While most of the targeted employees ignored the phishing text message,
one clicked the embedded phishing link that redirected to a fake login
portal with a multi-factor authentication (MFA) form. After signing in, the attacker deepfaked an employee's voice and called
the targeted IT team member, tricking them into providing an additional
MFA code, which allowed the addition of an attacker-controlled device to
the targeted employee's Okta account.
Retool blames breach on Google Authenticator MFA cloud sync feature

Software company Retool says the accounts of 27 cloud customers were compromised following a targeted and multi-stage social engineering attack.
Retool's development platform is used to build business software by companies ranging from startups to Fortune 500 enterprises, including Amazon, Mercedes-Benz, DoorDash, NBC, Stripe, and Lyft.
✓ Snir Kodesh, Retool's head of engineering, revealed that all hijacked accounts belong to customers in the cryptocurrency industry.
The breach occurred on August 27, after the attackers bypassed multiple security controls using SMS phishing and social engineering to compromise an IT employee's Okta account.
The attack used a URL impersonating Retool's internal identity portal and was launched during a previously announced migration of logins to Okta.
While most of the targeted employees ignored the phishing text message, one clicked the embedded phishing link that redirected to a fake login portal with a multi-factor authentication (MFA) form.
After signing in, the attacker deepfaked an employee's voice and called the targeted IT team member, tricking them into providing an additional MFA code, which allowed the addition of an attacker-controlled device to the targeted employee's Okta account.
Hack blamed on new Google Authenticator sync feature
Retool is blaming the success of the hack on a new feature in Google Authenticator that allows users to synchronize their 2FA codes with their Google account.
This has been a long-requested feature, as you can now use your Google Authenticator 2FA codes on multiple devices, as long as they are all logged into the same account.
However, Retool says that the feature is also to blame for the August breach severity as it allowed the hacker who successfully phished an employee's Google account access to all their 2FA codes used for internal services.
"With these codes (and the Okta session), the attacker gained access to our VPN, and crucially, our internal admin systems," Kodesh said.
"This allowed them to run an account takeover attack on a specific set of customers (all in the crypto industry). (They changed emails for users and reset passwords.) After taking over their accounts, the attacker poked around some of the Retool apps."
✓ As Kodesh explained, while, initially, Retool had enabled MFA, the auth codes synced by Google Authenticator to the cloud led to an inadvertent transition to single-factor authentication.
This shift occurred as control over the Okta account translated into control over the Google account, granting access to all One-Time Passwords (OTPs) stored within Google Authenticator.
"We strongly believe that Google should either eliminate their dark patterns in Google Authenticator (which encourages the saving of MFA codes in the cloud), or at least provide organizations with the ability to disable it."
While Google Authenticator does promote its cloud sync feature, it is not required. If you have enabled the feature, you can deactivate it by clicking on the account circle at the top right of the app and selecting 'Use Authenticator without an account.' This will log you out of the app and delete your synchronized 2FA codes in your Google account.
"Our first priority is the safety and security of all online users, whether consumer or enterprise, and this event is another example of why we remain dedicated to improving our authentication technologies. Beyond this, we also continue to encourage the move toward safer authentication technologies as a whole, such as passkeys, which are phishing resistant," a Google spokesperson told BleepingComputer.
✓ Google also recommended migrating to FIDO-based tech from legacy one-time password (OTP) multi-factor authentication as a simple way to thwart similar attacks.
"Phishing and social engineering risks with legacy authentication technologies, like ones based on OTP, are why the industry is heavily investing in these FIDO-based technologies," the Google spokesperson said.
"While we continue to work toward these changes, we want to ensure Google Authenticator users know they have a choice whether to sync their OTPs to their Google Account, or to keep them stored only locally. In the meantime, we'll continue to work on balancing security with usability as we consider future improvements to Google Authenticator."
No on-premise Retool customers breached
After discovering the security incident, Retool revoked all internal employee authenticated sessions, including those for Okta and G Suite.
✓ It also restricted access to all 27 compromised accounts and notified all affected cloud customers, restoring all hijacked accounts to their original configurations (no on-premise customers were impacted in the incident, according to Retool).
"This meant that although an attacker had access to Retool cloud, there was nothing they could do to affect on-premise customers," Kodesh said.
"It's worth noting that the vast majority of our crypto and larger customers in particular use Retool on-premise."
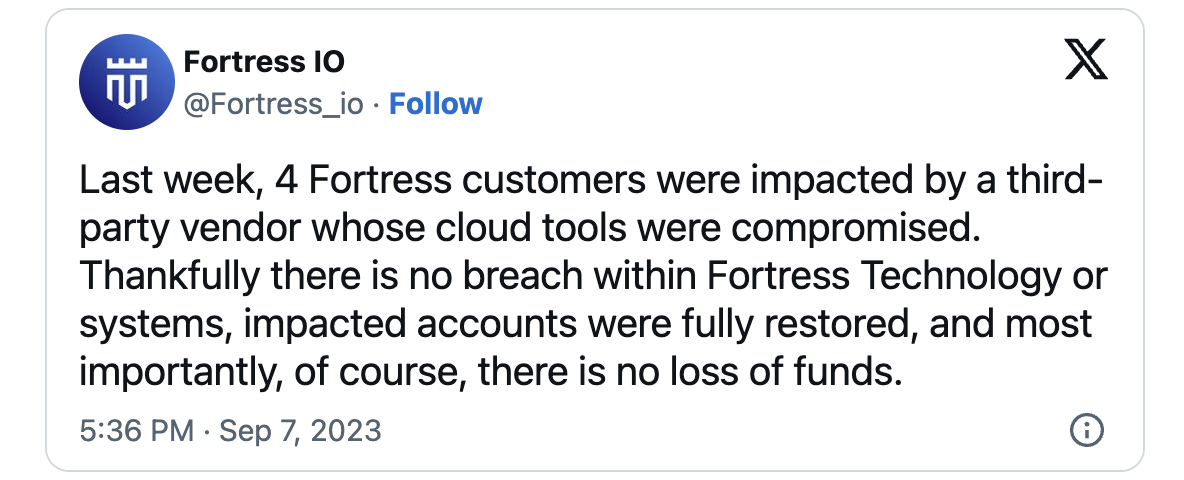
✓ A Coindesk report linked the Retool breach to the theft of $15 million from Fortress Trust in early September.
Retool's development platform is used to build business software by companies ranging from startups to Fortune 500 enterprises, including Amazon, Mercedes-Benz, DoorDash, NBC, Stripe, and Lyft.
Threat actors increasingly use social engineering attacks targeting IT service desks or support personnel to gain initial access to corporate networks.
The list of companies that got hacked using this tactic includes Cisco, Uber, 2K Games, and, more recently, MGM Resorts.
In late August, Okta alerted customers of networks being breached via companies' IT service desks after hackers reset Multi-Factor Authentication (MFA) defenses for Super Administrator or Org Administrator accounts.
✓✓ U.S. Federal Agencies also warned this week of the cybersecurity risks behind attackers using deepfakes. They recommended using tech that can help detect deepfakes used to gain access to their networks, communications, and sensitive information following successful social engineering attacks.
Update: Added Google statement.


No comments:
Post a Comment