Akira ransomware abuses CPU tuning tool to disable Microsoft Defender

- The abused driver is 'rwdrv.sys' (used by ThrottleStop), which the threat actors register as a service to gain kernel-level access.
- This driver is likely used to load a second driver, 'hlpdrv.sys,' a malicious tool that manipulates Windows Defender to turn off its protections.
This is a 'Bring Your Own Vulnerable Driver' (BYOVD) attack, where threat actors use legitimate signed drivers that have known vulnerabilities or weaknesses that can be abused to achieve privilege escalation. This driver is then used to load a malicious tool that disables Microsoft Defender.
"The second driver, hlpdrv.sys, is similarly registered as a service. When executed, it modifies the DisableAntiSpyware settings of Windows Defender within \REGISTRY\MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware," explain the researchers.
"The malware accomplishes this via execution of regedit.exe."
"We are flagging this behavior because of its ubiquity in recent Akira ransomware IR cases. This high-fidelity indicator can be used for proactive detection and retroactive threat hunting," continued the report.
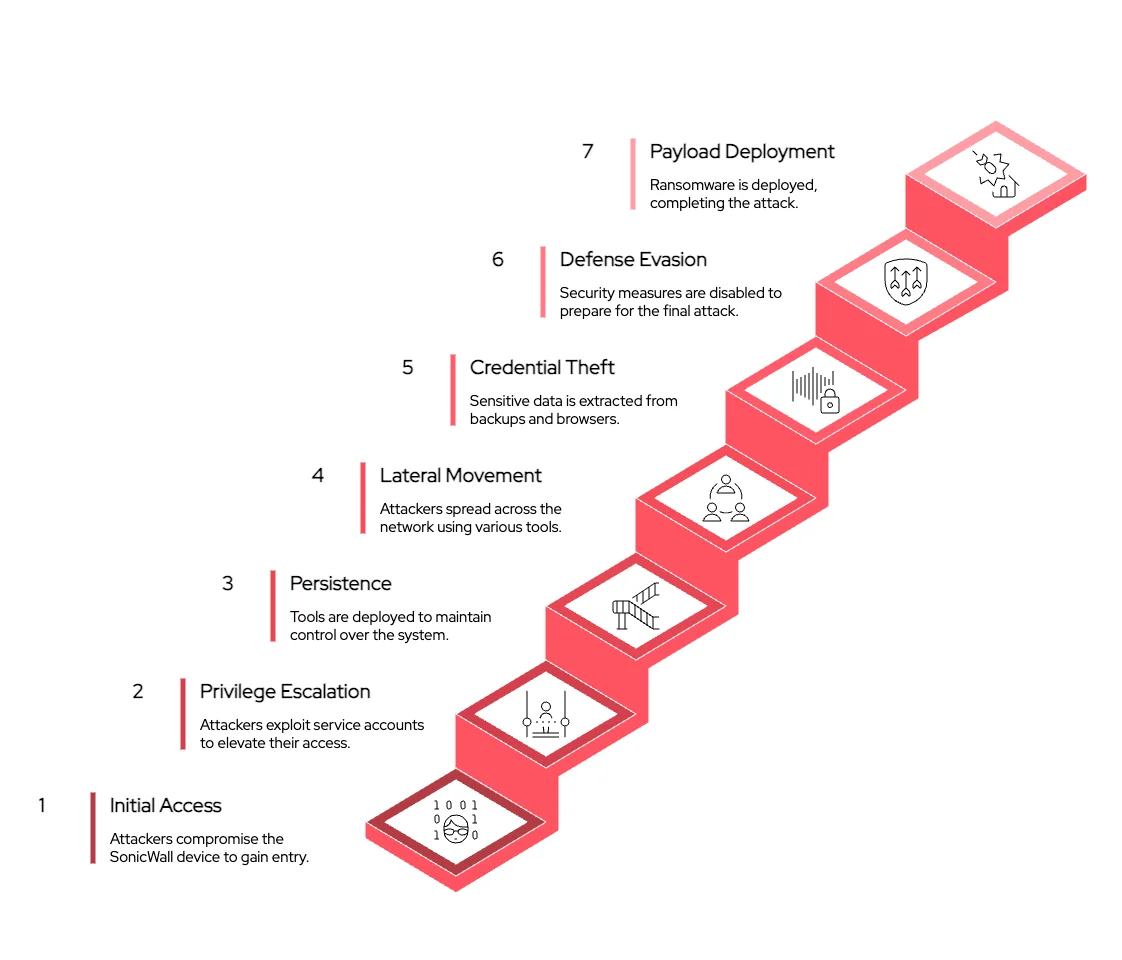
Akira attacks on SonicWall SSLVPN
Akira ransomware was recently linked to attacks on SonicWall VPNs using what is believed to be an unknown flaw.
- Guidepoint Security says it could neither confirm nor debunk the exploitation of a zero-day vulnerability in SonicWall VPNs by Akira ransomware operators.
- In response to reports about elevated offensive activity, SonicWall advised disabling or restricting SSLVPN, enforcing multi-factor authentication (MFA), enabling Botnet/Geo-IP protection, and removing unused accounts.
Meanwhile, The DFIR Report has published an analysis of recent Akira ransomware attacks, highlighting the use of the Bumblebee malware loader delivered via trojanized MSI installers of IT software tools.
An example involves searches for "ManageEngine OpManager" on Bing, where SEO poisoning redirected the victim to the malicious site opmanager[.]pro.
.jpg)
Source: The DFIR Report
Bumblebee is launched via DLL sideloading, and once C2 communication is established, it drops AdaptixC2 for persistent access.The attackers then conduct internal reconnaissance, create privileged accounts, and exfiltrate data using FileZilla, while maintaining access via RustDesk and SSH tunnels.
After approximately 44 hours, the main Akira ransomware payload (locker.exe) is deployed to encrypt systems across domains.
New Ghost Calls tactic abuses Zoom and Microsoft Teams for C2 operations
A new post-exploitation command-and-control (C2) evasion method called 'Ghost Calls' abuses TURN servers used by conferencing apps like Zoom and Microsoft Teams to tunnel traffic through trusted infrastructure.
- August 06, 2025
- 12:36 PM
 0
0
Hacker extradited to US for stealing $3.3 million from taxpayers
Nigerian national Chukwuemeka Victor Amachukwu has been extradited from France to the U.S. to face charges of hacking, fraud, and identity theft for suspected spearphishing attacks on U.S. tax preparation businesses.
- August 06, 2025
- 12:09 PM
 0
0
Google suffers data breach in ongoing Salesforce data theft attacks
Google is the latest company to suffer a data breach in an ongoing wave of Salesforce CRM data theft attacks conducted by the ShinyHunters extortion group.
- August 06, 2025
- 09:51 AM
 0
0
National Bank of Canada online systems down due to 'technical issue'
National Bank of Canada (Banque Nationale du Canada), the sixth largest commercial bank of Canada is currently experiencing a widespread service outage affecting its online banking and mobile app platforms.
- August 06, 2025
- 09:19 AM
 0
0
ReVault flaws let hackers bypass Windows login on Dell laptops
ControlVault3 firmware vulnerabilities impacting over 100 Dell laptop models can allow attackers to bypass Windows login and install malware that persists across system reinstalls.
- August 06, 2025
- 07:58 AM
 0
0







No comments:
Post a Comment