Emotet now drops Cobalt Strike, fast forwards ransomware attacks
In a concerning development, the notorious Emotet malware now installs Cobalt Strike beacons directly, giving immediate network access to threat actors and making ransomware attacks imminent.
Emotet is a malware infection that spreads through spam emails containing malicious Word or Excel documents. These documents utilize macros to download and install the Emotet Trojan on a victim's computer, which is then used to steal email and deploy further malware on the device.
Historically, Emotet would install the TrickBot or Qbot trojans on infected devices. These Trojans would eventually deploy Cobalt Strike on an infected device or perform other malicious behavior.
Cobalt Strike is a legitimate penetration testing toolkit that allows attackers to deploy "beacons" on compromised devices to perform remote network surveillance or execute further commands.
However, Cobalt Strike is very popular among threat actors who use cracked versions as part of their network breaches and is commonly used in ransomware attacks.
Emotet changes its tactics
Today, Emotet research group Cryptolaemus warned that Emotet is now skipping their primary malware payload of TrickBot or Qbot and directly installing Cobalt Strike beacons on infected devices.
WARNING We have confirmed that #Emotet is dropping CS Beacons on E5 Bots and we have observed the following as of 10:00EST/15:00UTC. The following beacon was dropped: https://t.co/imJDQTGqxV Note the traffic to lartmana[.]com. This is an active CS Teams Server. 1/x
— Cryptolaemus (@Cryptolaemus1) December 7, 2021
A Flash Alert shared with BleepingComputer by email security firm Cofense explained that a limited number of Emotet infections installed Cobalt Strike, attempted to contact a remote domain, and then was uninstalled. . ." READ MORE
27 flaws in USB-over-network SDK affect millions of cloud users

December 7, 2021 10:15 AM
Due to the pandemic and the rising trend of working from home, organizations have begun to rely heavily on cloud-based services. This necessity also increased cloud providers utilizing Eltima's SDK that allow employees to mount local USB mass storage devices for use on their cloud-based virtual desktops.
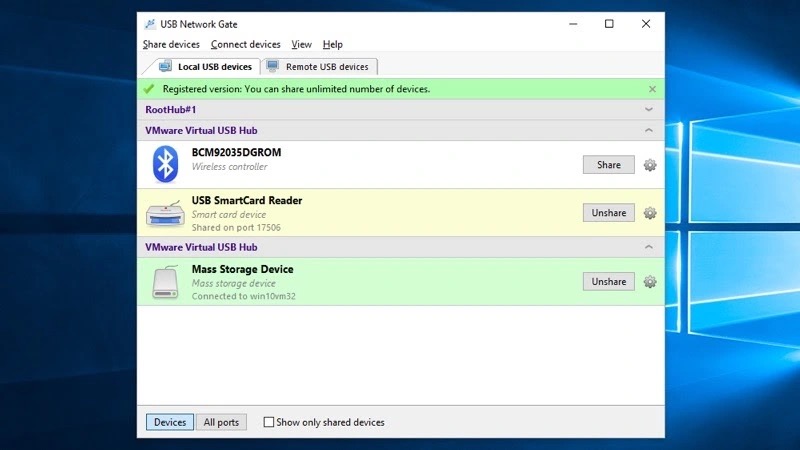
Source: Eltima
However, as cloud desktop providers, including Amazon Workspaces, rely on tools like Eltima, SentinelOne warned that millions of users worldwide have become exposed to the discovered vulnerabilities.
The implications of exploiting the flaws are significant as they could allow remote threat actors to gain elevated access on a cloud desktop to run code in kernel mode.
"These vulnerabilities allow attackers to escalate privileges enabling them to disable security products, overwrite system components, corrupt the operating system, or perform malicious operations unimpeded," explained a new report by Sentinel Labs.
This elevated access could allow malware to steal credentials that threat actors can use to breach an organization's internal network.
In total, there are 27 vulnerabilities discovered by SentinelOne, with the CVE IDs listed below:
CVE-2021-42972, CVE-2021-42973, CVE-2021-42976, CVE-2021-42977, CVE-2021-42979, CVE-2021-42980, CVE-2021-42983, CVE-2021-42986, CVE-2021-42987, CVE-2021-42988, CVE-2021-42990, CVE-2021-42993, CVE-2021-42994, CVE-2021-42996, CVE-2021-43000, CVE-2021-43002, CVE-2021-43003, CVE-2021-43006, CVE-2021-43637, CVE-2021-43638, CVE-2021-42681, CVE-2021-42682, CVE-2021-42683, CVE-2021-42685, CVE-2021-42686, CVE-2021-42687, CVE-2021-42688These vulnerabilities have been responsibly disclosed to Eltima, who has already released fixes for affected versions. However, it is now up to cloud services to upgrade their software to utilize the updated Eltima SDK.
According to SentinelOne, the affected software and cloud platforms are:
- Amazon Nimble Studio AMI, before 2021/07/29
- Amazon NICE DCV, below: 2021.1.7744 (Windows), 2021.1.3560 (Linux), 2021.1.3590 (Mac), 2021/07/30
- Amazon WorkSpaces agent, below: v1.0.1.1537, 2021/07/31
- Amazon AppStream client version below: 1.1.304, 2021/08/02
- NoMachine [all products for Windows], above v4.0.346 below v.7.7.4 (v.6.x is being updated as well)
- Accops HyWorks Client for Windows: version v3.2.8.180 or older
- Accops HyWorks DVM Tools for Windows: version 3.3.1.102 or lower (Part of Accops HyWorks product earlier than v3.3 R3)
- Eltima USB Network Gate below 9.2.2420 above 7.0.1370
- Amzetta zPortal Windows zClient
- Amzetta zPortal DVM Tools
- FlexiHub below 5.2.14094 (latest) above 3.3.11481
- Donglify below 1.7.14110 (latest) above 1.0.12309
It is important to note that Sentinel Labs hasn’t looked into all possible products that could incorporate the vulnerable Eltima SDK, so there could be more products affected by the set of flaws.
Also, some services are vulnerable on the client-side, others on the server-side, and a few on both, depending on code-sharing policies
-
Emotet now drops Cobalt Strike, fast forwards ransomware attacks
In a concerning development, the notorious Emotet malware now installs Cobalt Strike beacons directly, giving immediate network access to threat actors and making ransomware attacks imminent.
- December 07, 2021
- 06:21 PM
 0
0
-
Grafana fixes zero-day vulnerability after exploits spread over Twitter
Open-source analytics and interactive visualization solution Grafana received an emergency update today to fix a high-severity, zero-day vulnerability that enabled remote access to local files.
- December 07, 2021
- 05:46 PM
 1
1
-
AWS outage impacts Ring, Netflix, and Amazon deliveries
Amazon AWS in the US-EAST-1 Region is suffering an outage that affected numerous online services, including Ring, Netflix, and Amazon Prime Video, and Roku.
- December 07, 2021
- 04:28 PM
 0
0
-
Alleged ransomware affiliate arrested for healthcare attacks
A 31-year old Canadian national has been charged in connection to ransomware attacks against organizations in the United States and Canada, a federal indictment unsealed today shows.
- December 07, 2021
- 03:37 PM
 0
0
-
US universities targeted by Office 365 phishing attacks
US universities are being targeted in multiple phishing attacks designed to impersonate college login portals to steal valuable Office 365 credentials.
- December 07, 2021
- 03:23 PM
 0
0
-
Become a Windows 11 power user in 5½ hours with this $20 course
The Essential Windows 11 Course provides an easy way to learn your way around, with 5½ hours of video tutorials. It's normally priced at $75, but you can get it today for only $19.99,
- December 07, 2021
- 02:55 PM
 0
0
-
Microsoft starts rolling out redesigned Notepad for Windows 11
Microsoft has started rolling out the new and completely redesigned Notepad for Windows 11 to all Windows Insiders in the Dev Channel.
- December 07, 2021
- 02:22 PM
 0
0
-
New Cerber ransomware targets Confluence and GitLab servers
Cerber ransomware is back, as a new ransomware family adopts the old name and targets Atlassian Confluence and GitLab servers using remote code execution vulnerabilities.
- December 07, 2021
- 01:19 PM
 0
0
-
Google disrupts massive Glupteba botnet, sues Russian operators
Google announced today that it has taken action to disrupt the Glupteba botnet that now controls more than 1 million Windows PCs around the world, growing by thousands of new infected devices each day.
- December 07, 2021
- 11:57 AM
 0
0
-
27 flaws in USB-over-network SDK affect millions of cloud users
Researchers have discovered 27 vulnerabilities in Eltima SDK, a library used by numerous cloud providers to remotely mount a local USB device.
- December 07, 2021
- 10:15 AM
 0
0
-
STOP Ransomware vaccine released to block encryption
German security software company G DATA has released a vaccine that will block STOP Ransomware from encrypting victims' files after infection.
- December 07, 2021
- 10:06 AM
 3
3
-
QNAP warns users of bitcoin miner targeting their NAS devices
QNAP warned customers today of ongoing attacks targeting their NAS (network-attached storage) devices with cryptomining malware, urging them to take measures to protect them immediately.
- December 07, 2021
- 08:53 AM
 0
0
-
Twitter bots pose as support staff to steal your cryptocurrency
Scammers monitor every tweet containing requests for support on MetaMask, TrustWallet, and other popular crypto wallets, and respond to them with scam links in just seconds.
- December 07, 2021
- 04:04 AM
 1
1
-
Nordic Choice Hotels hit by Conti ransomware, no ransom demand yet
Nordic Choice Hotels has now confirmed a cyber attack on its systems from the Conti ransomware group. Although there is no indication of card or payment information being affected, information pertaining to guest bookings was potentially leaked.
- December 07, 2021
- 02:39 AM
 0
0













No comments:
Post a Comment