Cyber security experts studying memory modules in computers have uncovered a key weakness that has led to worldwide security fixes in AMD computer processors.
The weakness occurs because of "BadRAM"—rogue memory modules that deliberately provide false information to the computer's processor during startup.
The weakness occurs because of "BadRAM"—rogue memory modules that deliberately provide false information to the computer's processor during startup.
'BadRAM' exploit: Security flaw in computer memory leads to worldwide fixes

Processors are present in every computer and are necessary to perform every calculation. The computer's memory (DRAM) is essential for storing code and data. When a computer boots up, the processor will communicate with DRAM modules to learn size, speed and configuration.
This information is stored on the so-called SPD chip. But by tampering with this chip, the researchers found that attackers were able to bypass the AMD's security mechanisms put in place to protect sensitive data—particularly data stored in shared cloud environments with pervasive data breaches and insider threats.
In this case, the researchers targeted a security technology called Secure Encrypted Virtualization (SEV), designed by global computing company AMD. This cutting-edge technology protects privacy and trust in cloud computing by encrypting a virtual machine's memory and isolating it from advanced attackers.
In this case, the researchers targeted a security technology called Secure Encrypted Virtualization (SEV), designed by global computing company AMD. This cutting-edge technology protects privacy and trust in cloud computing by encrypting a virtual machine's memory and isolating it from advanced attackers.
- The research was carried out by a consortium of experts from KU Leuven, Belgium; the University of Luebeck, Germany; and the University of Birmingham, U.K.
Professor Oswald said, "We found that using cheap, off-the-shelf equipment, we were able to trick the computer's processor into allowing access to protected memory."
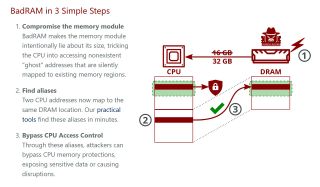
The researchers have published a website to explain the weakness and the potential threat posed. They explain that BadRAM makes the computer's memory module intentionally lie about its size, tricking the CPU into addressing "ghost" memory regions that don't exist.
This leads to two CPU addresses mapping to the same DRAM location. And through these aliases, attackers can bypass CPU memory protections, exposing sensitive data or causing disruptions.
This leads to two CPU addresses mapping to the same DRAM location. And through these aliases, attackers can bypass CPU memory protections, exposing sensitive data or causing disruptions.
Professor Oswald added,
"We worked with AMD to ensure they were able to adopt appropriate countermeasures so that BadRAM is detected at the point the computer boots up. While it's good practice to keep your system up-to-date, most cloud providers will have updated their firmware to include AMD's countermeasures—so there is no need to worry that your data is not secure!"
Provided by University of Birmingham
Explore further






No comments:
Post a Comment