Ready for more...
Hackers selling access to 576 corporate networks for $4 million
Bill Toulas
- October 31, 2022
- 02:45 PM
"A new report shows that hackers are selling access to 576 corporate networks worldwide for a total cumulative sales price of $4,000,000, fueling attacks on the enterprise.
The research comes from Israeli cyber-intelligence firm KELA which published its Q3 2022 ransomware report, reflecting stable activity in the sector of initial access sales but a steep rise in the value of the offerings.
Although the number of sales for network access remained about the same as in the previous two quarters, the cumulative requested price has now reached $4,000,000.
For comparison, the total value of initial access listings in Q2 2022 was $660,000, recording a drop in value that coincided with the summer ransomware hiatus that hurt demand.
The road to ransomware
Initial access brokers (IABs) are hackers who sell access to corporate networks, usually achieved through credential theft, webshells, or exploiting vulnerabilities in publicly exposed hardware.
After establishing a foothold on the network, the threat actors sell this corporate access to other hackers who use it to steal valuable data, deploy ransomware, or conduct other malicious activity.
The reasons IABs choose not to leverage network access vary, ranging from lacking diverse intrusion skills to preferring not to risk increased legal trouble.
IABs still play a crucial role in the ransomware infection chain, even if they got sidelined last year when big ransomware gangs that operated as crime syndicates operated their own IAB departments.
Q3 '22 numbers
In the third quarter of 2022, KELA's analysts observed 110 threat actors posting 576 initial access offerings totaling a cumulative value of $4,000,000.
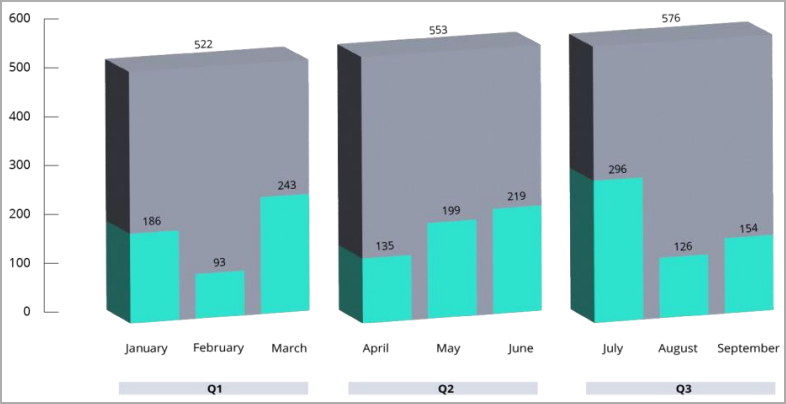
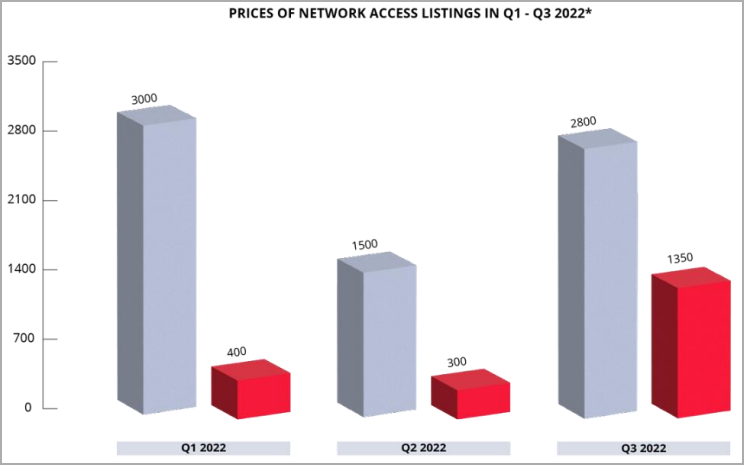
The average selling price of these listings was $2,800, while the median selling price reached a record figure of $1,350.
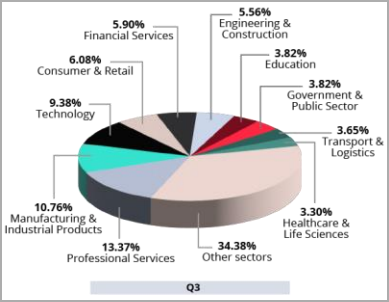
When looking at the targeted sectors, professional services, manufacturing, and technology topped the list with 13.4%, 10.8%, and 9.4%, respectively. Again, ransomware attacks feature a similar ranking, emphasizing the connection between the two.
As initial access brokers have become an integral part of the ransomware attack chain, properly securing your network from intrusion is crucial.
This includes placing remote access servers behind VPNs, restricting access to publicly exposed devices, enabling MFA, and conducting phishing training to prevent the theft of corporate credentials.'
Related Articles:
- LATEST ARTICLES
-
OpenSSL fixes two high severity vulnerabilities, what you need to know
The OpenSSL Project has patched two high-severity security flaws in its open-source cryptographic library used to encrypt communication channels and HTTPS connections.
- NOVEMBER 01, 2022
- 12:39 PM
 0
0
-
New SandStrike spyware infects Android devices via malicious VPN app
Threat actors are using a newly discovered spyware known as SandStrike and delivered via a malicious VPN application to target Persian-speaking Android users.
- NOVEMBER 01, 2022
- 11:29 AM
 0
0
-
Hacking group abuses antivirus software to launch LODEINFO malware
The Chinese Cicada hacking group, tracked as APT10, was observed abusing security software to install a new version of the LODEINFO malware against Japanese organizations.
- OCTOBER 31, 2022
- 11:34 AM
 0
0
-
Instagram confirms outage following stream of user suspensions
Instagram users are currently experiencing issues signing into their accounts, some of them being notified their accounts have been suspended. At the same time, those who manage to log in see that their follower count has dropped.
- OCTOBER 31, 2022
- 11:14 AM
 1
1
-
Chegg sued by FTC after suffering four data breaches within 3 years
The U.S. Federal Trade Commission (FTC) has sued education technology company Chegg after it exposed the sensitive information of tens of millions of customers and employees in four data breaches suffered since 2017.
- OCTOBER 31, 2022
- 02:07 PM
 0
0
-
NSA shares supply chain security tips for software suppliers
NSA, CISA, and the Office of the Director of National Intelligence (ODNI) have shared a new set of suggested practices that software suppliers (vendors) can follow to secure the supply chain.
- OCTOBER 31, 2022
- 12:54 PM
 1
1









No comments:
Post a Comment