Backdoor gives hackers complete control over federal agency network
Avast researchers say the malware has ties to a previously seen espionage hack.

"A US federal agency has been hosting a backdoor that can provide total visibility into and complete control over the agency network, and the researchers who discovered it have been unable to engage with the administrators responsible, security firm Avast said on Thursday.
The US Commission on International Religious Freedom, associated with international rights, regularly communicates with other US agencies and international governmental and nongovernmental organizations. The security firm published a blog post after multiple attempts failed to report the findings directly and through channels the US government has in place. The post didn't name the agency, but a spokeswoman did in an email. Representatives from the commission didn't respond to an email seeking comment.
Members of Avast’s threat intelligence team wrote:
While we have no information on the impact of this attack or the actions taken by the attackers, based on our analysis of the files in question, we believe it’s reasonable to conclude that the attackers were able to intercept and possibly exfiltrate all local network traffic in this organization. This could include information exchanged with other US government agencies and other international governmental and nongovernmental organizations (NGOs) focused on international rights. We also have indications that the attackers could run code of their choosing in the operating system’s context on infected systems, giving them complete control.
Bypassing firewalls and network monitoring
The backdoor works by replacing a normal Windows file named oci.dll with two malicious ones—one early in the attack and the other later on. The first imposter file implements WinDivert, a legitimate tool for capturing, modifying, or dropping network packets sent to or from the Windows network stack. The file allows the attackers to download and run malicious code on the infected system. Avast suspects the main purpose of the downloader is to bypass firewalls and network monitoring.
At a later stage in the attack, the intruders replaced the fake oci.dll downloader with code that decrypts a malicious file named SecurityHealthServer.dll and loads it into memory. The functions and flow of this second fake DLL are almost identical to rcview40u.dll, a malicious file that was dropped in espionage-driven supply chain hacks that targeted South Korean organizations in 2018.
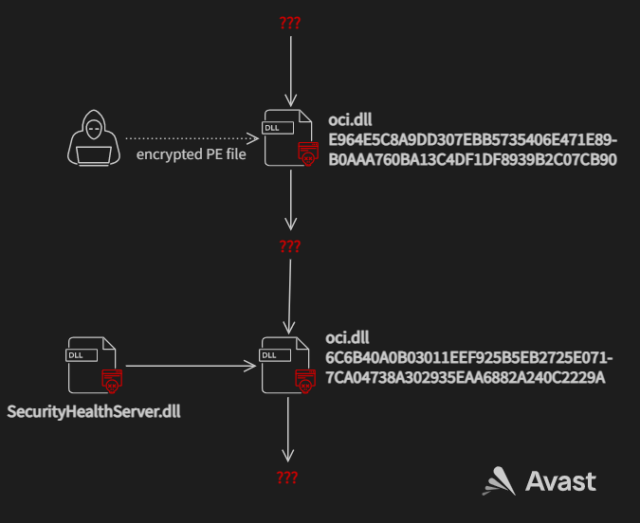
“Because of the similarities between this oci.dll and rcview40u.dll, we believe it is likely that the attacker had access to the source code of the three year-old rcview40u.dll,” Avast researchers wrote. “The newer oci.dll has minor changes like starting the decrypted file in a new thread instead of in a function call which is what rcview40u.dll does. oci.dll was also compiled for x86-64 architecture while rcview40u.dll was only compiled for x86 architecture.”
The net effect of the attack sequence is that the attackers were able to compromise the federal agency network in a way that allowed them to execute code with the same unfettered system rights as the OS and capture any traffic passing into or out of infected machines.
Because officials with the compromised agency didn’t engage with Avast researchers, they can’t be sure precisely what the attackers were doing inside the network. But the implications are clear.
“It is reasonable to presume that some form of data gathering and exfiltration of network traffic happened, but that is informed speculation,” the researchers wrote. “Further because this could have given total visibility of the network and complete control of an infected system it is further reasonable speculation that this could be the first step in a multi-stage attack to penetrate this, or other networks more deeply in a classic APT-type operation.”


No comments:
Post a Comment