The malware was discovered by risk management firm Stroz Friedberg, an Aon Insurance company, and enables its operators to create reverse shells for remote access and to further the the attack.
By Bill Toulas
August 24, 2024
10:36 AM

The malware was discovered by risk management firm Stroz Friedberg, an Aon Insurance company, and enables its operators to create reverse shells for remote access and to further the the attack.
"At the time of this writing, the persistence technique used (udev rules) is not documented by MITRE ATT&CK," the researchers note, highlighting that sedexp is an advanced threat that hides in plain site.
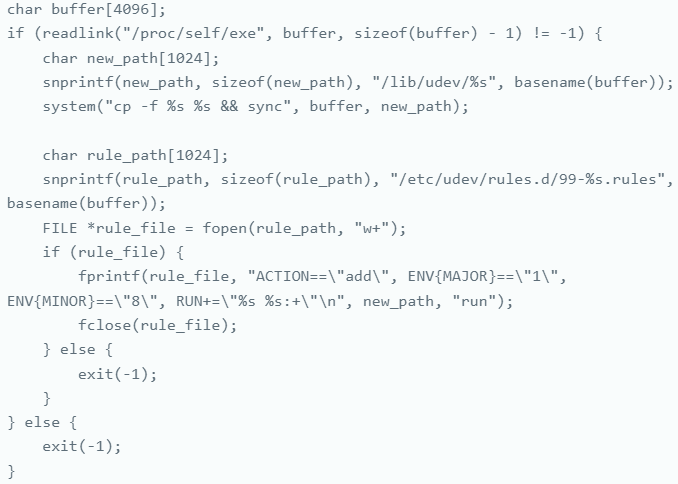
Persisting via udev rulesNode files are dynamically created and removed when the user connects/disconnects devices, while udev also handles the loading of appropriate drivers.
Udev rules are text configuration files that dictate how the manager should handle certain devices or events, located in '/etc/udev/rules.d/' or '/lib/udev/rules.d/.'
These rules contain three parameters that specify its applicability (ACTION== "add"), the device name (KERNEL== "sdb1"), and what script to run when the specified conditions are met (RUN+="/path/to/script").
ACTION=="add", ENV{MAJOR}=="1", ENV{MINOR}=="8", RUN+="asedexpb run:+"
The final rule component (RUN+= "asedexpb run:+") executes the malware's script 'asedexpb,' so by setting /dev/random as a precondition, the attackers ensure the malware is run frequently.
Most importantly, /dev/random is an essential system component on Linux that security solutions do not monitor. Hence, its abuse guarantees evasion for the malware.
Source: Aon
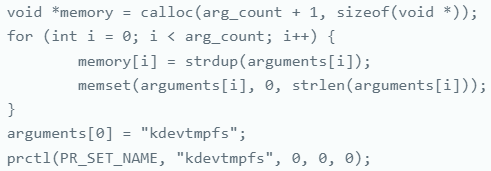
Primary operational capabilities
The malware names its process' kdevtmpfs,' which mimics a legitimate system process, further blending in with normal activities and making it harder to detect using conventional methods.
Source: Aon
Sedexp also employs memory manipulation techniques to hide any file containing the string "sedexp" from standard commands like 'ls' or 'find,' concealing its presence on the system.
It can also modify memory contents to inject malicious code or alter the behavior of existing apps and system processes.
- The researchers mention that the malware has been used in the wild since at least 2022. They found it present in many online sandboxes and without being detected (on VirusTotal only two antivirus engines flag as malicious the three sedexp samples available in the report).
-
Hackers now use AppDomain Injection to drop CobaltStrike beacons
A wave of attacks that started in July 2024 rely on a less common technique called AppDomain Manager Injection, which can weaponize any Microsoft .NET application on Windows.
- August 23, 2024
- 12:31 PM
 0
0
-
US oil giant Halliburton confirms cyberattack behind systems shutdown
Halliburton, one of the world's largest providers of services to the energy industry, has confirmed a cyberattack that forced it to shut down some of its systems earlier this week.
- August 23, 2024
- 12:01 PM
 2
2
-
Russian laundering millions for Lazarus hackers arrested in Argentina
The federal police in Argentina (PFA) have arrested a 29-year-old Russian national in Buenos Aires, who is facing money laundering charges related to cryptocurrency proceeds of the notorious North Korean hackers' Lazarus Group.'
- August 23, 2024
- 09:59 AM
 0
0




No comments:
Post a Comment