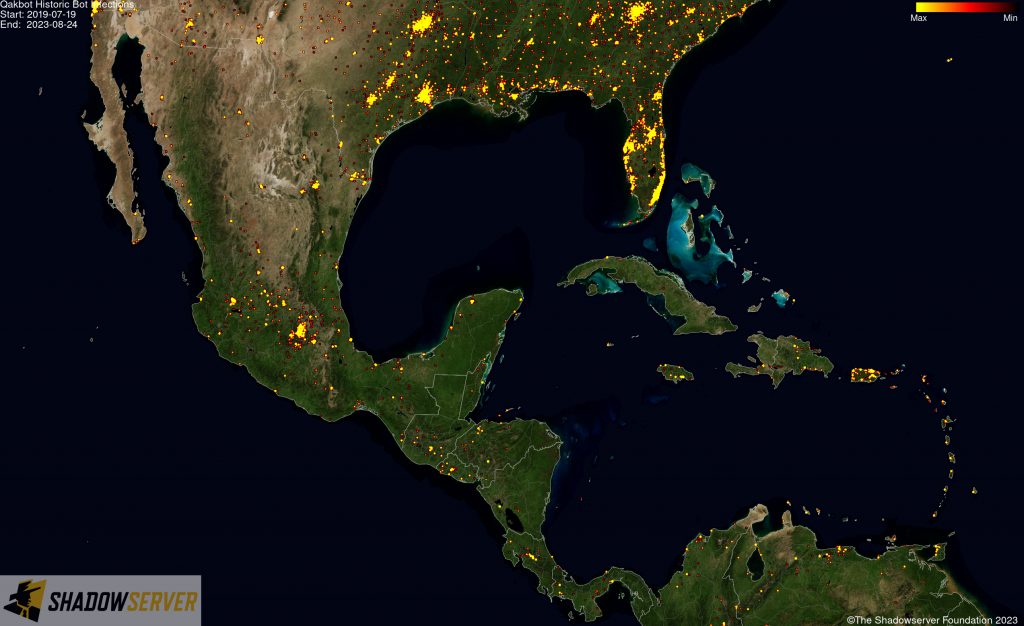 (IP-geolocated Qakbot infections – Central America)
(IP-geolocated Qakbot infections – Central America)
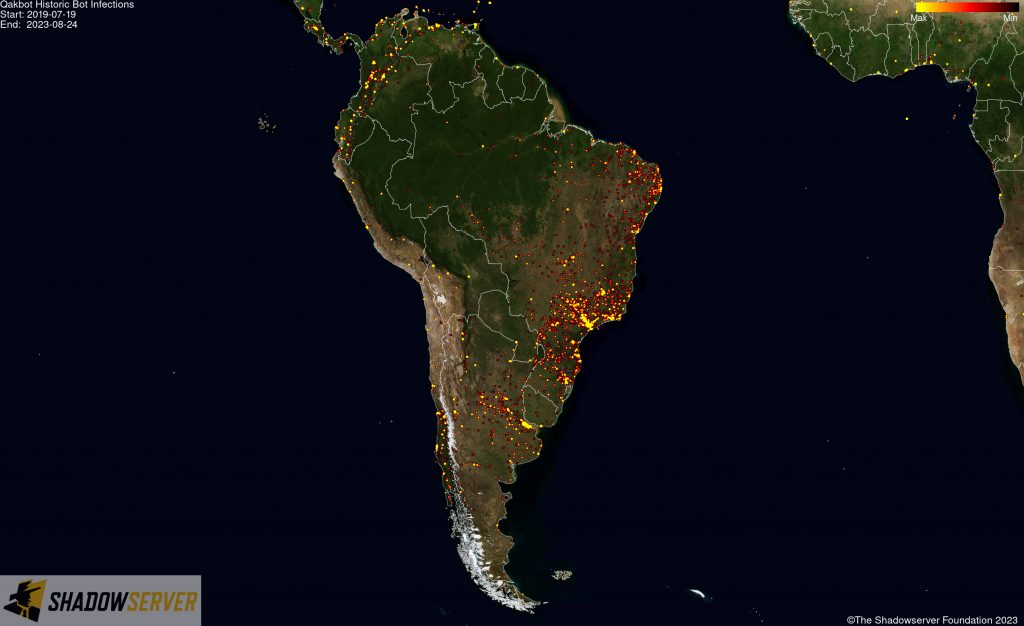 (IP-geolocated Qakbot infections – South America)
(IP-geolocated Qakbot infections – South America)
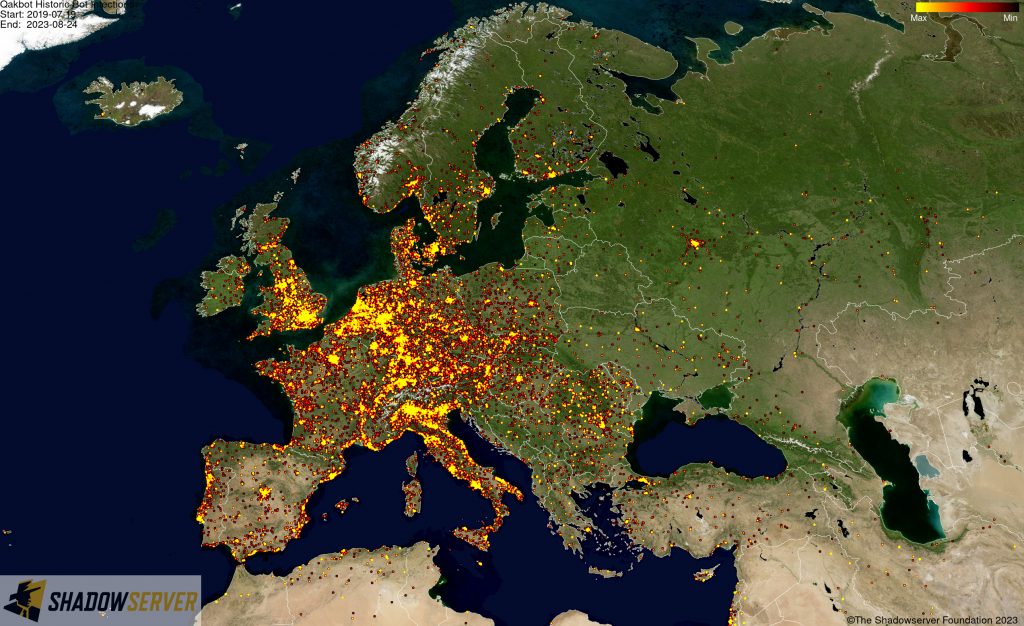 (IP-geolocated Qakbot infections – Europe)
(IP-geolocated Qakbot infections – Europe)
 (IP-geolocated Qakbot infections – UK/Europe)
(IP-geolocated Qakbot infections – UK/Europe)
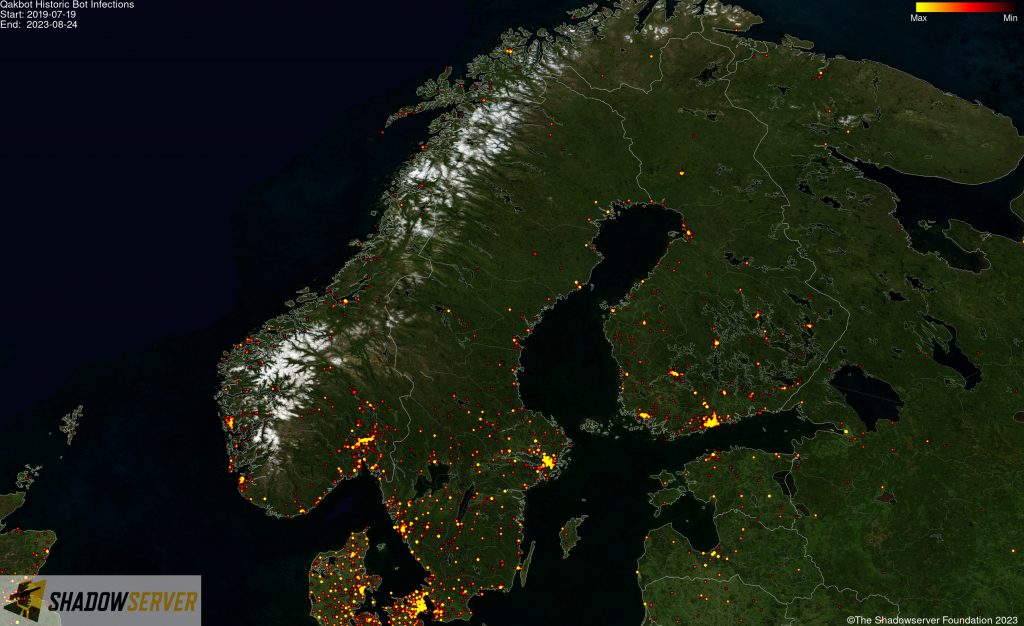 (IP-geolocated Qakbot infections – Scandinavia)
(IP-geolocated Qakbot infections – Scandinavia)
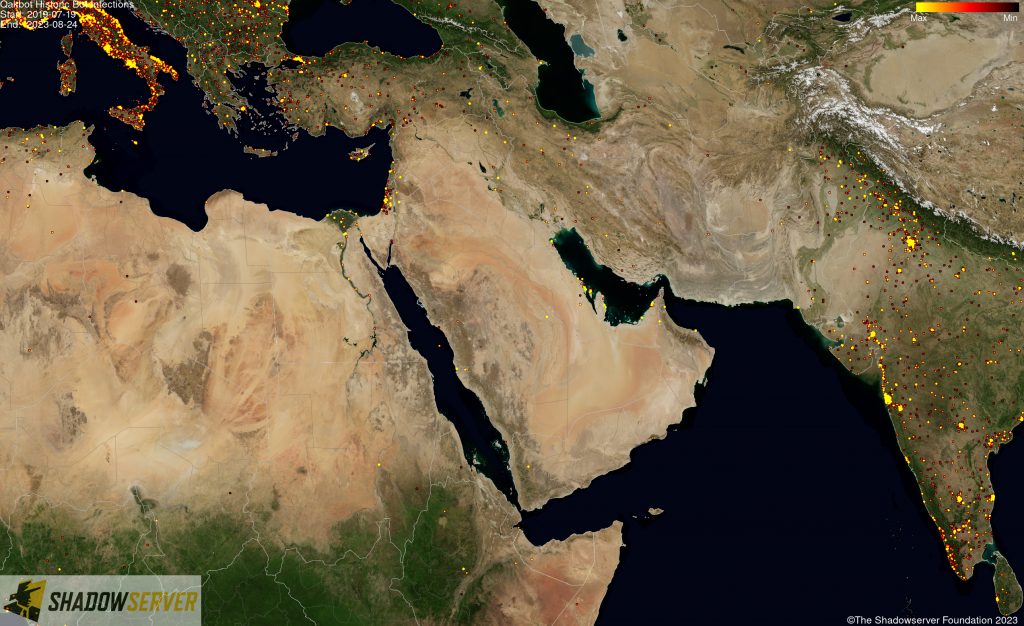 (IP-geolocated Qakbot infections – Middle East)
(IP-geolocated Qakbot infections – Middle East)
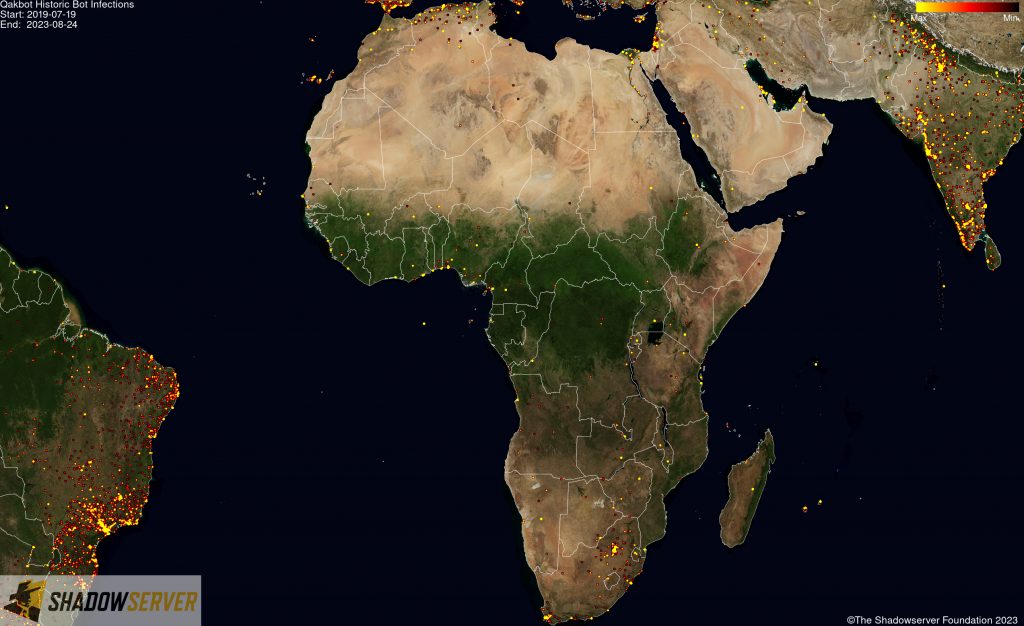 (IP-geolocated Qakbot infections – Africa)
(IP-geolocated Qakbot infections – Africa)
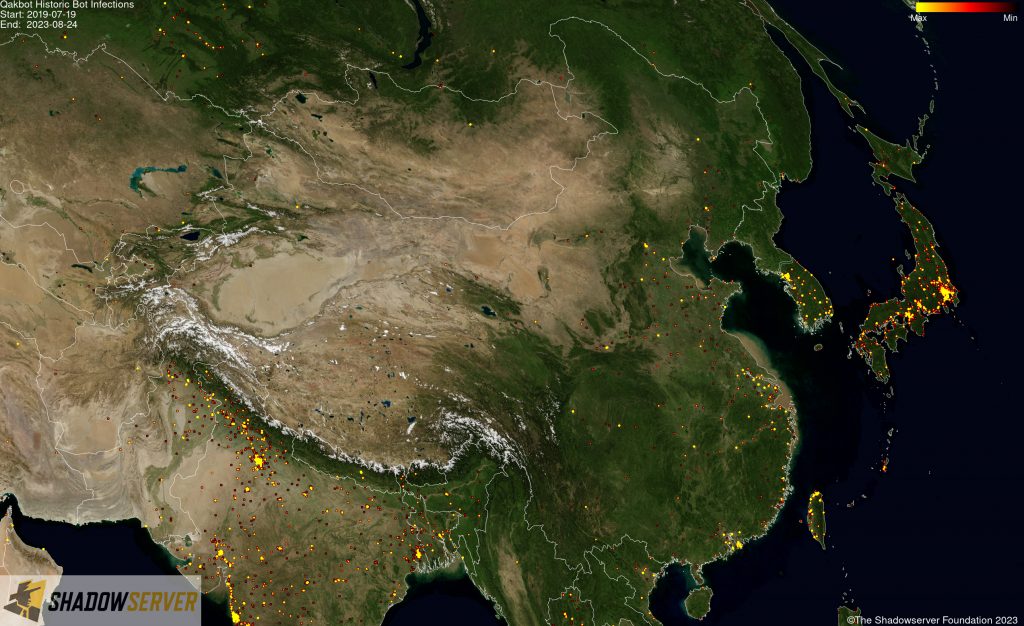 (IP-geolocated Qakbot infections – East Asia)
(IP-geolocated Qakbot infections – East Asia)
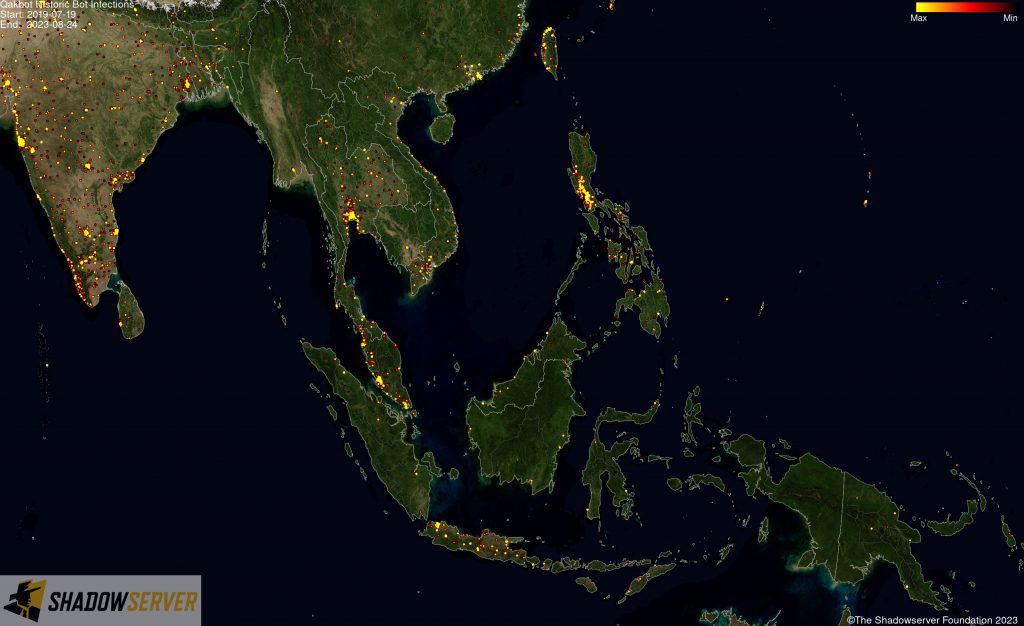 (IP-geolocated Qakbot infections – Oceania)
(IP-geolocated Qakbot infections – Oceania)
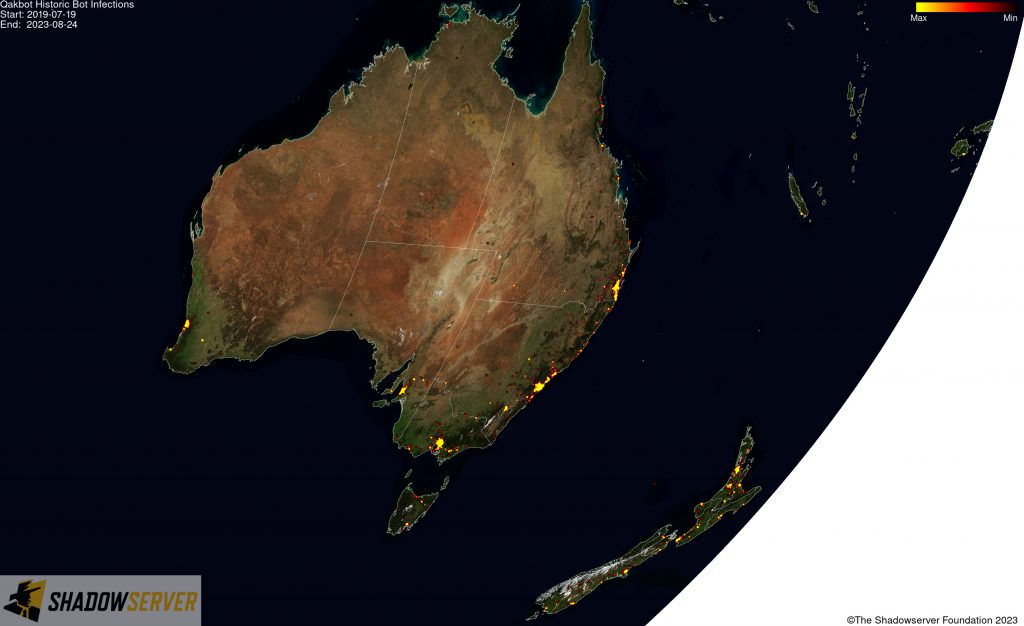 (IP-geolocated Qakbot infections – Australia/New Zealand)
(IP-geolocated Qakbot infections – Australia/New Zealand)
- Note that a small number (398) of IP addresses do not geolocate to a country, so the displayed number is slightly lower than the actual total:
 (Qakbot infections per country)
(Qakbot infections per country)
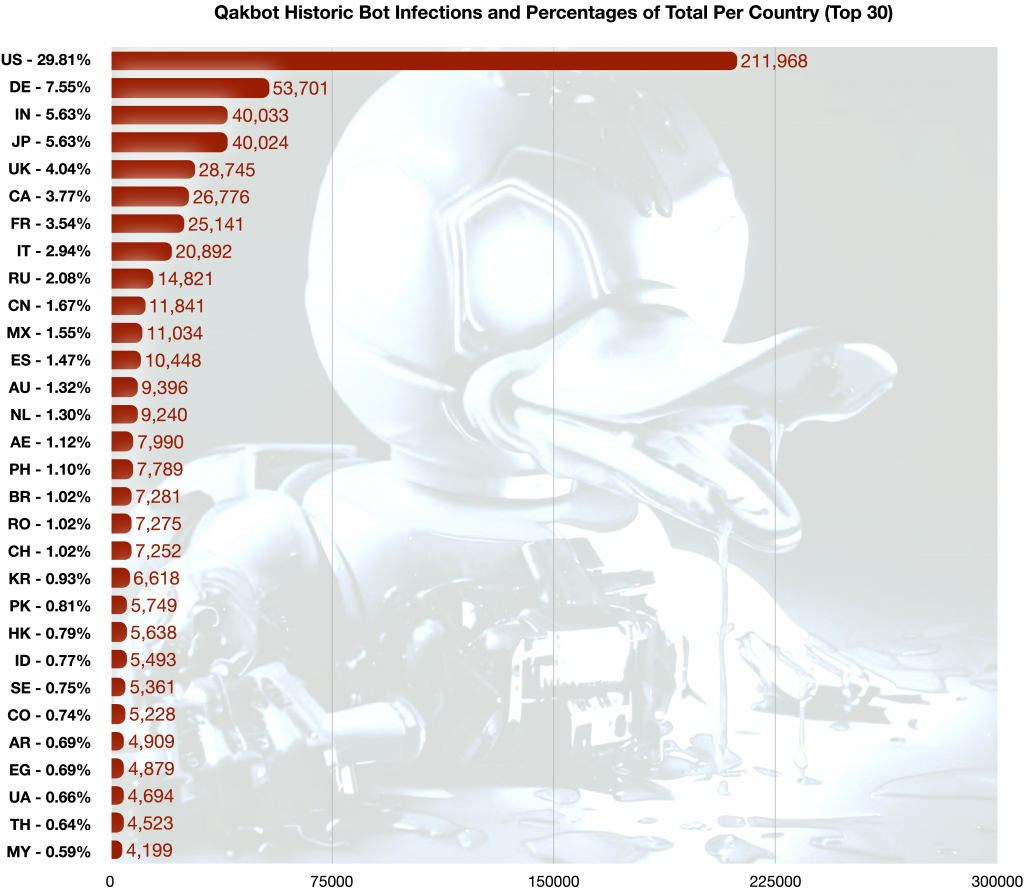
In chart form, the total number of Qakbot infections logged during the period July 2019 to August 2023, and the percentage of the total per country, was:
(Qakbot infections and percentage of total per country)
If you have any questions, please contact us, although there may be limitations on what information can be shared at this moment due to the ongoing LE investigations.
___________________________________________________________________________________
___________________________________________________________________________________









No comments:
Post a Comment