FBI seizes stolen credentials market Genesis in Operation Cookie Monster
Ionut Ilascu
- April 4, 2023
- 04:18 PM
- 0

The domains and infrastructure for Genesis Market, one of the most popular marketplaces for stolen credentials of all types, were seized by law enforcement earlier this week as part of Operation Cookie Monster.
The action is an important blow to the cybercriminal world as Genesis was one of the major players offering both consumer and corporate account identities.
Looking for the admins
While authorities have yet to publish press releases about the takedown, accessing the Genesis Market domains shows a banner saying that the FBI has executed a seizure warrant.
It appears that the administrators of the marketplace have not been caught or identified as the FBI is interested in anyone that is in contact with them. Whoever is behind the Genesis Market has kept a low profile for all these years, indicating good operational security knowledge.
source: BleepingComputer
The FBI informs that the action was possible with the support of multiple organizations in the public and private sectors.
“These seizures were possible because of international law enforcement and private sector coordination,” reads the seizure banner, which includes close to two dozen partners.
However, some of the Genesis infrastructure appears to be active still, as the platform's site on the dark web is still reachable.
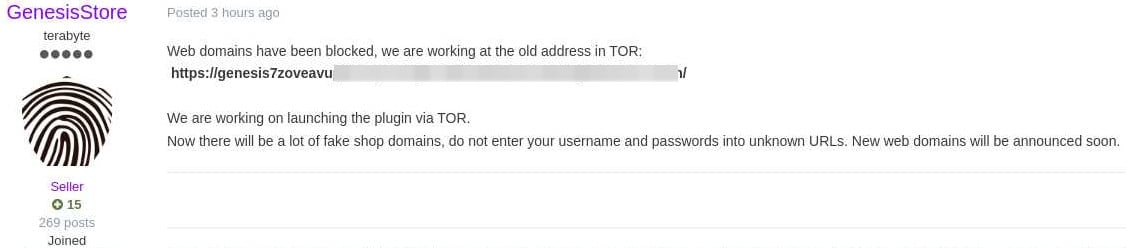
Researchers at ZeroFox say that the platform admins announced recently that the new domains for the marketplace would become available via reputable dark web channels.
Genesis Market operators confirmed that the Tor network domain is active and that they would keep the shop running by launching their plugin via Tor. They also warned of fake domains emerging.
source: Kela
According to ZeroFox, the platform's inventory received new bots since the clear web domains for the market were seized.
Alexander Martin of The Record writes that the Genesis Market takedown prompted a large number of arrests all over the world.
Europol in a press release on Wednesday informed that 119 users of the platform have been arrested, law enforcement carried out searches at 208 properties, and interviewed 97 people.
Genesis, the digital identity market
Genesis Market started in alpha stage in late 2017 and by 2020 it became the most popular online shop for account credentials for various services, device fingerprints, and cookies.
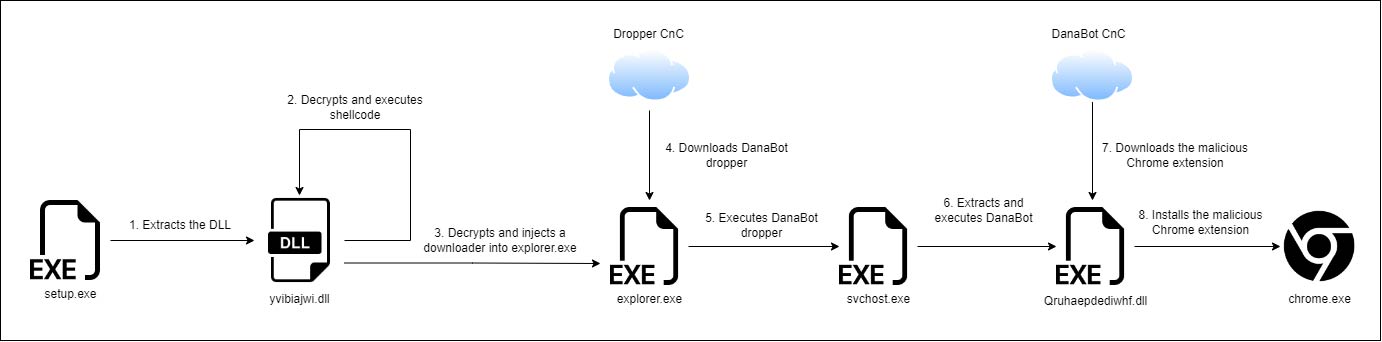
Cybersecurity company Trellix, which assisted law enforcement with the analysis and detection of malicious files used by Genesis Market, says that the operators of the platform used custom JavaScript code dropped on victim machines to collect the logins and fingerprint data (e.g. cookies, IP addresses, time zones, device info) that together composed the digital identity.
The malicious JavaScript was planted on compromised hosts by various info-stealing malware, among them RedLine, DanaBot, Raccoon, AZORult, which provided initial access.
source: Trellix
Their profits came from renting the account identities through bots that provided stolen accounts and sensitive info, complete with the fingerprint data that made the access appear legitimate.
The bot would reside on the compromised computer and send the harvested the information in real time to its buyer.
Depending on the collected information, a bot would cost from $0.70 (consumer accounts) to hundreds of U.S. dollars (access to online banking).
Genesis Market's full database had 1.5 million bots supplying more than 2 million identities; more than 460,000 bots were available for sale at the time of the takedown. In total, the platform offered about 80 million credentials and digital fingerprints, says UK's National Crime Agency.
"The criminals buying these special bots were not only provided with stolen data, but also with the means of using it. Buyers were provided with a custom browser which would mimic the one of their victim. This allowed the criminals to access their victim’s account without triggering any of the security measures from the platform the account was on" - Europol
Genesis Market provided access to a wide list of services with user accounts from all over the world. Among them were Gmail, Facebook, Netflix, Spotify, WordPress, PayPal, Reddit, Amazon, LinkedIn, Cloudflare, Twitter, Zoom, and Ebay.
It appears that customers of the market turned a pretty penny from using the stolen digital identities. Following a raid at a suspected cybercriminal that used Genesis Market, the Romanian Police seized more than $200.000 in cash and over 9 kilograms of pure gold.
According to the Dutch Police, one victim lost almost EUR 70,000 after a Genesis Market customer used his digital identity to make various online purchases. Someone also opened multiple accounts in his name at several banks.
Users that want to check if their accounts were compromised and sold on Genesis Market can check a portal from the Dutch Police specifically built for this purpose.
The FBI did not reply to a request for comment from BleepingComputer.
Update [April 5]: Article updated with information from law enforcement agencies available after publishing time
GENESIS MARKET SHUTDOWN —
Operation Cookie Monster: Feds seize “notorious hacker marketplace”
Genesis Market sold user data and a tool that mimics each victim's web browser.
An international law enforcement operation shut down a "notorious hacker marketplace" that sold access to infected devices and stolen account credentials, the US Department of Justice and Europol announced today. The operation targeting Genesis Market involved 17 countries, seized the platform's infrastructure, and resulted in "119 arrests, 208 property searches, and 97 knock-and-talk measures," Europol said.
The now-shuttered Genesis Market "advertised and sold packages of account access credentials—such as usernames and passwords for email, bank accounts, and social media—that had been stolen from malware-infected computers around the world," the Justice Department said. The so-called "Operation Cookie Monster" seized 11 domain names pursuant to a warrant authorized by the US District Court for the Eastern District of Wisconsin.
While Genesis Market's public website was taken down, its .onion domain was still accessible on the dark web using Tor today. Law enforcement is apparently still looking for at least some of the people behind the platform, as the domain seizure message seeks tips from anyone who has been in contact with Genesis Market administrators. The US Treasury Department said Genesis Market "is believed to be located in Russia."
Europol said that "unlike other criminal marketplaces, Genesis Market was accessible on the open web, although obscured from law enforcement behind an invitation-only veil. Its accessibility and cheap prices greatly lowered the barrier of entry for buyers, making it a popular resource among hackers."
Genesis Market reportedly had about 59,000 registered users. According to Europol, the market's "main criminal commodity was digital identities" or "what the market owners referred to as 'bots' that had infected victims' devices through malware or account takeovers."
Operation Cookie Monster was led by the FBI and Dutch National Police, with coordination by Europol.
“Custom browser” mimicked victims’ devices
Genesis Market emerged in March 2018 and since then "has offered access to data stolen from over 1.5 million compromised computers around the world containing over 80 million account access credentials," the Justice Department said.
Upon purchasing a bot from Genesis Market, "criminals would get access to all the data harvested by it such as fingerprints, cookies, saved logins and autofill form data," Europol said. The cheapest bots sold for less than a dollar each, but others fetched hundreds of dollars and provided access to online banking accounts.
Europol said that Genesis Market shoppers were "provided with a custom browser which would mimic the one of their victim," letting them access victims' accounts "without triggering any of the security measures from the platform the account was on. These security measures include recognizing a different log-in location, a different browser fingerprint or a different operating system."
A Brian Krebs report described the Genesis offering as "a custom Web browser plugin which can load a Genesis bot profile so that the browser mimics virtually every important aspect of the victim's device, from screen size and refresh rate to the unique user agent string tied to the victim's web browser."
The DOJ said it accessed Genesis Market's user database. "The database contained the purchase and activity history on all users, which the feds say helped them uncover the true identities of many users," Krebs wrote.
Three big takedowns in the past year
The Genesis Market takedown follows similar actions against Hydra Market in April 2022 and BreachForums in March 2023. The DOJ claims it has "dismantled the darknet's largest marketplaces" due to those three operations over the last year.
The Justice Department said victim credentials obtained during Operation Cookie Monster were provided to HaveIBeenPwned.com, which helps you check whether you've been involved in a data breach.
The Treasury Office of Foreign Assets Control (OFAC) said it designated Genesis Market, meaning that "all property and interests in property of the entity that are in the United States or in the possession or control of US persons must be blocked and reported to OFAC." Additionally, anyone who "engage[s] in certain transactions with the entity designated today may themselves be exposed to sanctions."


No comments:
Post a Comment