American cybersecurity firm CrowdStrike has confirmed that an insider shared screenshots taken on internal systems with hackers after they were leaked on Telegram by the Scattered Lapsus$ Hunters threat actors.
However, the company noted that its systems were not breached as a result of this incident and that customers' data was not compromised.
CrowdStrike catches insider feeding information to hackers

Update November 21, 12:04 EST: Story updated with information from hackers.
[. . .] "We identified and terminated a suspicious insider last month following an internal investigation that determined he shared pictures of his computer screen externally," a CrowdStrike spokesperson told BleepingComputer today.
"Our systems were never compromised and customers remained protected throughout. We have turned the case over to relevant law enforcement agencies."
- However, this statement was provided in response to questions from BleepingComputer regarding screenshots of CrowdStrike systems that were recently posted on Telegram by members of the threat groups ShinyHunters, Scattered Spider, and Lapsus$.
ShinyHunters told BleepingComputer earlier today that they allegedly agreed to pay the insider $25,000 to provide them with access to CrowdStrike's network.
The threat actors claimed they ultimately received SSO authentication cookies from the insider, but by then, the suspected insider had already been detected by CrowdStrike, which had shut down his network access.
The extortion group added that they also attempted to purchase CrowdStrike reports on ShinyHunters and Scattered Spider, but did not receive them.
BleepingComputer contacted CrowdStrike again to confirm if this information is accurate and will update the story if we receive additional information.
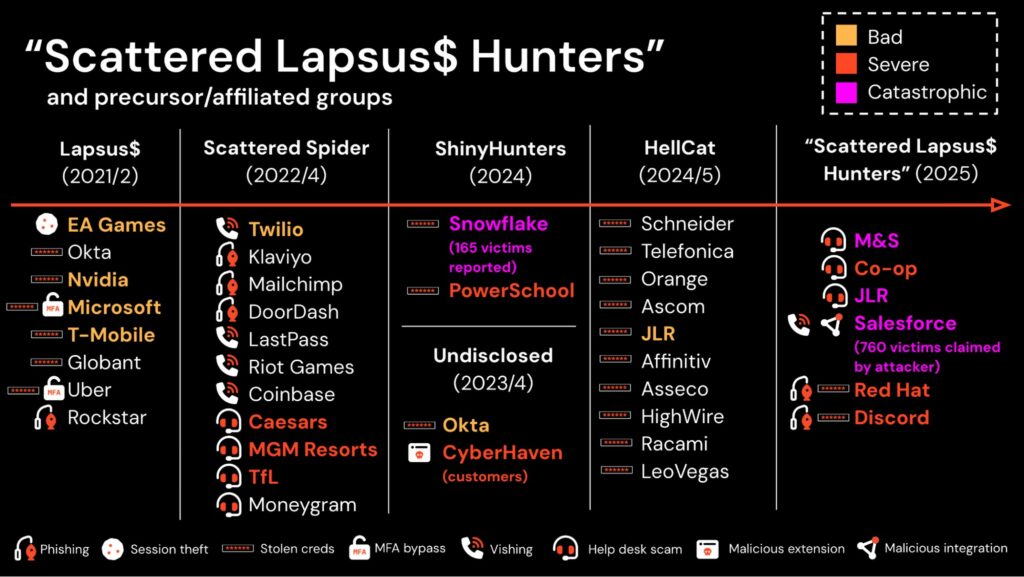
The Scattered Lapsus$ Hunters cybercrime collective
These groups, now collectively calling themselves "Scattered Lapsus$ Hunters," have previously launched a data-leak site to extort dozens of companies impacted by a massive wave of Salesforce breaches.
- Google,
- Cisco,
- Allianz Life,
- Farmers Insurance,
- Qantas,
- Adidas,
- Workday, as well as LVMH subsidiaries, including Dior, Louis Vuitton, and Tiffany & Co.
- Google,
- Cisco,
- Toyota,
- Instacart,
- Cartier,
- Adidas,
- Sake Fifth Avenue,
- Air France & KLM,
- FedEx, Disney/Hulu,
- Home Depot, Marriott,
- Gap,
- Walgreen's,
- Transunion,
- HBO MAX,
- UPS,
- Chanel, and IKEA.
Scattered Lapsus$ Hunters also claimed responsibility for the Jaguar Land Rover (JLR) breach, stealing sensitive data and significantly disrupting operations, resulting in damages of over £196 million ($220 million) in the last quarter.
As BleepingComputer reported this week, the ShinyHunters and Scattered Spider extortion groups are switching to a new ransomware-as-a-service platform named ShinySp1d3r, after previously using other ransomware gangs' encryptors in attacks, including ALPHV/BlackCat, RansomHub, Qilin, and DragonForce.
- LinkedIn,
- GitLab,
- Atlassian,
- Thomson Reuters,
- Verizon,
- F5,
- SonicWall,
- DocuSign, and
- Malwarebytes.
As the threat actors told BleepingComputer yesterday, they compromised the Salesforce instances after breaching Gainsight using secrets stolen in the Salesloft drift breach.
-
WhatsApp API flaw let researchers scrape 3.5 billion accounts
Researchers compiled a list of 3.5 billion WhatsApp mobile phone numbers and associated personal information by abusing a contact-discovery API that lacked rate limiting.
- November 22, 2025
- 01:53 PM
 1
1
-
Cox Enterprises discloses Oracle E-Business Suite data breach
Cox Enterprises is notifying impacted individuals of a data breach that exposed their personal data to hackers who breached the company network after exploiting a zero-day flaw in Oracle E-Business Suite.
- November 22, 2025
- 10:16 AM
 0
0
-
New Webinar: How phishing attacks evolved in 2025

This year, we've seen a huge amount of phishing evolution, with new techniques, toolkits, and delivery methods identified every day.
Register for the webinar to get the latest insights from Push Security analysing key stats, getting hands-on with phishing kits, and sharing case studies from the field.
-
Piecing Together the Puzzle: A Qilin Ransomware Investigation
Huntress analysts reconstructed a Qilin ransomware attack from a single endpoint, using limited logs to reveal rogue ScreenConnect access, failed infostealer attempts, and the ransomware execution path. The investigation shows how validating multiple data sources can uncover activity even when visibility is reduced to a "pinhole."
- November 22, 2025
- 08:45 AM
 0
0
-
This like-new refurbished Surface Laptop 3 is just $379.99 right now
If your current laptop is starting to show signs of aging every time you open a browser tab, this like-new refurbished Microsoft Surface Laptop 3 is absolutely worth a look while it's just $379.99 (MSRP $1,099) with free shipping.
- November 22, 2025
- 08:12 AM
 0
0
-
CISA warns Oracle Identity Manager RCE flaw is being actively exploited
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning government agencies to patch an Oracle Identity Manager tracked as CVE-2025-61757 that has been exploited in attacks, potentially as a zero-day.
- November 21, 2025
- 06:50 PM
 0
0
-
Nvidia confirms October Windows updates cause gaming issues
Nvidia has confirmed that last month's security updates are causing gaming performance issues on Windows 11 24H2 and Windows 11 25H2 systems.
- November 21, 2025
- 02:57 PM
 0
0
-
Microsoft: Out-of-band update fixes Windows 11 hotpatch install loop
Microsoft has released an out-of-band cumulative update to fix a known issue causing the November 2025 KB5068966 hotpatch update to reinstall on Windows 11 systems repeatedly.
- November 21, 2025
- 01:02 PM
 0
0
-
Grafana warns of max severity admin spoofing vulnerability
Grafana Labs is warning of a maximum severity vulnerability (CVE-2025-41115) in its Enterprise product that can be exploited to treat new users as administrators or for privilege escalation.
- November 21, 2025
- 12:58 PM
 0
0











No comments:
Post a Comment