Looks like that is a SIGN OF OUR TIME
New stealthy DarkWatchman malware hides in the Windows Registry
A new malware named 'DarkWatchman' has emerged in the cybercrime underground, and it's a lightweight and highly-capable JavaScript RAT (Remote Access Trojan) paired with a C# keylogger.
According to a technical report by researchers at Prevailion, the novel RAT is employed by Russian-speaking actors who target mainly Russian organizations.
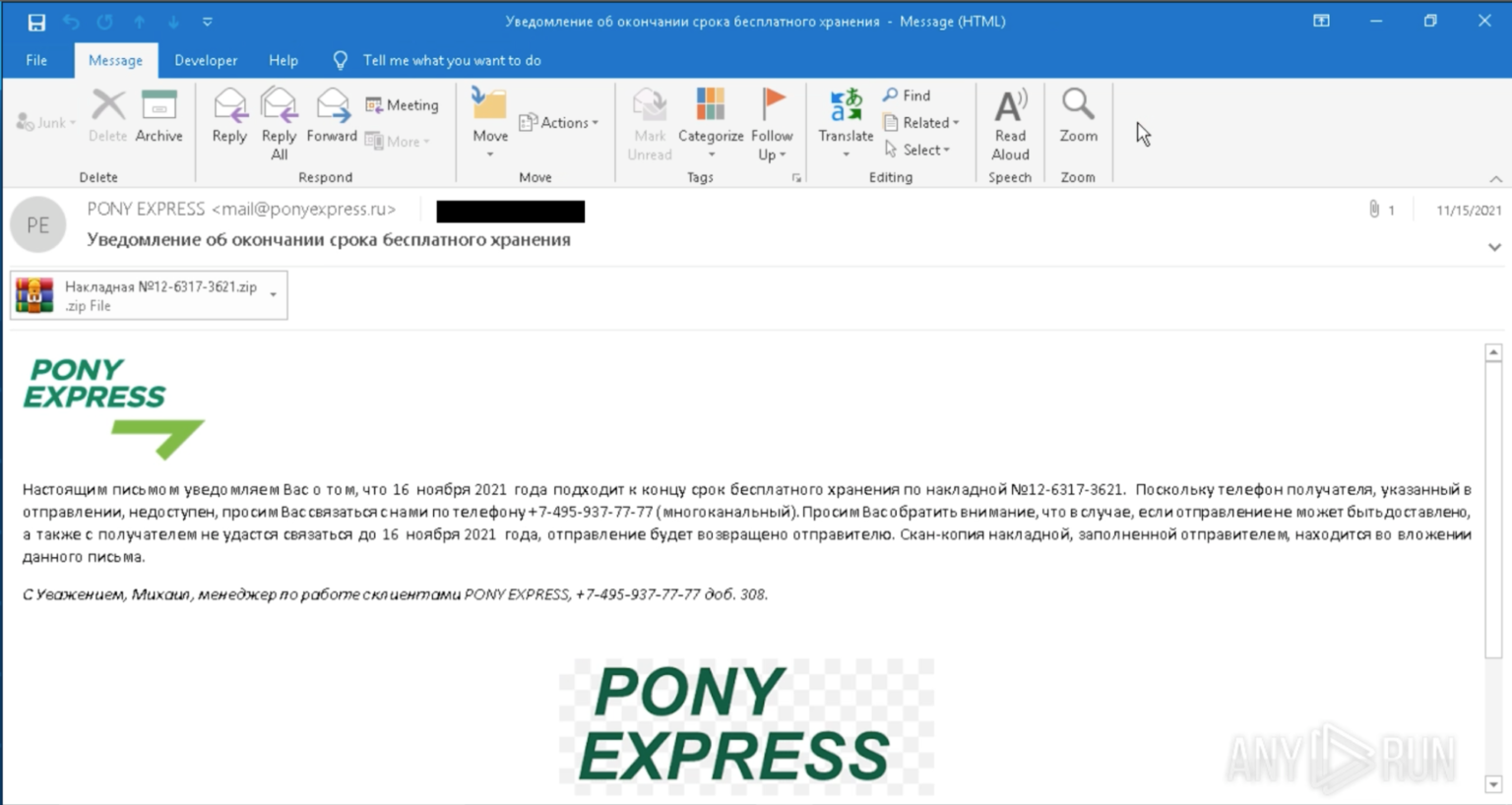
The first signs of DarkWatchman's existence appeared in early November as the threat actor began distributing the malware through phishing emails with malicious ZIP attachments.
.png)
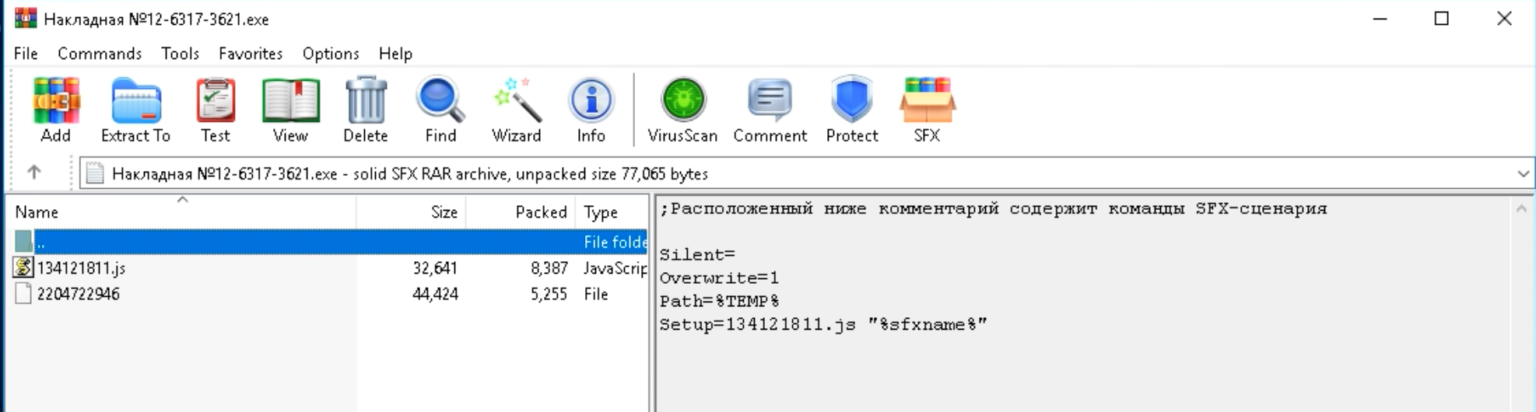
These ZIP file attachments contain an executable using an icon to impersonate a text document. This executable is a self-installing WinRAR archive that will install the RAT and keylogger.
If opened, the user is shown a decoy popup message that reads "Unknown Format," but in reality, the payloads have been installed in the background.
A stealthy 'file-less' RAT
DarkWatchman is a very light malware, with the JavaScript RAT measuring just 32kb in size and the compiled only taking using 8.5kb of space.
It utilizes a large set of "living off the land" binaries, scripts, and libraries, and incorporates stealthy methods to transfer data between modules.
The fascinating aspect of DarkWatchman is its use of the Windows Registry fileless storage mechanism for the keylogger.
Instead of storing the keylogger on disk, a scheduled task is created to launch the DarkWatchman RAT every time the user logs into Windows.
Once launched, DarkWatchmen will execute a PowerShell script that compiles the keylogger using the .NET CSC.exe command and launches it into memory . . .
[...] DarkWatchman’s functional capabilities are the following:
- Execute EXE files (with or without the output returned)
- Load DLL files
- Execute commands on the command line
- Execute WSH commands
- Execute miscellaneous commands via WMI
- Execute PowerShell commands
- Evaluate JavaScript
- Upload files to the C2 server from the victim machine
- Remotely stop and uninstall the RAT and Keylogger
- Remotely update the C2 server address or call-home timeout
- Update the RAT and Keylogger remotely
- Set an autostart JavaScript to run on RAT startup
- A Domain Generation Algorithm (DGA) for C2 resiliency
- If the user has admin permissions, it deletes shadow copies using vssadmin.exe
The ransomware hypothesis
Prevailion theorizes that DarkWatchman may be tailored by/for ransomware groups that need to empower their less capable affiliates with a potent and stealthy tool.
The malware can load additional payloads remotely, so it could be used as a stealthy first-stage infection for subsequent ransomware deployment.
Since DarkWatchman can communicate to actor-controlled domains after the initial foothold, the ransomware operator could take over and deploy the ransomware or handle the file exfiltration directly.
This approach would degrade the affiliate's role to that of a network infiltrator and simultaneously make RaaS operations more clinical and efficient.
-
Fix your home Wi-Fi with this 4.3 Gbps mesh router, now just $245
The Gryphon AX WiFi Router takes advantage of the mesh approach. This powerful device delivers up to 4.3 Gbps on its own, and you can pair two together for even better coverage. Right now, it's 12% off MSRP at just $245.
- December 20, 2021
- 03:46 PM
 0
0
-
Microsoft warns of easy Windows domain takeover via Active Directory bugs
Microsoft warned customers today to patch two Active Directory domain service privilege escalation security flaws that, when combined, allow attackers to easily takeover Windows domains.
- December 20, 2021
- 02:51 PM
 3
3
-
Meta sues people behind Facebook and Instagram phishing
Meta (formerly known as Facebook) has filed a federal lawsuit in California court to disrupt phishing attacks targeting Facebook, Messenger, Instagram, and WhatsApp users.
- December 20, 2021
- 01:37 PM
 1
1
-
FBI: State hackers exploiting new Zoho zero-day since October
The Federal Bureau of Investigation (FBI) says a zero-day vulnerability in Zoho's ManageEngine Desktop Central has been under active exploitation by state-backed hacking groups (also known as APTs or advanced persistent threats) since at least October.
- December 20, 2021
- 01:06 PM
 0
0
-
UK govt shares 585 million passwords with Have I Been Pwned
The United Kingdom's National Crime Agency has contributed more than 585 million passwords to the Have I Been Pwned service that lets users check if their login information has leaked online.
- December 20, 2021
- 12:49 PM
 0
0
-
Log4j vulnerability now used to install Dridex banking malware
Threat actors now exploit the critical Apache Log4j vulnerability named Log4Shell to infect vulnerable devices with the notorious Dridex banking trojan or Meterpreter.
- December 20, 2021
- 11:33 AM
 0
0
-
T-Mobile says it blocked 21 billion scam calls this year
T-Mobile says it blocked 21 billion scam, spam, and unwanted robocalls this year through its free Scam Shield robocall and scam protection service, amounting to an average of 1.8 billion scam calls identified or blocked every month.
- December 20, 2021
- 10:46 AM
 0
0
-
This $40 bundle can help get you started in cybersecurity
The 2022 Masters in Cyber Security Certification Bundle helps you build the required résumé, with nine courses covering all the fundamentals. The included training is worth $1,800, but you can get it today for only $39.99.
- December 20, 2021
- 07:16 AM
 0
0
-
Phishing attacks impersonate Pfizer in fake requests for quotation
Threat actors are conducting a highly targeted phishing campaign impersonating Pfizer to steal business and financial information from victims.
- December 20, 2021
- 06:00 AM
 0
0











No comments:
Post a Comment