More reports from Bleeping Computer ---
Chinese hackers use new Windows malware to backdoor govt, defense orgs
- August 8, 2022
- 09:36 AM
- 0
An extensive series of attacks detected in January used new Windows malware to backdoor government entities and organizations in the defense industry from several countries in Eastern Europe.
Kaspersky linked the campaign with a Chinese APT group tracked as TA428, known for its information theft and espionage focus and attacking organizations in Asia and Eastern Europe [1, 2, 3, 4].
The threat actors successfully compromised the networks of dozens of targets, sometimes even taking control of their entire IT infrastructure by hijacking systems used to manage security solutions.
"The attack targeted industrial plants, design bureaus and research institutes, government agencies, ministries and departments in several East European countries (Belarus, Russia, and Ukraine), as well as Afghanistan," Kaspersky ICS CERT researchers said.
"An analysis of information obtained while investigating the incidents indicates that cyberespionage was the goal of this series of attacks."
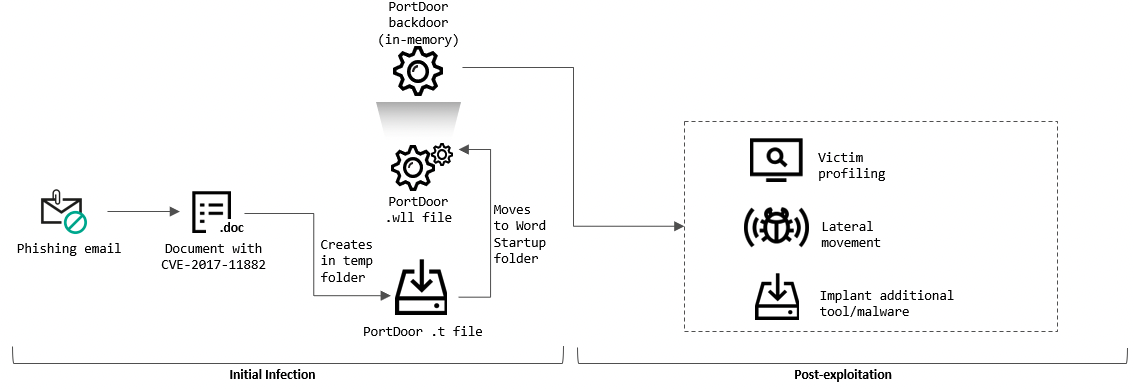
New backdoor deployed for cyberespionage
To achieve their goal, the Chinese cyberspies used spear phishing emails containing confidential information about the targeted organizations and malicious code exploiting the CVE-2017-11882 Microsoft Office vulnerability to deploy PortDoor malware.
PortDoor was also used in spear phishing attacks coordinated by Chinese-backed hackers in April 2021 to hack into the systems of a defense contractor that designs submarines for the Russian Navy.
In the following stages of the attack, the group installed additional malware linked to TA428 in the past (i.e., nccTrojan, Logtu, Cotx, and DNSep), as well as a never before seen malware strain named CotSam.
Like the other families used in this campaign, the new backdoor allows the attackers to collect and steal system information and files from compromised systems.
To deliver CotSam, the attackers went as far as to include a vulnerable version of Microsoft Word together with the payload (Microsoft Word 2007 on 32-bit systems and Microsoft Word 2010 on 64-bit systems).
Stolen data forwarded to Chinese server
After moving laterally through their victims' enterprise networks using tools capable of network scanning, vulnerability search and exploitation, and password attacks like the Ladon hacking utility (popular among Chinese threat actors), they gained domain privileges and harvested confidential files.
Next, they sent them to command-and-control (C2) servers from different countries as encrypted and password-protected ZIP archives.
However, all this stolen data was forwarded by the C2 servers to a second-stage server with a Chinese IP address.
Evidence connecting this campaign to TA428 includes significant overlaps in tactics, techniques, and procedures (TTPs) with the group's previous activity, the same exploit for delivering the initial malware payload used in other attacks against Russian targets, malicious tools commonly used by Chinese threat actors, and dozens of connections to infected systems during Chinese business hours.
Furthermore, the researchers also identified malware and C2 servers previously used in attacks linked by other vendors to this Chinese APT group.
"We believe that the attack series we have identified is an extension of known campaign described in the research of Cybereason, DrWeb, and NTTSecurity," Kaspersky added.
"This is supported by numerous facts and a large amount of evidence we have identified, from the choice of victims to matching CnC servers."


No comments:
Post a Comment